0%
Annual “checkbox” pentests are on their last legs.
More than 58% of companies still test once a year—or whenever they feel like it. Sure, that might keep auditors off your back. But it won’t stop a breach. Threats evolve daily. Attack surfaces shift by the hour. A PDF report from six months ago won’t help when someone’s already in.
Security leaders know it. The numbers show it. Zero-days doubled in just one year. Most IT heads admit they still don’t feel protected—despite bigger security budgets. Why? Because old-school pentesting just can’t keep up.
Traditional testing moves slow, costs too much, and covers too little. It’s a process built for waterfall development in a DevSecOps world.
That’s why more teams are flipping the script. Models like Pay-Per-Vulnerability and PTaaS (Penetration Testing as a Service) are gaining ground. They’re fast. Flexible. Built for how we build software now. And they don’t just uncover flaws—they redefine how security testing adds value.
Security isn’t a one-time event. It’s a continuous process. And this new wave of testing finally treats it that way.
Traditional pentesting hasn’t kept up with the pace of modern development. What was once considered best practice now feels outdated—too slow, too costly, and riddled with blind spots. Here’s where it consistently falls short:
Most tests take 4–6 weeks to complete. That’s a long window where vulnerabilities stay exposed—and attackers aren’t waiting around.
With tight timelines, testers can’t go deep. Large networks, cloud environments, and APIs often get only a surface-level scan. Critical systems get skipped due to time constraints.
Your results depend heavily on who’s doing the test. One tester might uncover real risks. Another might just check the boxes. There’s no guarantee of depth or accuracy.
These tests capture a snapshot, not a stream. Any new code, feature, or config pushed after the test gets no coverage—leaving you exposed for months.
Manual testing takes time, coordination, and budget. It’s hard to repeat and doesn’t scale with fast-moving DevOps or CI/CD environments.
It’s no longer enough to test once and hope for the best—security needs to move at the speed of your code.
The Pay‑Per‑Vulnerability (PPV) model flips traditional security testing on its head. Instead of paying a flat fee for time or reports, you only pay when a valid, exploitable vulnerability is found. No fluff. No billable hours. Just results.
Think of it as outcome-driven pentesting. Whether it's an independent hacker or a specialized security team, they get rewarded only when they deliver a confirmed security issue—one that actually matters. This model isn’t about generic scan results or theoretical risks. It’s about verified, real-world threats that you can fix immediately.
PPV has grown popular as organizations look for more efficient, ROI-focused security. It blends the accountability of bug bounty programs with the structure of traditional penetration testing. You define the scope, set the reward ranges, and security researchers dig in.
This approach not only motivates testers to find meaningful flaws, but it also eliminates the noise of false positives and bloated reports. Bottom line: you get what you pay for—and what you pay for is actual risk reduction.
Pay-Per-Vulnerability flips the traditional pentesting model on its head. Instead of paying for time, you pay for actual results—vulnerabilities found, not hours logged. That shift changes everything: cost structure, speed, and how security work gets done.
In a traditional pentest, you pay no matter what they find—even if the report’s empty. With Pay-Per-Vulnerability, vendors earn only when they find real issues. That puts your budget to work solving actual problems, not funding box-ticking exercises.
Forget waiting weeks for a final report. Pay-Per-Vulnerability platforms deliver results as they happen. First findings come in hours—not days—and full results take ~2.25 weeks, not 3+. That means faster fixes, fewer open exposures, and better sleep at night.
Modern PTaaS dashboards show live vulnerabilities across your stack. Security teams can act immediately. Business leaders can track risk in real time. Devs can retest fixes mid-sprint—before bad code hits prod.
This model fits naturally into CI/CD workflows. Kick off tests when features go live. Automate ticket creation through integrations with Jira, ServiceNow, or Azure DevOps.
Pay-Per-Vulnerability doesn’t just test faster—it tests smarter. For DevSecOps teams moving fast and breaking (some) things, it’s a better way to stay secure without slowing down.
Pay-Per-Vulnerability doesn’t follow the usual “bill by the hour” model. Instead, it flips the focus from effort to outcome—tying cost directly to the impact of what’s found. You only pay when there’s something real to fix.
Vulnerabilities are priced by risk level. The more damage a flaw could cause, the more it costs:
So a remote code execution bug? That might net $5K+. A basic XSS issue? $150. This structure ensures the focus stays on what actually matters—not on padding time sheets.
Companies set aside a dedicated bounty pool—budget meant only for confirmed vulnerabilities. This does a few things well:
Want more attention on your customer data systems? Assign more of the pool there. Ethical hackers follow the incentives.
There are two common models:
No bugs? No charge. You pay only when real vulnerabilities are confirmed. It’s performance-based—and the vendor takes the risk. Ideal for lean security budgets.
You pay a flat monthly fee for access to the testing platform, plus rewards for each issue found. This gives you predictable costs and minimum test guarantees—better for large orgs with ongoing needs.
Bottom line? Pay-Per-Vulnerability puts the money where the risk is. And that’s exactly where it belongs.
Ethical hackers are the backbone of Pay‑Per‑Vulnerability. They bring real-world experience, fresh perspectives, and a motivation that’s tightly linked to outcomes—not effort. It’s a shift from closed-door testing to open, crowdsourced security.
Bug bounty programs—and modern bug software platforms—reward findings, not time spent. That creates the right kind of pressure: dig deeper, find real flaws, earn more.
CERN’s program is a great example: 100 CHF for XSS, 500 CHF for root, and up to 5000 CHF for critical systems. You pay when it counts.
Strong PoCs are key. Microsoft’s framework ranks them:
For web bugs, PoCs often use minimal HTML changes or benign payloads. Think harmless comment tags—not destructive JavaScript or unauthorised shells.
No ethical hacker wants to be sued for helping. That’s why safe harbor matters.
Most programs also offer a 90-day remediation window before public disclosure—giving vendors time to patch while still keeping pressure on to fix things fast.
Bottom line? When legal and financial guardrails are in place, ethical hackers can move fast, go deep, and make real security better.
Pay‑Per‑Vulnerability isn’t just another buzzword. It’s how modern security teams ditch bloated retainers, cut through noise, and pay only when real risk is uncovered. No fluff. No filler. Just results.
A handful of platforms are redefining what efficient, outcome-based pentesting looks like. Here are four leading the charge:
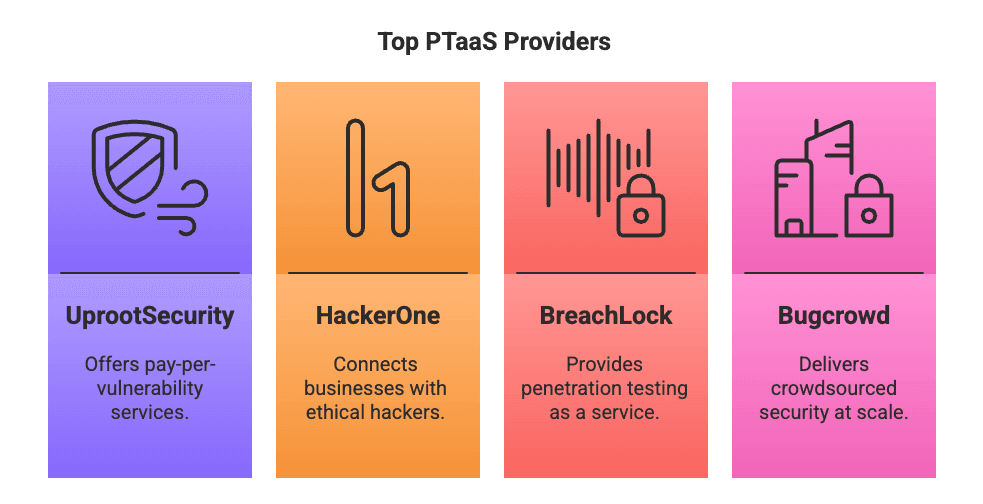
Top PTaaS Providers
Let’s get into each and see what makes them tick.
UprootSecurity
Uproot flips the traditional model on its head. You don’t pay for reports—you pay for results. Their Pay‑Per‑Vulnerability pricing directly ties cost to real risk uncovered. Here’s how it works:
Their three-step testing covers web, mobile, cloud, and network assets. No fluff, no filler—just confirmed issues and clean reporting.
Hackerone
HackerOne brings the crowd—safely. Their platform connects you with vetted ethical hackers, all managed in one sleek dashboard.
This mix of people and platform helps orgs fix faster—and smarter.
BreachLock
BreachLock blends AI with deep human testing. It’s scalable, repeatable, and sharp.
Great if you want automated coverage without sacrificing human insight.
Bugcrowd
Bugcrowd brings the power of the crowd to modern security testing, pairing companies with a global network of ethical hackers.
With Bugcrowd, you get creativity and scale—ideal for teams that want continuous coverage without drowning in noise.
Rolling out a Pay‑Per‑Vulnerability program isn’t just about turning on a bounty board. It takes clear rules, smart structure, and the right blend of people and tools to make it work without burning your budget.
Good bug bounty programs start with clear boundaries. Microsoft’s framework offers a blueprint:
Make it easy for hackers to know what’s eligible. The clearer the scope, the more focused the findings.
Running your own bounty program sounds great—until you realize the cost.
Managed platforms fill that gap fast, with pre-vetted researchers and tested workflows. For most orgs, they’re the faster, cleaner start.
A solid program plugs into your existing security infrastructure. That means:
You want findings to move from detection to fix without friction.
Once bugs come in, tracking matters. Tools like Jira, ServiceNow, and Bugcrowd dashboards help triage and reward quickly.
CERN’s model is a strong one: 100 CHF for XSS, 500 CHF for root, 5,000 CHF for critical hits. It works because everyone wins—hackers get paid, teams fix fast, and the org builds resilience instead of tech debt.
Done right, Pay‑Per‑Vulnerability turns outside eyes into your sharpest security asset.
Old-school security testing is slow, expensive, and out of sync with how modern teams build and ship software. Pay‑Per‑Vulnerability flips that model—charging for actual risk, not hours spent poking around.
This isn’t just a pricing hack. It’s a complete rethink of how organizations approach security. Companies using this model uncover 42% more critical vulnerabilities and cut testing costs by up to 30%. PTaaS platforms reduce triage time from 89 minutes to just 20 per bug. First findings land within hours—not weeks—accelerating fixes and shrinking the window of exposure.
And the gap is only widening. While nearly 80% of IT leaders still feel underprotected despite rising budgets, agile teams are moving forward. They’ve moved past yearly scans and checkbox audits to continuous testing tuned to real-world threats.
With zero-days surging and attackers moving faster than ever, the traditional approach no longer holds. Pay‑Per‑Vulnerability isn’t just more efficient—it’s more accountable. It rewards outcomes, not effort. It delivers clarity, not confusion. And it’s exactly what security testing should’ve been all along.
Want real results, not just reports? Skip the noise and get straight to impact. Talk to our team and see how Pay-Per-Vulnerability testing can work for you.

Senior Security Consultant