0%
Ever stop and think about who you’re really trusting when you run npm install?
Here’s the uncomfortable truth: NPM supply chain attacks don’t hit your app directly. They hit the packages your app depends on — the same ones thousands of developers rely on. One compromised package can ripple through the ecosystem, affecting countless downstream projects.
The NPM registry is the world’s biggest JavaScript playground. One poisoned package can spread like wildfire. Take event-stream: downloaded 1.5 million times weekly, used by 1,600 other packages. Then boom — compromised.
Attackers have a playbook: typosquatting, creating packages that look legit but aren’t; slopsquatting, exploiting AI-generated code suggestions; account takeovers via fake support emails; and hijacking expired domains to reset passwords.
September 2025 brought the Shai-Hulud attack — over 500 packages infected, hunting GitHub tokens and cloud API keys. Recent attacks hit 18 major packages with 2.6 billion weekly downloads. Trust is the weapon. Open source’s greatest strength becomes its biggest weakness.
Your dependencies aren’t just code. They’re trust — and right now, that trust is being systematically exploited.
An NPM supply chain attack happens when malicious actors slip harmful code into packages you rely on. Not your own code — the dependencies your app installs, often automatically. That’s what makes them dangerous: the attack spreads silently across thousands of projects.
It’s a clever exploitation of trust. Developers expect packages in the NPM registry to be safe. Attackers weaponize that trust. A single poisoned package can cascade downstream, affecting countless applications.
Methods vary. Typosquatting tricks developers into installing similarly named packages. Slopsquatting leverages AI-generated suggestions. Account takeovers let attackers push malicious updates. Even expired domains can be hijacked to seize maintainer privileges.
Real-world attacks illustrate the stakes. event-stream, the Shai-Hulud worm, and recent multi-package compromises show how one compromised maintainer account can wreak havoc across the ecosystem.
At its core, an NPM supply chain attack is a trust-based attack, targeting the very dependencies developers rely on to build software securely. Understanding it is the first step to preventing it.
You want to know how these attacks actually happen? Let’s break it down.
These aren’t random script kiddies doing drive‑by exploits. These are calculated moves that weaponize the very thing that makes the npm ecosystem powerful—its massive, interconnected dependency graph.
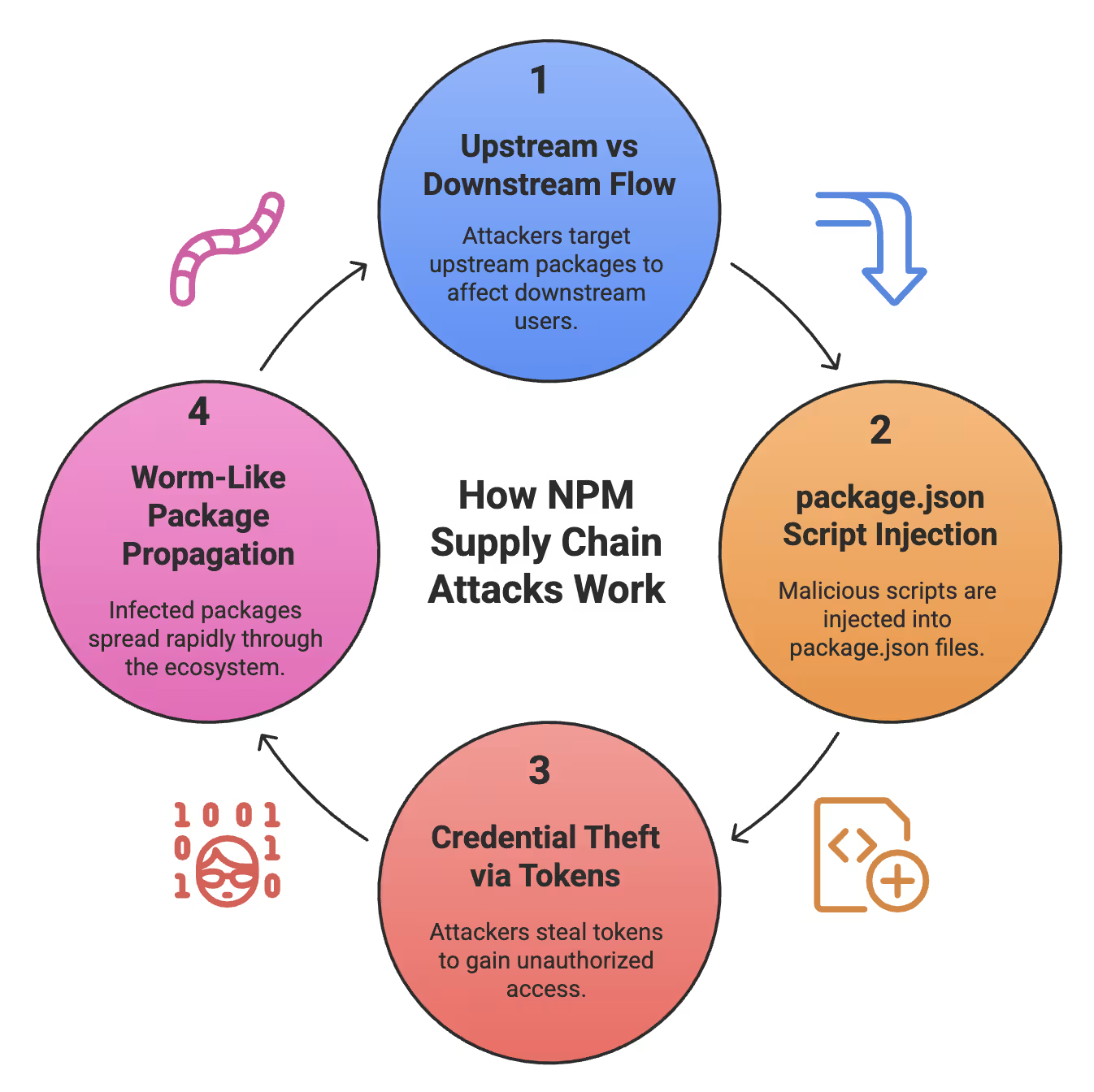
How NPM Supply Chain Attacks Work
Modern attackers don’t waste time breaching individual applications. That’s slow, manual, and noisy.
So they go upstream—where the real leverage lives. One trusted maintainer. One popular package. One stolen registry credential. Poison the source, and every downstream project inherits the compromise automatically.
And downstream? That’s where the damage detonates. Thousands of apps, CI pipelines, and production environments blindly pull poisoned updates—turning one upstream breach into a full-scale downstream cascade.
The September 2025 attack proved exactly how catastrophic this model is. A single compromised maintainer account rippled into 18 high-profile packages. Overnight, 2.6 billion weekly downloads were exposed. One upstream breach. A downstream blast radius the size of the ecosystem.
Attackers don’t need to rewrite codebases. They just tweak package.json.
One malicious preinstall or postinstall script is all it takes:
Shai‑Hulud abused this perfectly—burying malicious logic inside a bloated bundle.js triggered on install. Newer attacks masquerade as “helpful utilities” like Bun installers, making the payload look like normal tooling.
Your system runs their code because you trust the package. That’s the whole game.
Once their script runs, the real extraction begins. Attackers know exactly what to target:
Some attackers bundle scanners like TruffleHog to hunt your cloud credentials. They turn your own security tools into reconnaissance.
The scariest part? These attacks don’t stop at compromise—they spread.
Shai‑Hulud showed what automated propagation looks like:
One infected package becomes hundreds in hours. It’s not just an attack—it’s automated digital reproduction.
And once it starts, no human needs to be involved. That’s what makes modern NPM supply chain attacks so dangerous.
These aren't hypothetical scenarios. They're war stories. Real attacks that happened to real developers, with real consequences.
September 2025. The month that changed everything.
The Shai-Hulud worm wasn't just another attack—it was a digital pandemic:
This thing spread faster than gossip in a startup.
January to April 2021. Two months of silent data theft.
Attackers found a crack in Codecov's Docker setup and squeezed right through:
Your build pipeline thought it was uploading test results. It was actually broadcasting your secrets to strangers.
The attack that made cybersecurity experts lose sleep.
This wasn't just sophisticated—it was surgical:
When your security vendor gets hacked, who do you trust?
December 2022. Package managers played favorites with public repos.
The attack was elegant in its simplicity:
Package managers trusted public repos over private ones. Attackers knew this. Developers paid the price.
Each of these attacks shares one thing: they turned trust into a weapon. Dependencies, tools, workflows—all became attack vectors.
Alright, enough scary stories. Time to armor up.
Protecting yourself from npm supply chain attacks isn’t rocket science—but it’s no longer optional. These aren’t “nice to have” measures—they’re survival tactics.
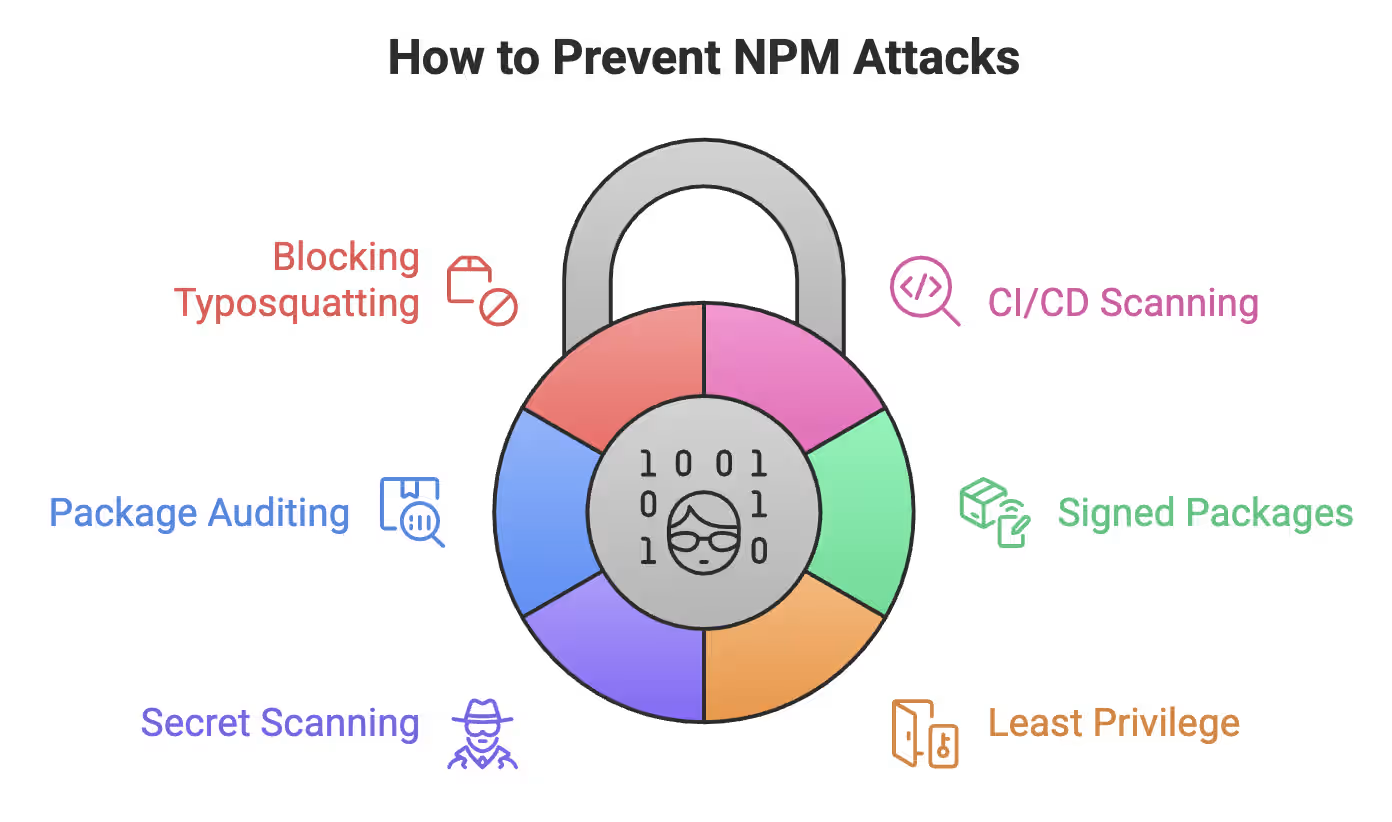
How to prevent NPM Attacks
Think of your CI/CD pipeline as your bouncer. It shouldn’t just watch—you want it stopping trouble before it enters:
Package signatures aren’t just crypto fluff—they prove authenticity:
Your npm account is a gateway. Treat it like one:
Attackers love finding API keys before you know they’re exposed:
That shiny new release? Give it a moment:
Generative AI introduces new risks:
You can’t prevent every attack—but you can make yourself a much harder target. Honestly? That’s usually enough to keep attackers sweating and your dependencies safer.
Security experts aren’t losing sleep over isolated attacks anymore—they’re watching open source get weaponized. This isn’t about a single breach. It’s an ecosystem-wide problem.
Open source supply chain attacks have surged 742% per year. That’s not growth. That’s an epidemic.
And here’s the kicker:
What changed? Attackers aren’t just stealing credentials anymore. They’re building self-replicating malware networks. They’re not raiding houses—they’re conquering neighborhoods.
Thought AI would make coding safer? Plot twist: it’s creating new attack vectors.
Researchers analyzing AI-generated code found:
Think about it: AI suggests a package that doesn’t exist. Developer trusts it. Attacker registers it. Game over.
We’ve built a feedback loop. Our own tools are now inventing attack vectors for us—suggesting packages that never existed, trusting them blindly, and leaving the ecosystem wide open.
GitHub isn’t just a code host—it’s now the central nervous system of supply chain attacks. Compromised tokens become credential dropboxes, as Shai-Hulud proved. Vulnerable GitHub Actions workflows provide easy entry points, and long-lived tokens act as skeleton keys, unlocking entire ecosystems. The line between app security and supply chain security has disappeared.
Attackers are weaponizing the very trust that drives open-source collaboration. The real question isn’t whether your dependencies are safe—it’s how long before they aren’t, and how quickly a single compromise can cascade through thousands of projects.
We’ve covered a lot, and if it feels overwhelming, that’s understandable. The numbers tell the story: attacks are up 742% annually, and malicious packages linger undetected for 209 days on average. This isn’t a distant threat — it’s in your dependency tree now.
Security isn’t optional anymore. Multi-layered defenses — dependency scanning, signed packages, least privilege access — are the minimum standard. AI adds another wrinkle: generative tools speed development but can introduce non-existent or malicious packages, creating new attack vectors.
The Shai-Hulud attack showed how quickly trust can be weaponized at scale. Open source built the modern internet, and it remains one of our greatest strengths. We just need smarter ways to protect it.
No strategy is perfect. But verifying dependencies, auditing packages, and enforcing strict controls will significantly reduce your risk. Your code is only as secure as its weakest dependency. Not a catchy phrase — the reality. The question isn’t if a supply chain attack will happen, but whether you’ll be ready when it does.

Senior Security Consultant