Ever wondered why some companies seem bulletproof against cyberattacks while others get breached every other quarter? Here’s the uncomfortable truth: most organizations don’t fail because they lack tools—they fail because they lack structure. Security isn’t magic. It’s a system. A disciplined one.
That’s why BSI ISO/IEC 27001 exists. It’s not another badge to flex on your website. It’s the global benchmark for building an information security management system (ISMS) that actually works in the real world. No guesswork. No crossing your fingers and hoping your firewall catches everything. Just a clear, risk-based framework that tells you what matters, what needs protecting, and how to protect it—every single time.
And here’s the kicker: companies that adopt ISO 27001 don’t just reduce risk. They move faster. They win deals. They earn trust. They stop putting out constant fires and start building security that scales.
If you’ve ever wanted a practical, no-nonsense walkthrough of BSI ISO/IEC 27001—how it works, why it matters, and what the certification journey actually looks like—you’re in the right place.
What is BSI ISO/IEC 27001 and Why It Matters?
BSI ISO/IEC 27001 is the gold standard for building a security system that works every day—not just on audit day. At its core, it’s a globally recognized framework created by ISO and IEC to help organizations protect their information assets with precision, structure, and accountability.
Here’s what it actually means in practice:
- You stop relying on random tools and start following a proven, risk-based method.
- You define what’s sensitive, understand where the threats are, and implement controls that actually move the needle.
- You create an ISMS that aligns people, processes, technology, and policies—so nothing falls through the cracks.
And it matters because the numbers don’t lie. Certified organizations see fewer incidents, lower breach costs, stronger operational resilience, and a massive boost in customer trust. In a world where companies are asked to “prove” their security, BSI ISO/IEC 27001 is the credibility signal buyers, partners, and regulators actually pay attention to.
This isn’t checkbox compliance. It’s a strategic advantage.
Understanding the 27001 BSI Certification Lifecycle
BSI certification isn’t about jumping through hoops—it’s about building an ISMS that actually works under pressure. The lifecycle is structured, predictable, and designed to take you from uncertainty to audit-ready confidence. And the impact is real: organizations report 75% lower overall business risk and 51.6% fewer security incidents after certification. Here’s how that path unfolds.
From Initial Consultation to the ISO 27001 Certification BSI Audit
The journey begins with initial consultation. BSI helps you outline your scope, maturity level, and certification pathway so you’re not guessing what’s required.
Training usually follows. It equips your team to implement Annex A controls correctly—and avoid surprises later.
A gap analysis is where things get real. BSI reviews your existing ISMS and highlights weaknesses early. You get a clear plan of action before auditors ever look at your environment.
Then comes the formal audit, done in two steps:
- Stage 1: Documentation review—policies, procedures, risk assessments, SoA, evidence.
- Stage 2: Operational verification—interviews, implementation checks, and end-to-end control testing.
The result is a certification decision based on how your ISMS performs both on paper and in practice—and for most organizations, the full readiness journey takes 3–6 months, while larger environments may need 6–12 months.
Role of BSI Certification ISO 27001 in Compliance
This is where BSI’s value shows. A certificate from BSI isn’t a vanity badge—it’s a trust signal that your controls aren’t theoretical; they’re working, repeatable, and independently validated.
It strengthens your entire compliance posture. Customers see a lower-risk partner. Regulators see alignment with global frameworks. Sales teams see faster procurement cycles. And leadership sees reduced audit fatigue because one strong certification often satisfies overlapping requirements.
In industries where contracts hinge on credibility, a BSI-issued ISO 27001 certificate becomes a competitive advantage—not just an obligation—especially since BSI is backed by respected accreditation bodies like UKAS and DAR.
Transitioning to ISO/IEC 27001:2022 Under BSI
The transition deadline—October 31, 2025—is now behind us. BSI makes the upgrade to ISO 27001:2022 structured and predictable:
- Understand the new controls and theme-based domains
- Update policies, risk treatment plans, and the SoA
- Perform an internal readiness review
- Complete BSI’s transition audit
Cleaner structure. Updated threat coverage. A future-proof ISMS built for today’s risks.
Building a Compliant BSI ISMS and Achieving BSI ISO 27001 Certification
Ready to build something that won’t collapse the moment auditors start asking real questions?
BSI ISO 27001 isn’t about box-ticking—it’s about building an ISMS that holds up under pressure. The standard moves through five core clauses, each stacking on the last. Get one wrong, and the whole structure starts to wobble.
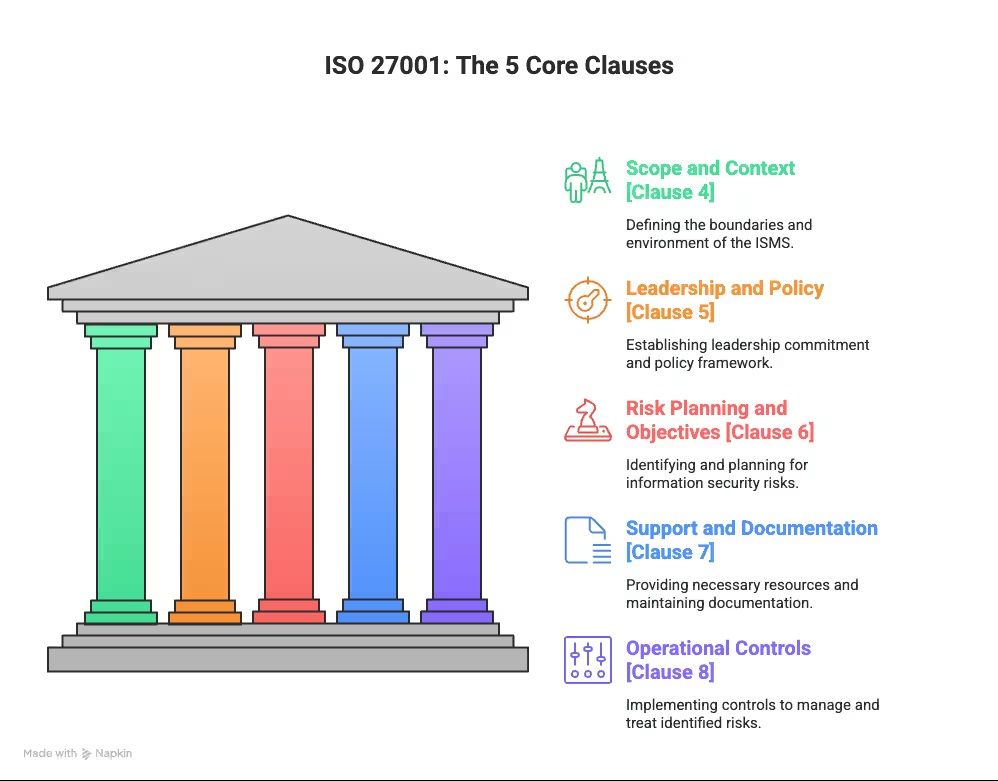
ISO 27001- The 5 Core Clauses
Defining Scope and Context (Clause 4)
Your ISMS only works if you know exactly what it covers. Most teams blow this step by choosing a scope that’s too broad, too vague, or full of blind spots.
What matters here is clarity:
- Identify internal issues—skills gaps, staff turnover, operational weaknesses
- Map external factors—industry regulations, market threats, customer expectations
- Draw hard boundaries for what your BSI ISMS will and will not protect
A tight scope keeps you focused, avoids resource drain, and stops endless scope creep. Miss here, and you’ll spend months fixing foundational mistakes.
Leadership and Policy Development (Clause 5)
If leadership treats security like a chore, auditors will spot it instantly. Clause 5 demands visible commitment—not lip service.
That means leadership must:
- Set an information security policy tied to business strategy
- Embed ISMS requirements into everyday processes
- Allocate real resources—time, budget, people
There’s a reason 80% of successful certifications point to executive ownership. Without it, your ISMS becomes a checkbox exercise with no staying power.
Risk-Based Planning and Objectives (Clause 6)
Risk management isn’t about decorating spreadsheets—it’s about understanding what can genuinely break your business.
Clause 6 requires:
- A consistent, repeatable risk assessment methodology
- Identification of risks to confidentiality, integrity, and availability
- A Statement of Applicability (SoA) that justifies every included or excluded control
Your risk decisions—avoid, transfer, mitigate, accept—must match the reality of your environment, not guesswork.
Support and Documentation (Clause 7)
An ISMS without capable people and documented proof is dead on arrival.
You need to:
- Define competencies for every ISMS role
- Run real security awareness training (remember: humans cause most breaches)
- Maintain documentation that proves compliance—not paperwork for its own sake
People can either reinforce controls or completely undermine them.
Operational Controls and Risk Treatment (Clause 8)
Clause 8 is where plans stop being theoretical.
It requires:
- Implementing processes exactly as planned
- Reassessing risks on a predictable cadence
- Controlling third-party services that affect security
Many teams bring in a BSI lead implementer here—and it shows. Execution is where inexperienced teams stumble.
How to Prepare for a BSI ISO 27001 Lead Auditor Assessment
Audit day coming up? Here’s the truth: you don’t need perfection—you need proof. Most organizations fail not because their security is weak, but because they can’t demonstrate that their controls actually work. A BSI lead auditor assessment is less about catching you off guard and more about confirming that your ISMS isn’t just paperwork—it’s reality.
Internal Audit Best Practices
Internal audits are your dress rehearsal. Treat them like it.
Here’s what strong organizations do:
- Run audits regularly, not reactively
- Use competent, independent auditors—someone who didn’t build your ISMS
- Develop an audit program that defines scope, frequency, method, and reporting
- Conduct mock audits to surface issues early
Many teams wisely bring in external ISO 27001 specialists. Not to “pass,” but to avoid blind spots—and blind spots are exactly what BSI auditors notice fastest.
Statement of Applicability (SoA) Preparation
Your SoA is the backbone of your ISMS. Auditors read it like a blueprint, and they can tell instantly whether it’s thoughtful or rushed.
Make it defensible:
- Include all 93 Annex A controls with clear rationales for inclusion or exclusion
- Show understanding of applicable legal and regulatory requirements
- Link every decision to actual policies and procedures
- Secure formal management approval—auditors expect executive ownership
Your SoA tells auditors how you think about risk. If it’s weak, everything else collapses.
Corrective Actions and Nonconformity Handling
Nonconformities aren’t failures—they’re signals. Auditors don’t expect perfection; they expect a system that improves.
Know the difference:
- Minor: isolated issues with limited impact
- Major: structural problems that undermine your ISMS
Follow the disciplined flow: identify → investigate → correct → implement → validate. And document every step. Nothing frustrates auditors more than “we fixed it but forgot to record it.”
What BSI 27001 Lead Auditors Look For
BSI auditors aren’t hunting mistakes—they’re looking for authenticity:
- An ISMS used in real operations, not just during audit week
- Staff who understand their security responsibilities
- Clear documentation of risks, controls, and treatments
- Consistent control application across the entire scope
- Leadership visibly driving the ISMS
Because at the end of the day, BSI certification isn’t about passing an exam. It’s about proving that security is baked into how your organization actually works.
Once the audit expectations are clear, the next step is equipping your team with the skills and tools to actually meet them.
Training and Tools to Support ISO 27001 BSI Implementation
You can't just wing your way to BSI ISO 27001 certification.
Yup, you need proper training. And the right tools. Because knowledge without the right support system? That's just expensive confusion.
BSI ISO 27001 Certification Training Course
BSI Training Academy doesn't mess around with fluff. Here's what they offer:
- Requirements of ISO/IEC 27001:2022 – Learn the fundamentals without the jargon
- Implementing ISO/IEC 27001:2022 – How to actually make it work in the real world
- ISO/IEC 27001:2022 Internal Auditor – Become your own quality control
- ISO/IEC 27001:2022 Lead Implementer – Five-day intensive for project leaders
The best part? They use accelerated learning techniques that actually stick. In-person, remote, on-demand - pick your poison.
And here's proof it works: over 80% of organizations with proper training sail through certification. The rest? They struggle.
Using a BSI Lead Implementer for Project Execution
A certified BSI lead implementer isn't just nice to have – they're essential. These people know:
- How to implement and maintain an ISMS that actually functions
- Management tools that work (not just theory)
- How to spot gaps before they become problems
The five-day BSI ISO 27001 lead implementer course teaches you to explain implementation processes and identify frameworks following the PDCA cycle.
Bottom line: Organizations using certified implementers cut implementation time by up to 50%. That's months of your life back.
Technology Tools for ISMS Monitoring and Reporting
Managing your BSI ISMS manually is like trying to run a kitchen with a wooden spoon. BSI Connect gives you:
- 50% faster implementation (we're not kidding)
- Document control that actually controls documents
- Organization-wide visibility so nothing falls through cracks
- Dashboards that help you make smart decisions early
Integrating ISO 27701 BSI for Data Privacy Compliance
ISO 27001 certification BSI covers security. But what about privacy? That's where ISO 27701
BSI steps in:
- Turns your ISMS into a Privacy Information Management System (PIMS)
- Plays nice with GDPR and CCPA requirements
- Integrates privacy controls into your existing security setup
Smart organizations implement both standards together. Why? You get complete protection for information assets AND personal data, plus streamlined compliance with international privacy laws.
The whole truth? Training and tools aren't expenses - they're investments that pay for themselves.
Maintaining and Improving Your BSI ISO 27001 Certification
Getting your BSI ISO 27001 certification feels amazing. You did it!
But here's what nobody tells you: the certificate is just your entry ticket. The real security magic happens in what comes next.
Surveillance Audits and Annual Reviews
Once you're certified, BSI certification ISO 27001 puts you on a three-year cycle that looks like this:
- Annual surveillance audits to verify you're still doing what you said you'd do
- Annual surveillance audits, including sample-based checks of how well your ISMS actually works.
- A full recertification audit every three years to prove you still deserve that certificate
ISO 27001:2013 is officially dead. The October 31, 2025 transition deadline has come and gone, and any organization still clinging to the old standard is now out of alignment. If your transition audit isn’t already done, you’re not “behind schedule” — you’re exposed. And every week you delay widens that gap.
Don't wait until the last minute. Trust me on this one.
Continuous Risk Assessment and Control Updates
Static security is dead security.
The threat landscape changes faster than fashion trends, so your risk management needs to keep up:
- Run risk assessments regularly - not just when the calendar tells you to
- ISO 27001:2022's Clause 9.1 emphasizes dynamic monitoring for a reason
- Automate your security controls testing because manual processes don't scale
Here's a stat that should grab your attention: 70% of organizations are ramping up investment in continuous monitoring technologies. They know something you should too.
Aligning with Business Growth and New Threats
Your organization today isn't the same one that got certified last year. That's good! Growth means success.
But it also means your BSI ISMS needs to evolve:
- Reassess your scope whenever stakeholder needs shift or you add new services
- Update those Annex A controls, especially the 2022 additions like Threat Intelligence (Control 5.7)
- Factor in climate change considerations - yes, it's now explicitly required in Clause 4.1
Remember Clause 10.1's golden rule: continuous improvement is mandatory. You don't need perfection, but you absolutely need progress.
And progress that you can prove.
Conclusion: Why BSI ISO 27001 Is a Strategic Investment
Here’s the real story: BSI ISO 27001 isn’t a trophy you hang on a wall. It’s a strategic moat. The kind that keeps attackers out and keeps your business standing when others crumble.
And the impact? Hard to ignore:
- 75% drop in overall risk
- 51% fewer security incidents
- 43% bump in sales opportunities
- Nearly 30% sliced off breach costs
But numbers only tell part of it. The real shift happens inside your company. People stop guessing. Processes stop wobbling. Security becomes automatic—baked into how you work, not bolted on at the end.
Meanwhile, the world isn’t waiting. Customers expect this. Partners require it. Competitors already have it. And yes—the old 2013 version is history. The transition window is closed, and any company still operating on the outdated standard is already behind.
Sure, certification takes effort. But one breach will cost you more than every audit, consultant, and training session combined.
That’s why the smart companies don’t see ISO 27001 as compliance. They see it as positioning—proof they’re the trustworthy choice in a world drowning in breaches.
Turn ISO 27001 from a compliance burden into a competitive advantage with UprootSecurity — helping you automate controls, reduce risk, and prove trust effortlessly. → Book a demo today
Frequently Asked Questions

Robin Joseph
Senior Security Consultant
