0%
Ever wondered why security teams are ditching traditional penetration testing for something better?
Here’s the deal: Penetration Testing as a Service (PTaaS) isn’t just another acronym—it’s transforming how security testing gets done. The old model? Hire a consultant, wait weeks for scheduling, and then even longer for a static PDF report. By the time results arrive, your application has already evolved, leaving findings stale and out of sync.
PTaaS flips that model entirely. It blends human-led testing with the speed and convenience of cloud-based platforms. This balance is what makes a modern pentest as a service platform so powerful—it delivers security that scales as fast as your code. You get real vulnerabilities, found by real experts, in real time. No guesswork. No waiting games.
Unlike traditional methods, PTaaS enables testing after every code push—daily if needed. This continuous approach keeps security teams ahead of threats instead of playing catch-up. Whether you’re a startup or a large enterprise, PTaaS scales seamlessly with your workflows.
In short, it’s not just pentesting—it’s security that moves at the speed of your software.
Penetration Testing as a Service (PTaaS) is a modern, cloud-based approach to security testing. It replaces slow, one-off consultant-driven pentests with an on-demand platform that delivers faster, more flexible results.
Instead of waiting weeks for a report, PTaaS gives you real-time findings through an interactive dashboard. It combines automated tools with manual testing by security experts, so you catch both common and complex vulnerabilities. Leading PTaaS companies now offer specialized pentesting platforms that help teams run targeted tests across APIs, networks, and applications in one place.
Key features include:
PTaaS supports everything from web apps and APIs to cloud and network infrastructure. It’s scalable, fast, and built for agile teams.
PTaaS transforms security testing from a yearly checkbox into a continuous, developer-friendly process.
Most security leaders don’t just like PTaaS—they rely on it. And here’s why: the right PTaaS platform doesn’t just streamline testing; it elevates how your entire organization approaches risk. The benefits of PTaaS go beyond convenience, offering lasting value to both security and development teams.
Here’s what it delivers:
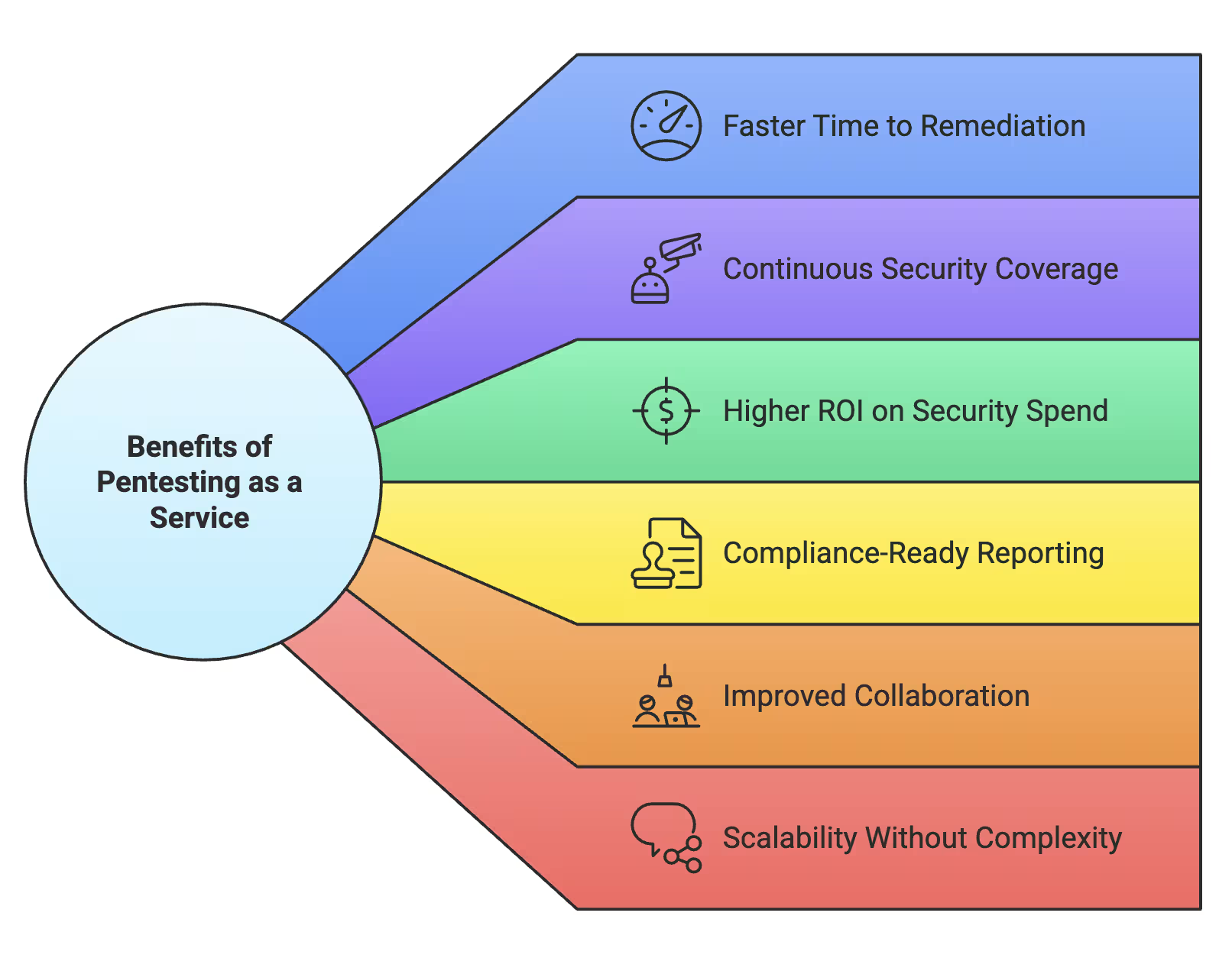
Faster Time to Remediation
Vulnerabilities are discovered and reported in real-time, allowing teams to fix issues immediately—often before the test even finishes.
Continuous Security Coverage
Test after every deployment, daily, or on-demand. PTaaS fits into DevOps and CI/CD workflows to keep pace with rapid development.
Higher ROI on Security Spend
By combining human expertise with automation, PTaaS delivers more value for each dollar spent—something even CFOs notice.
Compliance-Ready Reporting
Automatically generate reports that align with PCI-DSS, HIPAA, ISO 27001, SOC 2, and more—no manual formatting needed.
Improved Collaboration
Developers, testers, and security analysts can work from the same dashboard, tracking issues and fixes in real-time.
Scalability Without Complexity
Whether you’re testing one app or hundreds, PTaaS scales with your needs without requiring more headcount.
Benefits of Pentesting as a Service
In short, PTaaS turns security into a proactive, integrated business advantage—not a bottleneck.
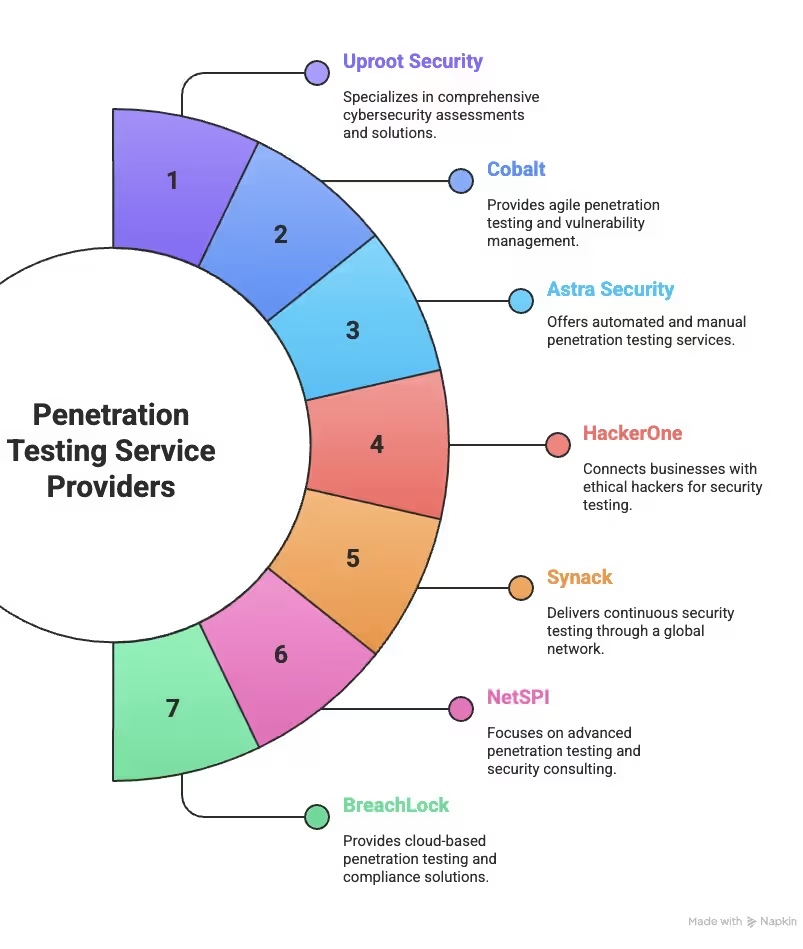
Want to know which PTaaS vendors actually deliver? These are the top penetration testing vendors that have redefined how modern pentest as a service works. Here are seven providers that security teams swear by—each with their own superpower:
Penetration Testing Service Providers
Let’s get into each of these PTaaS providers and explore what makes them stand out.
Uproot Security
The new kid on the block, but don't let that fool you. Uproot Security is making waves in the pen testing as a service space with a perfect 5.0 rating on G2. That's not easy to achieve.
What they do best:
Limited public info? Sure. But sometimes the best vendors are the ones not shouting about themselves.
Cobalt
The OG of PTaaS. Cobalt literally created this category, and they're still leading the pack.
Why they're trusted:
Cobalt gets DevSecOps. Their platform actually makes security testing feel like part of your development process, not a roadblock. Plus, they support all the compliance frameworks that matter: PCI-DSS, HIPAA, SOC-2, ISO 27001, and GDPR.
Astra Security
If you want comprehensive coverage, Astra's your pick. These guys don't mess around.
The numbers speak for themselves:
CTOs and CISOs love how Astra helps them shift from DevOps to DevSecOps without breaking their workflows. Their team? Certified pros (OSCP, CEH, CCSP) who contribute to OWASP and have discovered 50+ CVEs. Real deal.
Hackerone
The crowd-sourced powerhouse. HackerOne taps into their massive network of ethical hackers to deliver thorough security assessments.
What makes them different:
They follow all the industry standards (OWASP Top 10, PTES, OSSTM, CREST) and deliver comprehensive reporting that actually helps you meet SOC 2, ISO 27001, and GDPR compliance requirements.
Synack
The intelligence-focused platform. Synack combines human expertise with smart technology to deliver continuous penetration testing.
Their secret sauce:
Synack helps you maintain current inventories of your attack surface assets, segment them by business unit, and track testing coverage across your environment. Perfect for organizations that need to move beyond point-in-time assessments.
NetSPI
The enterprise favorite. NetSPI delivers technology-enabled, human-delivered penetration testing that scales.
Why enterprises choose them:
Their Resolve platform delivers live, actionable vulnerability reports and enables trend analysis over multiple years. Particularly popular with organizations in highly regulated industries who need that extra level of depth.
BreachLock
The AI-powered innovator. BreachLock combines human expertise, AI, and automation to optimize security testing outcomes.
What sets them apart:
BreachLock provides comprehensive visibility across your entire attack surface and helps organizations meet compliance requirements including HIPAA, PCI DSS, ISO 27001, SOC 2, and GDPR. Their reports are accepted by auditors and customers—no questions asked.
The truth? Each of these penetration testing service providers brings something unique to the table. Some penetration testing firms specialize in cloud environments, others in hybrid or on-prem systems. Your choice depends on your specific needs, development practices, and compliance requirements.
Choose wisely.
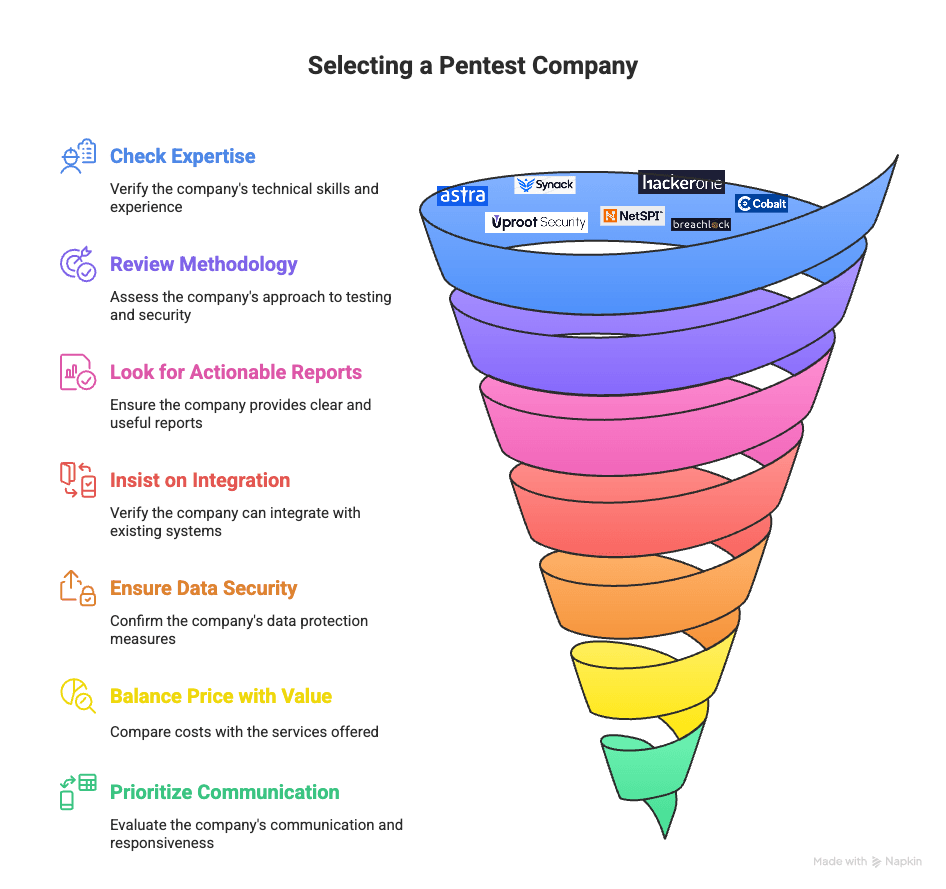
Choosing a pentest provider is about more than just finding a vendor—it’s about selecting a partner who fits your security goals. Organizations that carefully vet their PTaaS providers see up to 40% faster compliance certification. Here’s what to focus on:
The right PTaaS provider becomes an extension of your security team—choose one that strengthens your defenses, not just checks a box.
Selecting a Pentest Company
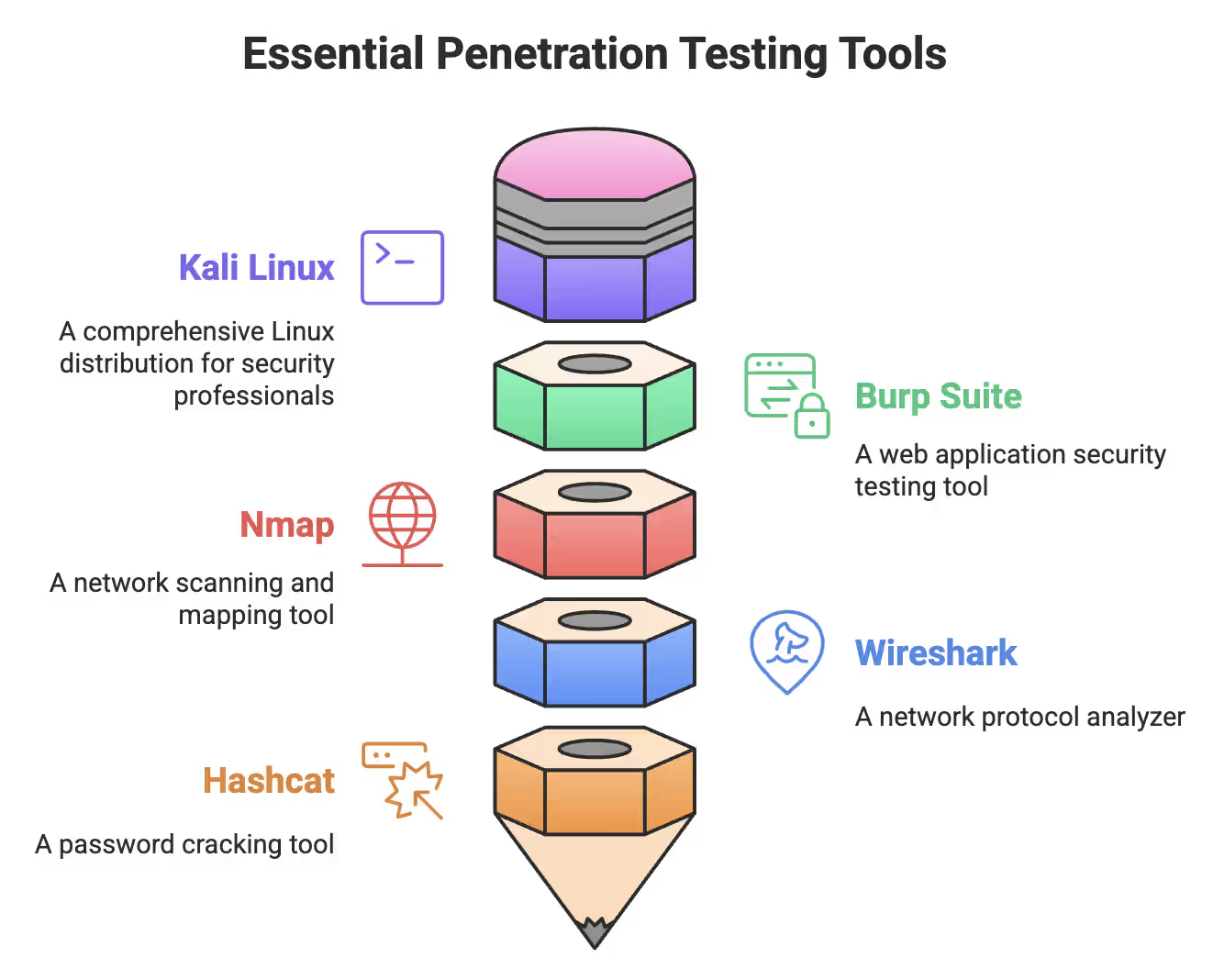
Want to know what separates real security professionals from script kiddies? It’s the tools they use. Every serious penetration test depends on a solid toolkit. While hundreds of tools exist, these five form the core arsenal used by both individual pentesters and professional penetration testing service providers:
Essential Penetration Testing Tools
Let’s break down each of these penetration testing tools and see why they’re considered essential.
Kali Linux
This isn't just another Linux distribution. Kali Linux is the undisputed champion of penetration testing platforms.
Why it dominates:
The beauty? No hours wasted configuring dozens of individual tools. Everything is ready to go. Many pen testing as a service companies even customize Kali for their specific methodologies and client needs.

Burp Suite
Web application testing without Burp Suite? Good luck with that.
What makes it the industry standard:
Burp Suite Pro automates scanning, boosting efficiency by up to 60% compared to manual testing. Web teams rely on it for faster, more accurate assessments.
Nmap
Network mapping is fundamental to any thorough penetration test.
Core capabilities:
Despite its age, Nmap remains a go-to tool for penetration testing service providers worldwide. Networks evolve, and Nmap evolves with them.

Wireshark
Network packet analysis provides critical insights during penetration tests.
What it does:
Wireshark reveals subtle vulnerabilities that automated tools often miss. Teams report detecting 40% more authentication issues using it.
Hashcat
Password cracking is essential in comprehensive security testing.
Raw power:
Hashcat’s speed and versatility make it a staple for penetration testing service providers, ensuring password security checks are thorough and efficient.
These five tools form the core arsenal for almost every security testing as a service provider. Sure, there are numerous specialized tools for specific scenarios, but mastering these fundamentals remains essential for both internal security teams and external penetration testing providers.
Without these tools, you're not doing serious security testing. You're just playing around.
At first glance, Security Testing as a Service (STaaS)—often delivered as PTaaS—may seem similar to Software as a Service (SaaS). Both are cloud-based, subscription-driven, and accessible through a browser. But beyond these surface similarities, they serve very different purposes and deliver distinct value. Here’s a quick comparison:
| Feature/Aspect | Software as a Service | Security Testing as a Service (STaaS) |
|---|---|---|
| Purpose | Provides software functionality (CRM, HR, productivity tools) | Delivers expert-led security testing and validation |
| Human Expertise | Mostly automated | Combines automation with skilled security professionals |
| Security Outcomes | Not focused on security | Validates application security posture continuously |
| Workflow Integration | Limited integration | Integrates with Jira, GitHub, CI/CD pipelines for seamless DevSecOps |
| Collaboration | Standard tool collaboration |
STaaS isn’t just “SaaS for security.” By embedding human intelligence into an automated platform, it ensures ongoing security validation, faster remediation, and deeper value for development teams. Understanding this distinction is essential when choosing modern security testing solutions.
PTaaS has redefined security testing. It closes the gap between thorough assessment and real-world agility—helping teams find vulnerabilities 75% faster while cutting costs by 30–40%.
Gone are the days of once-a-year consultant visits. PTaaS brings continuous, on-demand testing that keeps up with your development cycles. It gives you access to skilled professionals across domains—crucial when most cybersecurity roles sit unfilled for 120+ days.
The seven PTaaS providers we've covered each offer unique strengths: integration, testing depth, reporting quality, and compliance support. Organizations that choose wisely report 40% faster compliance and quicker remediation.
Yes, switching to a new model takes adjustment. But the payoff? Stronger security, faster insights, and tighter collaboration between dev and security teams.
PTaaS transforms penetration testing from a checkbox task into an always-on security practice—helping you stay ahead of threats while making smart use of budget and resources.
And the best part? You don’t have to figure it out alone. These vendors are transparent, capable, and ready to help.
Security isn't annual anymore. It's continuous. And with PTaaS, it’s finally manageable.
Ready to try a smarter, faster approach to penetration testing?
Talk to our team today and see how PTaaS can transform the way you test and secure your applications.

Senior Security Consultant
| Enables real-time communication between testers and developers |
| Updates & Access | Cloud-based, auto-updated | Cloud-based, auto-updated, with actionable security insights |