0%
Ever wondered why most businesses hide the fact that they're not SOC 2 compliant? Because they have something to hide.
Data breaches in the US skyrocketed by almost 40% in Q2 2021. Yup, you read that right. And guess what happens when your customer data gets leaked? Millions down the drain. Trust shattered. Reputation in tatters. We've seen it happen time and again.
So what’s this SOC 2 thing everyone’s buzzing about? It’s a security framework from the AICPA that shows you know how to protect customer data from hackers and all the scary stuff. It’s not legally required—but guess what? Big clients won’t even look your way without it.
Getting SOC 2 compliant takes 6 to 12 months. Yeah, it’s a process—but in today’s “prove your security” world, it’s a serious game-changer.
This guide breaks it all down: the five Trust Services Criteria (we’ll explain), how to survive your first audit, and the difference between Type 1 and Type 2. No BS. No jargon. Just the straight-up truth about SOC 2—because when it comes to data security, we’ve got #nothingtohide.
SOC 2 Compliance Requirements
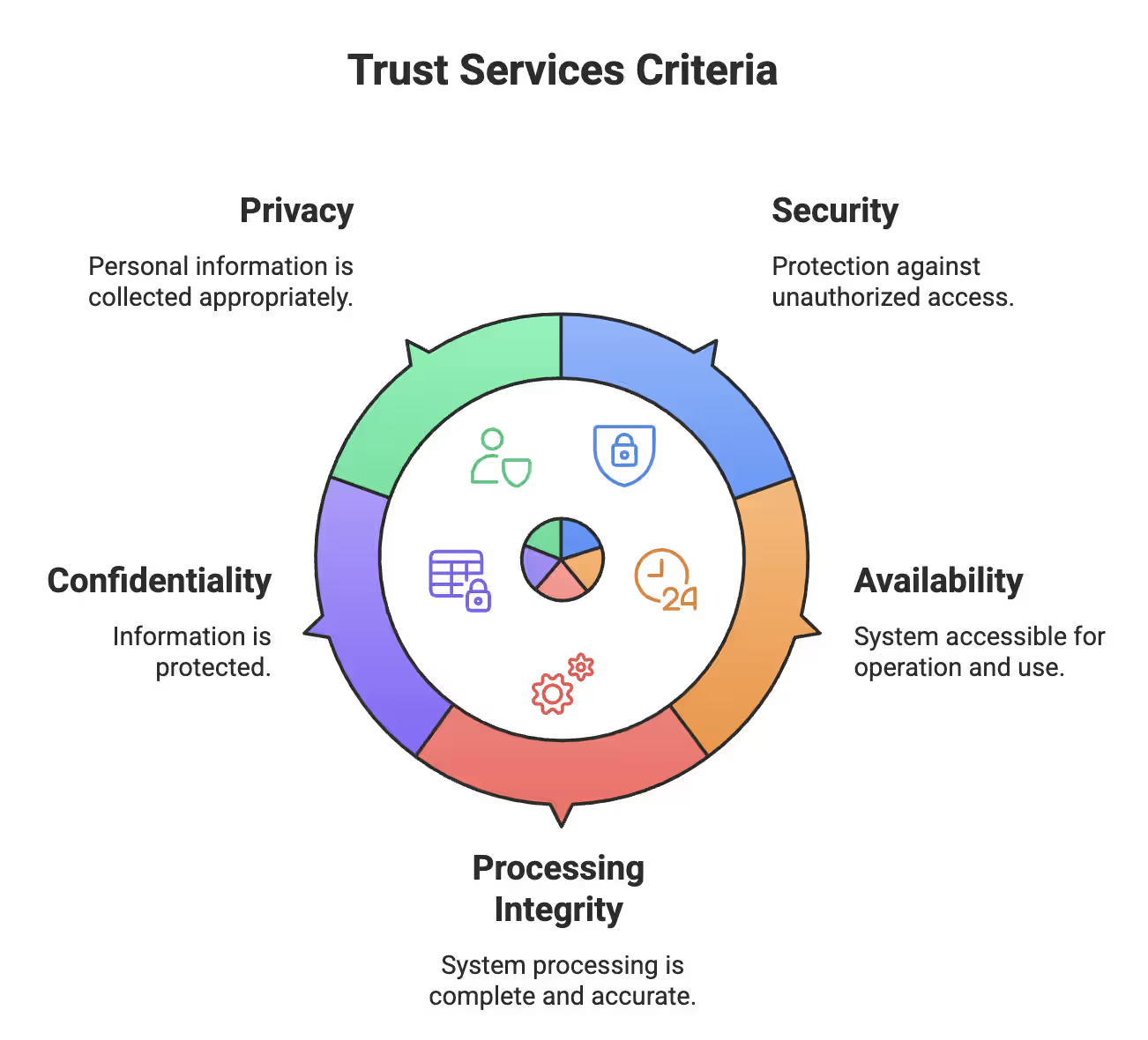
Let's cut to the chase. SOC 2 compliance isn't built on some mysterious, impossible-to-understand framework. It's actually based on something called the Trust Services Criteria (TSC). Think of it as the backbone that shows how well your organization is protecting sensitive information.
Unlike other security frameworks that force you into rigid checklists, SOC 2 gives you breathing room. It's flexible, while still making sure you're actually secure—not just pretending to be.
The American Institute of Certified Public Accountants (AICPA) created five criteria that form the heart of SOC 2. Here's what they really mean:
Each criterion comes with specific "points of focus" to guide you. For example, the Security criterion includes things like access management and system monitoring.
Here's some good news—only the Security criterion (also called Common Criteria) is actually required for SOC 2 certification. The other four? Totally optional. Pick the ones that make sense for your business.
Why is Security the only must-have? Because it's the foundation everything else stands on. This single criterion contains nine categories of controls, covering everything from how your organization is structured to how you secure endpoints and manage risks.
Be smart about which optional criteria you include. If you're handling healthcare data, the Privacy criterion becomes pretty darn important. Working in financial services? Processing Integrity should be your best friend to ensure accurate transactions.
About 70% of companies start with just the Security criterion for their first SOC 2 audit. Smart move. Get your security foundation solid before trying to do everything at once.
Want proof that SOC 2 matters? Look at these disasters:
In 2023, Okta got hammered when hackers stole HTTP access tokens from their support platform. Big names like Caesars Entertainment and MGM Resorts were affected. If they'd properly implemented the Security criterion's access controls, this mess might never have happened.
Then there's AT&T. They faced a massive data breach affecting 8.9 million wireless customers when a cloud vendor messed up with account details. The price tag? $13 million to settle an FCC investigation. A solid vendor security assessment—which SOC 2 requires—could have saved them.
The 2023 MOVEit vulnerability might be the scariest. It hit over 2,500 organizations worldwide, including the BBC and British Airways. This breach showed what happens when you don't properly assess third-party tech—exactly what SOC 2's risk management controls are designed to prevent.
Here's the truth—just having a SOC 2 report isn't enough. Companies with "checkbox compliance" are still vulnerable. Real security comes from actually implementing the controls, not just going through the motions.
Research shows that companies with solid SOC 2 compliance detect potential security incidents 65% faster than those without. In today's world of constant attacks, that's not just nice to have—it's essential.
Most auditors will make SOC 2 sound like some mystical process that only they understand. Why? Because they're selling you something.
Let me pull back the curtain on what really happens during a SOC 2 audit. I've guided companies through this journey countless times, and I'll tell you straight – knowing what's coming is the difference between smooth sailing and a total nightmare.
You've got two options, and companies love hiding which one you actually need:
SOC 2 Type I is basically a security snapshot. It checks if your controls look good on paper at a single moment in time. Quick and easy – often done within a month. The fast food of compliance.
SOC 2 Type II is the real deal. It watches how your controls actually perform over 3-12 months. This shows clients you're not just talking the talk, but walking the walk.
Here's what they don't tell you: about 70% of first-timers go for Type I, but many customers now straight-up reject these reports. They can smell the half-measures. Most clients expect you to get a Type II within a year anyway, so why waste time?
Your SOC 2 journey breaks down into three phases that nobody warns you about:
Pre-audit phase (2 weeks to 9 months): This is where you figure out what you're missing and fix it. First-timers, brace yourselves – you'll spend about eight hours every week for two months just getting ready.
Audit window (Type II only): This is your 3-12 month observation period. The AICPA says 6 months minimum, and they're not kidding.
Formal audit phase (1-3 months): When your auditor starts digging through everything. You'll answer about 100 evidence requests. Fun times!
Bottom line: Type I can be knocked out in under 4 months. Type II? You're looking at 9-12 months from start to finish.
The cost of SOC 2 certification isn't what most vendors advertise. Let's get real:
Audit type: Type I audits run $7,500-$15,000 for mid-sized companies and up to $60,000 for larger ones. Type II audits run $12,000-$20,000 for mid-sized companies and can hit $100,000 for the big players.
The hidden costs they never mention:
One company tallied their total first-time SOC 2 bill at $147,000. That's the whole truth that nobody's telling you.
But here's a secret – automation tools can slash your timeline from months to weeks. Many companies cut their audit time in half and save 25-50% on overall costs with the right automated solutions.
With data breaches up 68% in recent years and partners demanding SOC 2 reports before signing deals, the question isn't if you can afford to get certified – it's if you can afford not to.
Real food for thought, isn't it?
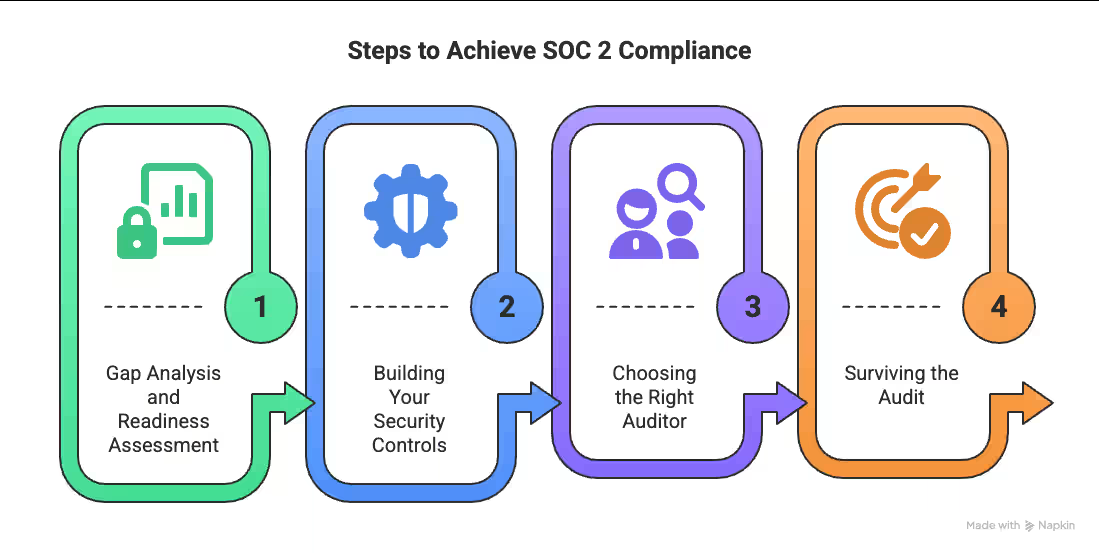
Want to know a secret? Getting SOC 2 compliance doesn't have to be the nightmare everyone makes it out to be. After helping dozens of companies through this process, I've figured out that success depends on having a straightforward, step-by-step approach. Yes, it's complex. But with the right strategy? Totally doable.
Steps to Achieve SOC 2 Compliance
First things first - get a proper readiness assessment. Trust me, this saves you massive headaches down the road. It's the difference between a smooth audit and pulling your hair out later.
A professional SOC 2 readiness assessment costs between $10,000-$17,000. Expensive? Maybe. Worth it? Absolutely. It's like getting a practice run before the real thing.
During this assessment, you'll:
Here's the deal - companies that do this step are way less likely to get nasty surprises during the actual audit. It's not required, but skipping it is like jumping out of a plane without checking your parachute first.
Other frameworks give you strict checklists. SOC 2 is different. You get flexibility in how you meet the requirements. That's good and bad. Good because you can tailor it to your business. Bad because... where do you even start?
Focus on these areas that most people mess up:
The big mistake? Treating SOC 2 like a checkbox exercise. The core of SOC 2 includes over 30 required controls within the security criteria. But they're not just hoops to jump through - they actually protect your business from the bad guys.
This is a relationship, not a transaction. Interview at least three potential auditors. And yes, they MUST be affiliated with AICPA or be a certified CPA firm - nobody else can perform these audits.
When picking your auditor, ask yourself:
A great auditor is a partner, not just someone checking boxes. They'll help you spot things you missed and improve your security storytelling. Pick someone you actually like - you'll be spending a lot of time together.
Once the audit starts, be ready for the evidence avalanche. Most companies handle about 100 evidence requests during the formal audit phase. That's a lot of screenshots and policy docs!
To make this less painful:
Automation isn't just nice-to-have - it's a game-changer. Companies using compliance automation tools often finish audits in half the time and save 25-50% on costs.
Remember this: SOC 2 isn't a one-and-done deal. It's ongoing. Build good habits from day one, and you won't be scrambling every year when audit time comes around.
The whole truth? SOC 2 is a journey, not a destination. But with these steps, at least it won't be a journey through hell.
Let's get real for a second. SOC 2 certification isn't just another security checkbox – it's a serious business driver. The numbers don't lie, and they're screaming that companies with solid security credentials are winning bigger deals and growing faster than their competitors.
Want to know a dirty little secret about the SaaS world? SOC 2 compliance has become the price of entry if you're looking to scale. Here's the naked truth:
Surprised? Here's something that'll really shock you: 34% of massive enterprises (we're talking $1 billion+ revenue) say increasing revenue and winning new clients is the main reason they got compliant. Not security. Not data protection. Cold, hard cash.
Why? Because a current SOC 2 report removes the "but are you secure?" roadblock from sales conversations. It's like having an express pass at the security-conscious customer theme park. No lines, no waiting, just deals closing faster.
So SOC 2 opens doors. But it does way more than that:
First, it builds trust like nothing else. When an independent auditor verifies you're not playing fast and loose with customer data, people take notice. Especially when you're handling the sensitive stuff – payment details, health records, or personal data.
In crowded markets, SOC 2 helps you stand out like a secure lighthouse in a sea of security-questionable competitors. This becomes even more valuable when chasing big fish – many enterprise clients and government entities flat-out require SOC 2 compliance before they'll even consider you.
But here's the real kicker – it future-proofs your business. As security standards keep rising (and trust us, they will), companies with mature compliance programs can adapt quickly while their competitors scramble to catch up.
Let's look at who's cleaning up with their SOC 2 certification:
Vonage – you know, the cloud communications giant – got their SOC 2 Type II certification for Network APIs before anyone else in their space. Smart move considering 44% of their target industries reported payment fraud increases. They didn't just get compliant; they turned compliance into a competitive edge.
MindBridge, that AI financial risk platform, did the same thing. Their Type 2 SOC 2 audit completion wasn't just a security win – it was a credibility booster in the financial sector, where data security isn't just important, it's everything.
The pattern keeps repeating across industries. From legal software to cybersecurity services – companies investing in SOC 2 consistently report stronger relationships, faster sales cycles, and better market positioning.
It's simple: in a world where data breaches make headlines daily, having #nothingtohide becomes your secret weapon.
Ready to start your SOC 2 journey? Good. Because waiting is literally killing your deals.
Let's be brutally honest about what happens when you keep putting off SOC 2 certification:
But here's the real kicker – the longer you wait, the more it costs. Why? Because retrofitting security controls into your growing business is like trying to add seatbelts to a car that's already speeding down the highway. Messy, expensive, and dangerous.
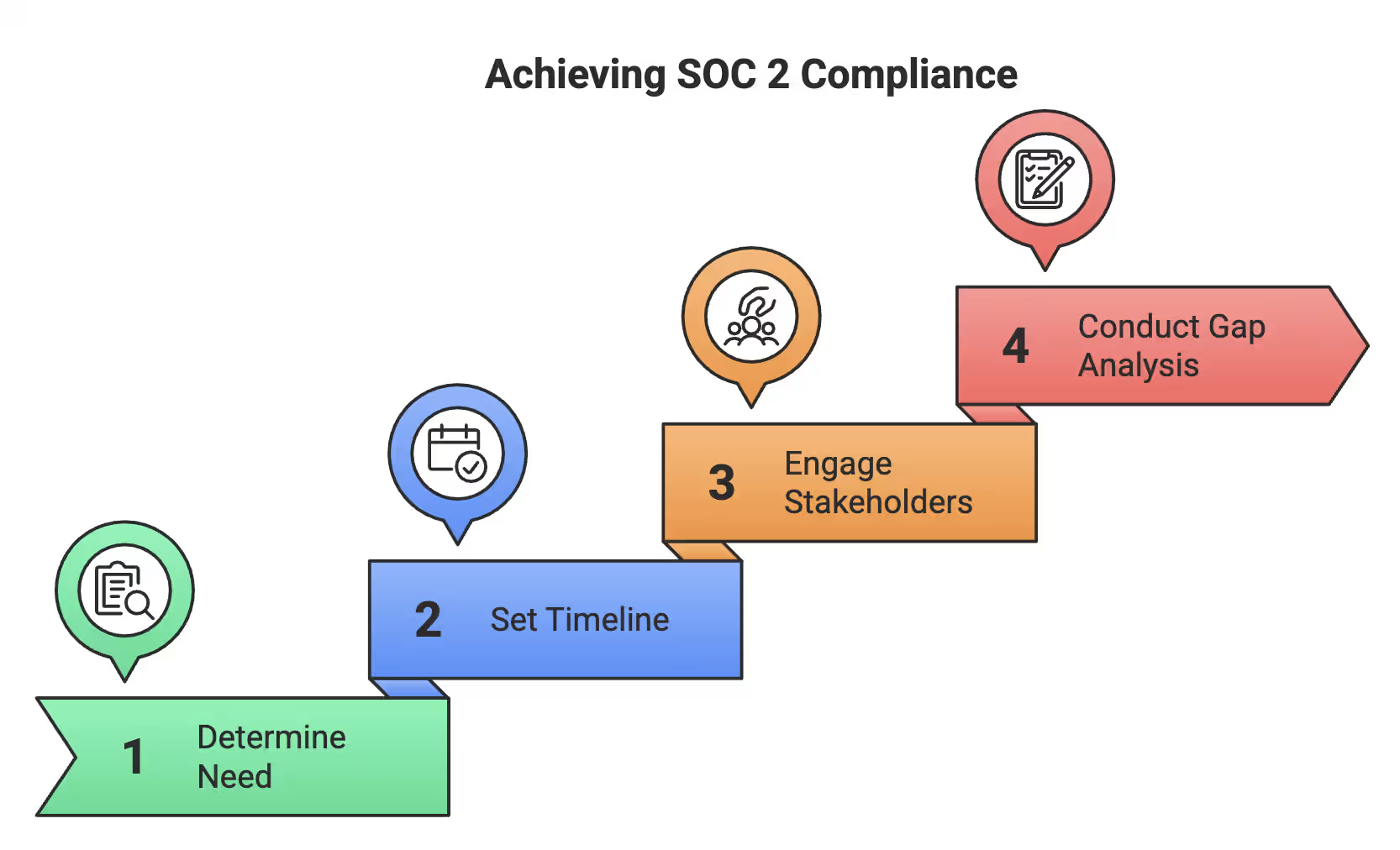
Want to get SOC 2 compliant without losing your mind? Here's your no-BS action plan:
Achieving SOC 2 Compliance
As experts keep saying (and we agree): "Starting early and involving all relevant stakeholders from the beginning" is absolutely critical.
Thank goodness for modern tech, because manual SOC 2 audits are a special kind of torture:
Companies using automation complete audits in half the time and save 25-50% on costs. That's not just nice—that's a no-brainer.
The proof is in the pudding. Start early, and you'll build your compliance program alongside your business growth. Wait too long, and you'll be scrambling to patch security holes while watching deals slip through your fingers.
In today's "show me your security credentials" world, SOC 2 compliance isn't a luxury—it's your ticket to play. Without it, you're just the vendor nobody trusts with their data.

Senior Security Consultant