Ever wonder why your software risk tools keep missing the vulnerabilities that actually matter? Here’s the uncomfortable truth: over 60% of breaches stem from issues traditional scanning tools don’t even flag. That sleek platform you rely on? It has blind spots. And those gaps are where attackers slip in.
The problem isn’t that risk tools are useless—they’re just limited. Static scans overlook dynamic threats. Dependency checkers miss transitive libraries buried three levels deep. And cloud misconfigurations? They often escape notice until attackers exploit them.
Then comes the data problem. Feed outdated SBOMs or incomplete dependency lists into your tools, and you’ll get a false sense of security. Hidden code libraries, unmanaged containers, and overlooked APIs become attack paths no dashboard shows.
And don’t forget human error layered on top. Developers bypassing scans to hit deadlines, teams ignoring “low severity” alerts, or bias creeping into how risks get prioritised. Add AI model risks, unmonitored CI/CD pipelines, and supply chain blind spots, and you’ve got a perfect storm of invisible threats.
Why Risk Management Software Misses Critical Software Threats
Your risk management software isn’t broken—it’s just blind where it matters most. The problem? It flags the obvious, but the critical risks keep slipping by.
Start with pipelines. Nearly nine out of ten enterprises struggle with misconfigurations, yet most tools don’t catch weak branch protections until attackers do. AI is another landmine—63% of companies never check whether their AI tools are secure before rolling them out. That’s not oversight, that’s negligence.
Then there’s speed. Emerging tech evolves faster than your models. New frameworks, APIs, and libraries pop up daily, while your software plays catch-up. Meanwhile, supply chains are riddled with hidden dependencies and third-party flaws—exactly the kind of risks that only explode once it’s too late.
The human factor makes it worse. Teams dismiss “low severity” alerts, deadlines push developers to skip scans, and groupthink clouds judgment. Fewer than half of organisations even feel confident in their own assessments.
Here’s the hard truth: risk management software is useful, but it’s not bulletproof. Knowing its blind spots is the only way to stop threats from slipping through and hitting where it hurts most.
Top Software Risk Assessment Tools to Detect Hidden Risks
Software risk isn’t just about bugs. It’s about hidden vulnerabilities, overlooked dependencies, and misconfigurations that can take down your systems before you even notice. The right tools don’t just scan—they shine a light on what’s hiding in plain sight. They give your team the insights it needs to catch issues early, prioritise fixes, and prevent costly mistakes down the line.
Some of the top software risk assessment tools you should know:
- Uproot Security
- Snyk
- WhiteSource
- Veracode
- Sonatype Nexus
- Checkmarx
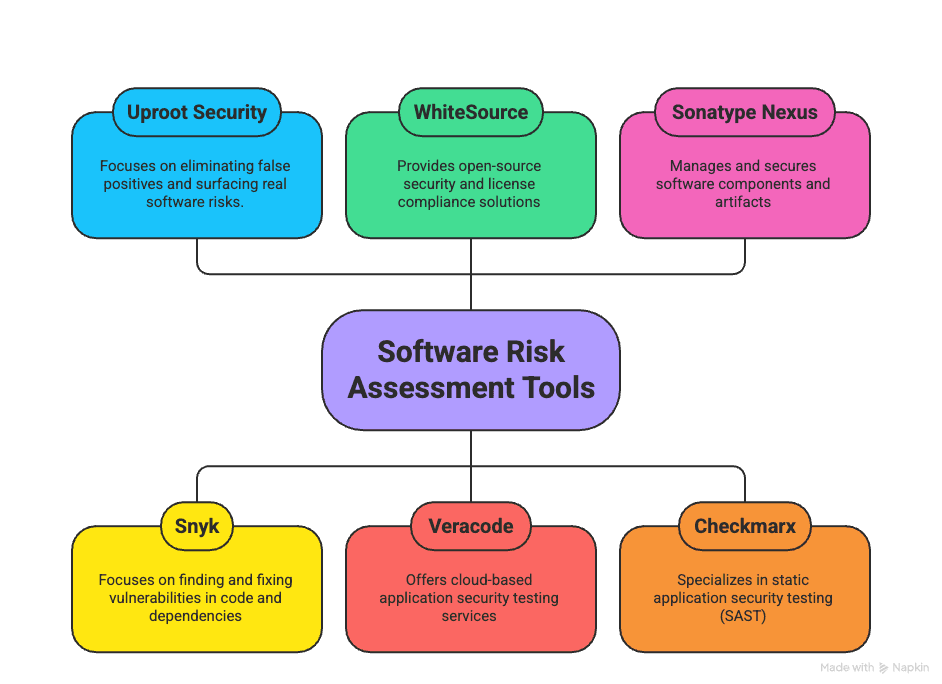
Top Software Risk Assessment Tools
Let’s break down what makes each of these tools worth your attention.
1. Uproot Security
Uproot Security cuts through noise in penetration testing by eliminating false positives and compliance clutter. It delivers clear, business-focused findings and streamlined reporting, so teams fix what truly matters—fast, efficient, and without wasted effort.
2. Snyk
Snyk scans open-source libraries, containers, and even infrastructure-as-code for vulnerabilities. It integrates directly into CI/CD pipelines, sending developers real-time alerts and actionable guidance. The result? Problems are fixed before code ever reaches production, turning potential disasters into proactive management.
3. WhiteSource
WhiteSource automates Software Composition Analysis (SCA) and generates detailed Software Bill of Materials (SBOMs). It tracks security flaws, license risks, and open-source compliance across your entire application stack. With this visibility, your team knows exactly what’s inside every component and where the hidden risks lie.
4. Veracode
Veracode combines static and dynamic application security testing. It identifies critical code flaws, ranks them by severity, and offers clear remediation steps. Developers can act fast without slowing down release cycles, ensuring security becomes part of the workflow rather than a roadblock.
5. Sonatype Nexus
Nexus monitors open-source components, flags risky libraries, and integrates with build pipelines. Vulnerable code is stopped before it reaches production. Think of it as a vigilant gatekeeper protecting your open-source ecosystem.
6. Checkmarx
Checkmarx merges static analysis with SCA, catching vulnerabilities early. Detailed reports make remediation fast and straightforward, embedding security into development rather than leaving it as an afterthought.
Pick the right tools, integrate them into your workflow, and turn hidden risks into visible, manageable actions. With these platforms, your team isn’t just scanning for issues—it’s staying ahead of them.
Limitations of Risk Assessment Tools to Watch
Here’s the uncomfortable truth: even the best risk assessment tools have flaws. And if you don’t know them, they’ll hit you where it hurts.
Static templates in dynamic environments
Most tools capture a snapshot of today’s risks and then sit collecting digital dust while your environment evolves constantly. Static templates miss everything that emerges after the initial assessment, leaving an incomplete picture. Organisations using dynamic assessments see fewer incidents. Rigid templates in a world that never stops changing are like navigating today’s internet with a 1995 map.
Third-party risk with outdated vendor data
Old or incomplete vendor data creates blind spots in third-party risk assessments. 82% of organisations waste at least a day per week fixing data quality issues. 71% of vendor records are incomplete, 67% inconsistent, and 31% obsolete. Most procurement teams can’t refresh data daily, and fewer than a third of companies have mature TPRM programs. The result? Your software misses critical changes in ownership, financial stability, or regional exposure.
Lack of AI/ML threat detection
Traditional tools catch only known threats. Sophisticated risks slip through. AI and ML could help—but they need massive datasets, constant tuning, and still produce false positives. Understanding why a model flags something is often a mystery. AI also introduces new risks: bias, data issues, and high resource demands. Most programs can’t balance detection power with practicality.
The bottom line: risk assessment tools are helpful, but not magic. Knowing their limits—static templates, outdated vendor data, and limited AI detection—is the first step to closing gaps before threats turn into disasters.
How to Spot Blind Spots with Risk Assessment Tools
Standard assessments won’t cut it anymore. Traditional risk tools catch the obvious, but hidden threats slip through. You need smarter approaches to uncover what your scans miss.
Cross-functional inputs for overlooked risks
The biggest problem? Teams don’t talk. Risk lives in silos, and departments define it differently. Security says one thing, compliance another, ops a third—nobody sees the full picture.
Here’s what works:
- Get internal teams and external partners (contractors, architects) talking through streamlined processes
- Bring representatives from every function into discussions, letting them raise concerns
- Reward collaboration on risk instead of just checking boxes
When teams communicate, hidden risks surface before they escalate.
Incident data for recurring patterns
Your incident logs aren’t just paperwork—they’re a map of recurring risks. That repeated near-miss in the same area? Not coincidence—it’s a red flag.
Centralised reporting gives you:
- Clear visibility into workplace risks and compliance gaps
- Insights into recurring safety or operational issues
- Actionable patterns to prevent future incidents
Modern incident management software categorises events by type, location, and timing, revealing root causes automatically.
SCA/SBOM for undocumented dependencies
Supply chain attacks rose 540% from 2019–2022. Most come from dependencies you didn’t even know existed.
- SCA scans your codebase, flagging hidden and transitive dependencies
- SBOMs inventory every component with full details
Together, they deliver transparency, simplify vulnerability management, and create a clear incident response roadmap—find it, patch it, done.
Stop flying blind. Cross-functional collaboration, incident analysis, and SCA/SBOM insights reveal what traditional risk tools miss—giving your team real visibility and control over software threats.
Using Risk Assessment Software to Surface Hidden Issues
"Scenario analysis and stress testing are not applied to evaluate alternative actions and assess response readiness to plausible and extreme scenarios." — Protiviti
Here’s the good news: modern risk assessment software has tricks traditional methods miss. It doesn’t just find risks—it turns hidden threats into actionable items you can actually tackle.
Heatmaps and scoring models for prioritising risks
Think of risk heatmaps as your threat radar. Colour-coded matrices cut through the noise, showing risks based on likelihood and impact. No more drowning in spreadsheets trying to figure out which problems deserve attention first.
The results are measurable:
- 30% faster issue resolution by addressing the right problems first
- Resources focus on high-priority, red-zone risks
- Stakeholders instantly understand what matters
The formula is simple: red = “drop everything and fix this now,” yellow = “monitor closely,” green = “not an immediate concern.” Everyone knows exactly where to focus their energy.
Scenario modelling for system- and process-level threats
Stop predicting the future. Start preparing for multiple possible futures. Scenario modelling uncovers hidden system-level threats by allowing teams to war-game outcomes rather than guess blindly.
The building blocks are simple:
- Variables: things that change (market conditions, economic shifts)
- Assumptions: educated guesses on variable behavior
- Multiple scenarios: worst case, best case, and everything in between
Leadership teams who review different potential futures make smarter decisions. It’s like having multiple backup plans ready before a crisis hits.
Integration with issue tracking to embed risk in workflows
Risk management that works is connected. Linking your risk software to issue tracking systems makes risks part of daily work. No more juggling spreadsheets and email chains.
Effective integrations include:
- Workflows that fit how your team actually operates
- Escalation rules ensuring urgent risks get urgent attention
- Full audit trails for accountability and follow-up
Teams using these integrations report 30% faster resolution times and more proactive risk reporting. When risks are linked to actions and outcomes, software stops being a passive tool—it becomes a strategic partner in solving problems.
This is the difference between software that simply identifies risks and software that helps your team actually manage, mitigate, and stay ahead of them.
How Software Risk Tools Strengthen Risk Assessment
Good news: modern software risk tools do more than just scan code—they turn hidden vulnerabilities into actionable insights. No more guessing which issues matter or scrambling after a breach.
Real-time dashboards for actionable visibility
Waiting weeks for reports? Forget it. Software risk platforms update automatically, showing live vulnerability status across applications, dependencies, and environments. You get:
- Instant alerts when high-risk issues appear
- Visual summaries that highlight critical hotspots
- Drill-down views to investigate risky modules without losing time
Automated alerts for code and dependency risks
Automation changes everything. These tools continuously monitor open-source libraries, container images, and even infrastructure-as-code for threats. When something is flagged—whether a license risk, CVE, or misconfiguration—you know immediately. Developers can fix issues before code ever reaches production.
Integration with development workflows
Risk tools that plug directly into CI/CD pipelines and issue trackers turn assessments into action. Vulnerabilities are linked to tasks, tracked, and escalated automatically. The result? Faster remediation, fewer surprises, and risks become part of everyday development rather than an afterthought.
Cross-functional collaboration
The best platforms make information accessible to security, DevOps, and QA teams in one place. Everyone works from the same data, sees trends, and prioritises fixes consistently. Hidden risks no longer slip through siloed processes.
With the right software risk tools, your team can see vulnerabilities earlier, prioritise fixes intelligently, and stay ahead of threats that traditional processes would miss. It’s software security that actually works for you, not against you.
Supply Chain Risk Management Software for Hidden Dependencies
Your supply chain is full of secrets—and those secrets are ticking time bombs. Supply chain risk management software helps you uncover hidden threats before they spread across your network.
Tracking upstream and downstream vendor risks
Here’s a scary fact: 81% of codebases have high or critical-risk vulnerabilities, and nearly half come from transitive dependencies. Think of these as the friends of your friends—the stuff you didn’t even know existed. Six out of seven project vulnerabilities stem from these “dependencies of dependencies.” That’s systemic risk.
Smart vendor risk management software tackles this by:
- Building centralised inventories of all third-party components, including vulnerability details
- Creating software bills of materials (SBOMs) mapping every dependency
- Showing upstream and downstream connections you never knew existed
Automating alerts for supply chain disruptions
The average supply chain faces around 300 disruptions every week. You can’t monitor that manually. Modern tools:
- Filter 1,000–1,500 potential disruptions daily using AI
- Send instant alerts when risks exceed tolerance thresholds
- Track ethical practices, financial health, and security posture in real time
Integrating supplier data with enterprise risk dashboards
Scattered supplier data is useless. Integration turns it into actionable intelligence. GRC software provides:
- Real-time reports showing where supplier risks are
- API connections that sync with existing systems
- Cross-functional visibility that aligns procurement, security, and risk teams
With these capabilities, supply chain risk management software doesn’t just track problems—it helps your organisation prevent them, respond faster, and keep your operations running smoothly—and protect your software from vulnerabilities buried in the supply chain.
Future-Proofing Software Risk
The world of software risk management is about to get a major makeover. Deloitte predicts cognitive technologies will start doing what humans used to do—and sometimes better. We’re talking AI that actually works, not just marketing fluff.
Here’s what’s coming:
- Controls built into products and services, monitoring risks 24/7
- Behavioral science informing smarter risk decisions
- Acceptance that you can’t prevent every risk, so resilience matters
- AI-powered tools that spot threats before they happen
The interesting part? Companies that take smart, calculated risks—even those outside neat regulatory boxes—will win big. Risk isn’t just something to avoid anymore; it’s a competitive advantage.
Imagine risk assessment tools connecting with blockchain and IoT, feeding machine learning systems that get smarter with every data point. The real winning formula? AI, machine learning, and humans working together. Neither alone can handle today’s flood of data.
Organisations that master this first won’t just play defence—they’ll set the rules. The future belongs to teams who can see around corners. The question is: are you ready?
Frequently Asked Questions

Robin Joseph
Senior Security Consultant
