Ever wondered why hackers always seem to be one step ahead?
It’s because they never stop looking for ways into your web applications. While your team is focused on building features, scaling infrastructure, or fixing bugs, attackers are busy scanning for that one overlooked vulnerability—the misconfigured endpoint, the exposed API key, the forgotten admin panel, or the unpatched library. And the uncomfortable truth? Hope is not a security strategy.
That’s where web application penetration testing comes in. It’s not just a checkbox activity—it’s a proactive way to stay ahead. You’re essentially hiring ethical hackers to think, act, and attack like real adversaries—but with your permission and for your benefit. They simulate real-world attack scenarios to uncover hidden flaws in your web apps before someone malicious does.
And no, they don’t just run automated scanners. They dive into your application logic, test user privilege boundaries, manipulate inputs, and expose any blind spots in your security posture.
Think of it this way: Would you rather learn about your vulnerabilities from your own security team—or from a public breach report?
Web app pentesting gives you clarity, control, and confidence.
Understanding Web Application Penetration Testing
Here’s what most people get wrong about web security: they think running an automated scanner is the same as penetration testing. It’s not. Real web app pentests involve skilled professionals who think like attackers—methodically uncovering vulnerabilities your tools can’t detect.
Need proof this matters? AWS logged over 310,000 unique web app attacks in just one quarter of 2020.
Penetration testers don’t just find weaknesses—they actively exploit them to show real-world impact. They:
- Hunt for misconfigurations and security gaps
- Chain multiple flaws to simulate real attacks
- Document exactly how much damage could be done
- Give you a fix-first roadmap that prioritizes risk
This goes beyond vulnerability assessments, which only tell you what might be a problem. Pentesting shows how those problems can be used to compromise your system.
Most tests reveal critical flaws like injection bugs, broken authentication, sensitive data exposure, and access control issues. But today’s web apps aren’t standalone—they’re sprawling ecosystems of APIs, third-party services, and cloud integrations. A proper pentest covers all of it.
From a compliance and trust perspective, web app pentesting isn’t optional—it’s foundational.
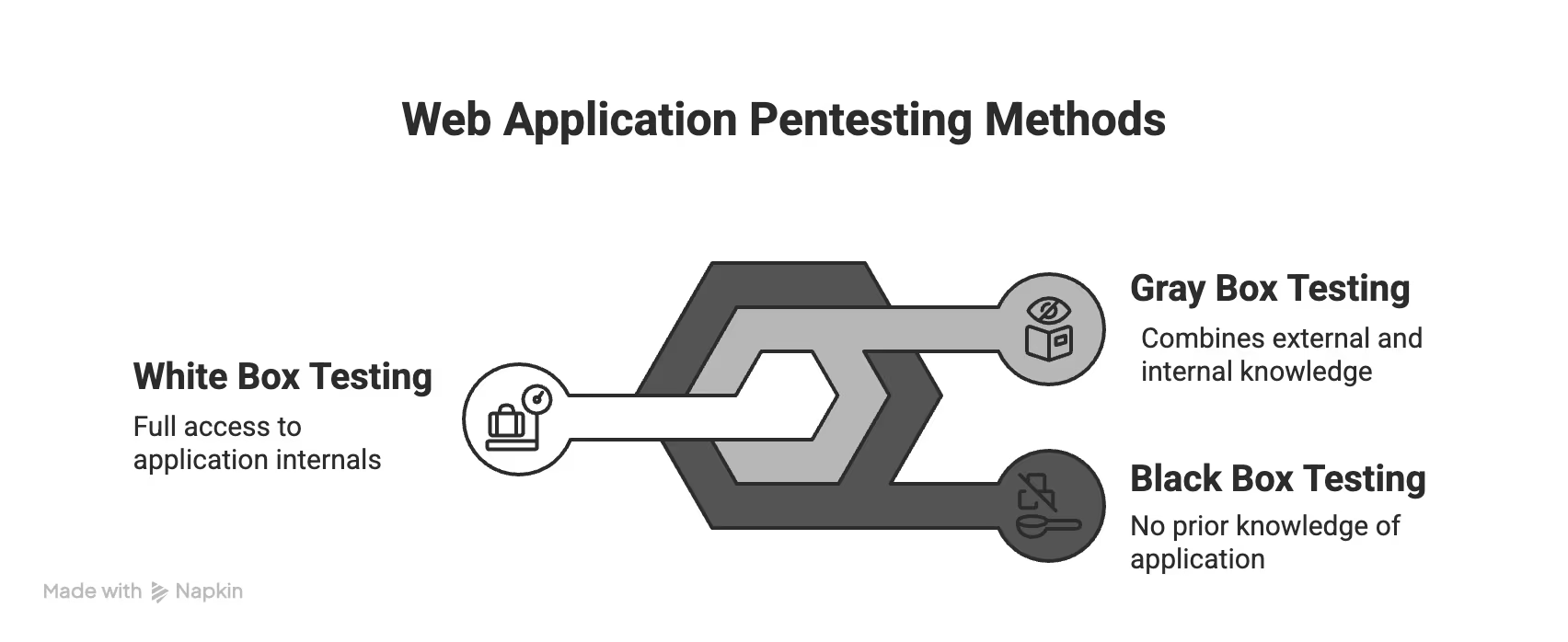
Web Application Penetesting Methods
When it comes to web app security, how you test is just as important as what you test. Penetration testing methods define the attacker's level of access and perspective during the engagement. Each method uncovers a different layer of risk—and choosing the right one can mean the difference between finding a surface-level issue or catching a deep architectural flaw.
These are the methods of web application penetration testing:
- Black Box
- White Box
- Gray Box
Web Application Penetration Testing Methods
Let’s go into each method to understand what it reveals—and what it might miss.
1. Black Box Testing
The tester has no internal access or prior knowledge—just like a real-world attacker. This method focuses on external attack surfaces, simulating someone trying to breach your application from the outside.
- Best for: Testing public-facing apps (e.g., login portals, APIs)
- Limitation: May miss internal misconfigurations or hidden logic flaws
2. White Box Testing
Also called clear-box or full-knowledge testing, this method gives testers complete access to source code, architecture diagrams, credentials, and internal documentation. It’s like a deep security audit of your application’s internals.
- Best for: Secure code reviews, CI/CD pipeline integration, compliance testing
- Limitation: Less representative of real-world external attackers
3. Gray Box Testing
A hybrid method where testers have limited knowledge—like user credentials or partial documentation—but not full access. It simulates an attacker with some insider access (e.g., a rogue employee or compromised user account).
- Best for: Balancing realism with depth; privilege escalation and session handling flaws
- Limitation: May require careful scoping to avoid overlap with other tests
Which Method Should You Use?
That depends on your goals.
- If you're simulating real-world attackers, go Black Box.
- If you're trying to uncover deep technical issues, go White Box.
- If you want a realistic but thorough assessment, Gray Box is often the sweet spot.
The most mature security programs use a combination of methods—testing external attack paths, insider threats, and code-level vulnerabilities across different environments and access levels.
Essential Web Application Penetration Testing Tools
Here’s the reality: most security teams miss critical vulnerabilities because they’re using the wrong tools—or using the right ones the wrong way. You can’t protect what you can’t see, and you can’t exploit what you don’t understand. The tools below aren’t just helpful—they’re essential penetration testing tools for running effective, real-world web app pentests.
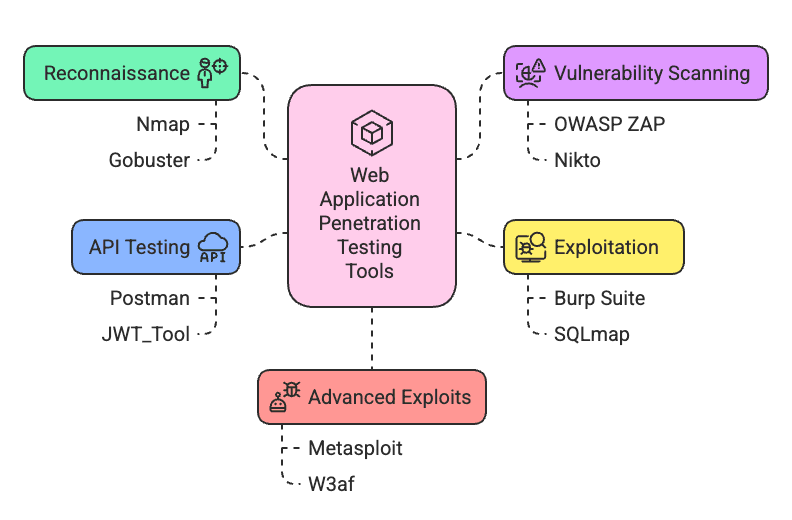
To make sense of it all, here are the essential categories of tools mapped to each phase of a web application penetration test. Each pair plays a key role in uncovering, validating, and exploiting vulnerabilities at different layers of your application stack:
- Reconnaissance – Nmap & Gobuster
- Vulnerability Scanning – OWASP ZAP & Nikto
- Exploitation – Burp Suite & SQLmap
- API Testing – Postman & JWT_Tool
- Advanced Exploits – Metasploit & W3af
Web Application Penetration Testing Tools
Here’s a closer look at how each penetration testing tool contributes to a successful pentest:
1. Nmap & Gobuster (Reconnaissance)
Nmap is the go-to tool for discovering open ports, services, and hosts. With flags like -sC (default scripts) and -sV (version detection), it reveals the network’s attack surface—like an x-ray for your infrastructure.
Gobuster, written in Go, brute-forces web server directories, files, subdomains, and virtual hosts. It’s lightweight, fast, and deadly effective for uncovering hidden content that attackers often exploit.
2. OWASP ZAP & Nikto (Vulnerability Scanning)
OWASP ZAP is the world’s most widely used web app scanner. Acting as a proxy, it intercepts traffic between the browser and server. With passive and active scanning modes, it identifies XSS, misconfigurations, insecure cookies, and more.
Nikto is straightforward and powerful. It scans web servers for 6,700+ known vulnerabilities, outdated software, misconfigurations, and dangerous files. It’s perfect for quick, targeted assessments at the server layer.
3. Burp Suite & SQLmap (Exploitation)
Burp Suite is an industry standard. Its modular tools—Proxy (to intercept), Repeater (to modify), Intruder (to brute-force), and Scanner (to automate discovery)—make it indispensable for manually probing and exploiting web applications.
SQLmap automates the discovery and exploitation of SQL injection flaws. Supporting six different injection techniques, it works with over 30 database types, making it ideal for uncovering deep-seated database vulnerabilities.
4. Postman & JWT_Tool (API Testing)
Postman is more than an API client—it’s a powerful testing platform. It allows you to explore endpoints, test authentication mechanisms, and identify security flaws in modern APIs.
JWT_Tool focuses on JSON Web Tokens. It validates, modifies, and exploits JWTs to test for flaws like signature bypasses, algorithm tampering, and known CVEs (e.g., CVE-2015-2951, CVE-2022-21449).
5. Metasploit & W3af (Advanced Exploits)
Metasploit Framework is a comprehensive exploitation engine. It supports a vast collection of exploits, payloads, and evasion techniques across multiple platforms, enabling both offensive testing and post-exploitation simulation.
W3af (Web Application Attack and Audit Framework) is plugin-driven and identifies over 200 vulnerabilities. Its integrated approach—Discovery, Audit, and Exploit—makes it a solid tool for full-scope web app testing.
Bottom line: Mastering these twelve tools gives you everything you need across recon, scanning, exploitation, and API testing. But remember—tools don’t do the job. Skilled testers do.
Types of Web Application Penetration Testing Services
Here’s the deal: not all penetration tests are created equal. The type of testing service you choose directly affects what you’ll find—and what you might miss. Here’s how the most common types stack up:
1. Black Box, White Box, and Gray Box Testing
These define how much internal knowledge the tester has before starting:
-
Black Box Testing – Testers have zero internal access. They simulate external hackers trying to break in with no credentials or code visibility.
-
White Box Testing – Full transparency. Testers get access to source code, architecture documents, and credentials—ideal for code-level vulnerability hunting.
-
Gray Box Testing – A hybrid approach. Testers get partial knowledge (e.g., login access) to simulate an attacker who already has limited insider privileges. Often the most efficient and realistic choice.
2. Internal vs. External Penetration Testing
This defines where the simulated attack originates:
-
Internal Penetration Testing – Simulates an attacker who’s already inside your network, like a rogue employee or a hacker who breached another system. Internal networks typically contain 3x more exploitable flaws than external ones.
-
External Penetration Testing – Focuses on publicly accessible systems (like websites, APIs, and cloud portals). This is the go-to test for identifying internet-facing risks.
3. Static vs. Dynamic Application Security Testing (SAST vs. DAST)
These define when and how your application is tested:
-
SAST (Static Testing) – Analyzes source code without executing it. Useful for finding security bugs early in the development process.
-
DAST (Dynamic Testing) – Scans your live application as it runs. Ideal for spotting vulnerabilities that emerge during real-world execution.
4. Client-Side and API Security Testing
These are focused services tailored to specific components:
-
Client-Side Testing – Targets browser-based risks like DOM-based XSS, JavaScript injection, and redirect logic flaws.
-
API Security Testing – Evaluates REST or GraphQL APIs for broken authentication, weak rate limiting, improper input validation, and insecure token handling (e.g., JWT or OAuth).
Choose wisely. Your security depends on it.
Best Practices for Web Application Security Testing
Here's the deal: Most security testing programs fail because they're poorly planned and executed. You can't just throw some tools at your applications and hope for the best.
These proven practices will dramatically improve your security outcomes—no guesswork required.
Combining Manual and Automated Testing Approaches
The most effective web application pentesting combines human insight with machine efficiency. Organizations using a hybrid approach identify 43% more vulnerabilities than those relying solely on automated tools.
Here's why this combo works:
- Automated testing handles repetitive tasks, consistency, and speed
- Manual testing provides creative problem-solving and business context understanding
- Human testers find issues in unscripted scenarios that automated tools miss
To maximize this combination, coordinate your testing strategy under one leader, share goals across teams, and use standardized naming conventions across all tests.
Following OWASP and NIST Testing Frameworks
Don't reinvent the wheel. Industry-standard frameworks provide structured, proven approaches:
- The OWASP Web Security Testing Guide offers hands-on guidance for finding common vulnerabilities
- NIST 800-115 delivers recommendations for designing and implementing security test processes
- The Penetration Testing Execution Standard (PTES) defines a 7-phase methodology from pre-engagement through reporting
These frameworks ensure your testing program addresses all critical vulnerability categories systematically.
Integrating Security into CI/CD Pipelines
Catch vulnerabilities at the pace they're introduced. Key implementation steps:
- Map how code moves from development to release
- Place each test where it can help most—some checks belong near the developer's keyboard, others later in the pipeline
- Connect security findings to the same issue trackers developers already use
Using PTaaS for Continuous Security Validation
Penetration Testing as a Service (PTaaS) combines manual expertise with automated scanning for ongoing protection. This approach enables:
- Testing on demand rather than just annual assessments
- Real-time vulnerability identification
- Continuous security validation against evolving threats
Prioritizing Business Logic and API Vulnerabilities
Business logic flaws remain largely invisible to automated scanners yet can completely undermine application security. Similarly, APIs represent critical attack surfaces that require specialized testing.
Focus on:
- Testing application workflows against misuse cases
- Validating that business rules are properly enforced
- Assessing API authentication, authorization, and rate limiting
Final Thoughts on Web App Pentesting Strategy
Here’s the deal: your web apps are under attack—right now. While you’re reading this, someone’s scanning for that one weak point to exploit. This isn’t fearmongering—it’s reality.
The good news? You don’t have to stay on defense. Web application penetration testing flips the game—you find the vulnerabilities before attackers do. Think of it as a fire drill that actually prevents the fire.
The strategy we outlined—planning, recon, scanning, exploitation, reporting—isn’t just best practice. It’s how you stay ahead. The real risk isn’t one flaw—it’s how multiple flaws connect to become a full-blown breach.
Your toolkit matters too. Nmap, Burp Suite, OWASP ZAP—these tools are more than names. They're your digital perimeter, each one built for a specific purpose.
And the type of testing matters. Black box mimics outsiders. White box uses insider knowledge. Gray box hits the balance—making it ideal for most teams.
Security isn't an annual event anymore. It’s a continuous process, embedded in how you build.
You’ll be targeted. That’s not a question.
The only question is—will you be ready?
#nothingtohide
Frequently Asked Questions

Robin Joseph
Senior Security Consultant
