0%
In 2023, nearly half of UK businesses reported a cyberattack. According to reports from AAG, this isn’t an outlier—it’s proof of how exposed today’s organisations really are.
Cybercrime has evolved beyond opportunistic hacks. Attacks are now engineered, precise, and relentless. The forces driving this rise? Breakneck technological growth, the flood of digital-first startups that prioritize speed over security, and adversaries who exploit even the smallest oversight. In this environment, one missed patch or weak configuration can open the door to devastating breaches.
Enter vulnerability scanning—the discipline built to find weaknesses before attackers do. At its core, it’s an ongoing process of testing and monitoring your IT infrastructure for cracks. Automated scans sweep through servers, applications, and networks, while manual checks add context and accuracy. Together, they give businesses visibility into risks that might otherwise remain hidden until it’s too late.
This blog unpacks what vulnerability scanning is, why it’s more than a compliance checkbox, and how it helps organizations shift from firefighting to prevention. Because in security, knowing where you’re vulnerable is the first step to building true resilience.
Vulnerability scanning is the process of systematically inspecting your network, systems, and applications for weaknesses that could be exploited by attackers. Think of it as a digital health check—automated tools probe your infrastructure, flagging known vulnerabilities, misconfigurations, and gaps in compliance with security policies or industry standards. The goal isn’t just to generate a list of flaws but to give organisations the visibility they need to fix issues before they spiral into breaches.
Here’s a simple way to picture it. Imagine a retail giant gearing up to launch its new e-commerce platform. Excitement is high—customers are waiting, payments will be processed, and sensitive data will flow across servers. But before the launch, the security team runs a vulnerability scan. Within minutes, the scan uncovers outdated software libraries, weak access controls, and a misconfigured server that could expose credit card details. By addressing these issues early, the company prevents attackers from finding them first.
At its core, vulnerability scanning is about anticipation. It’s a proactive defense that shines a light on risks you didn’t know were there—so your security team can close doors before adversaries try to break through.
Did you know? PCI DSS demands that an organization that stores, processes, or transmits information related to cardholders digitally should run internal and external vulnerability scans periodically (according to Requirement 11.2 from PCI DSS)
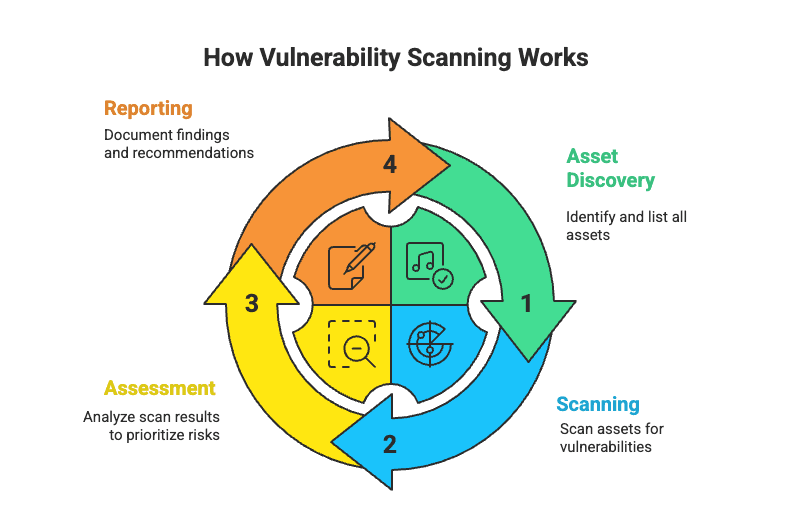
Vulnerability scanning isn’t guesswork—it’s a structured process that uses specialised tools to simulate real-world attacks on your systems. Instead of waiting for a hacker to find weak points, scanners methodically test your environment to expose them first. Here’s how the process unfolds:
The first step is visibility. Scanning tools sweep through your environment, cataloguing every device, server, application, and database. You can’t protect what you don’t know exists, and asset discovery ensures no shadow systems slip under the radar.
Once assets are identified, the tool checks them against a constantly updated database of known vulnerabilities. This includes missing patches, misconfigurations, outdated software versions, and unsafe default settings—all common attack vectors.
Not every flaw is equal. During this stage, issues are prioritised based on severity and business impact. A critical vulnerability on a payment server, for instance, will be treated as far more urgent than a low-risk misconfiguration on an internal test machine.
Finally, the scanner compiles its findings into a detailed report. Vulnerabilities are grouped by severity, and remediation steps are laid out clearly, giving security teams a roadmap for patching and hardening their defences.
Vulnerability scans can be run across operating systems, applications, network devices, and databases—ensuring nothing is left unchecked. At its core, the process is about transforming unknown risks into clear, actionable priorities. That visibility is the foundation of stronger, proactive security.
How Vulnerability Scanning Works
Vulnerability scanning is more than just running a tool and checking boxes. When done consistently, it gives organisations a clear picture of where they stand—what’s secure, what’s weak, and where attackers might strike next. The process works best as an ongoing cycle of discovery, testing, and remediation, ensuring your defences evolve as quickly as threats do.
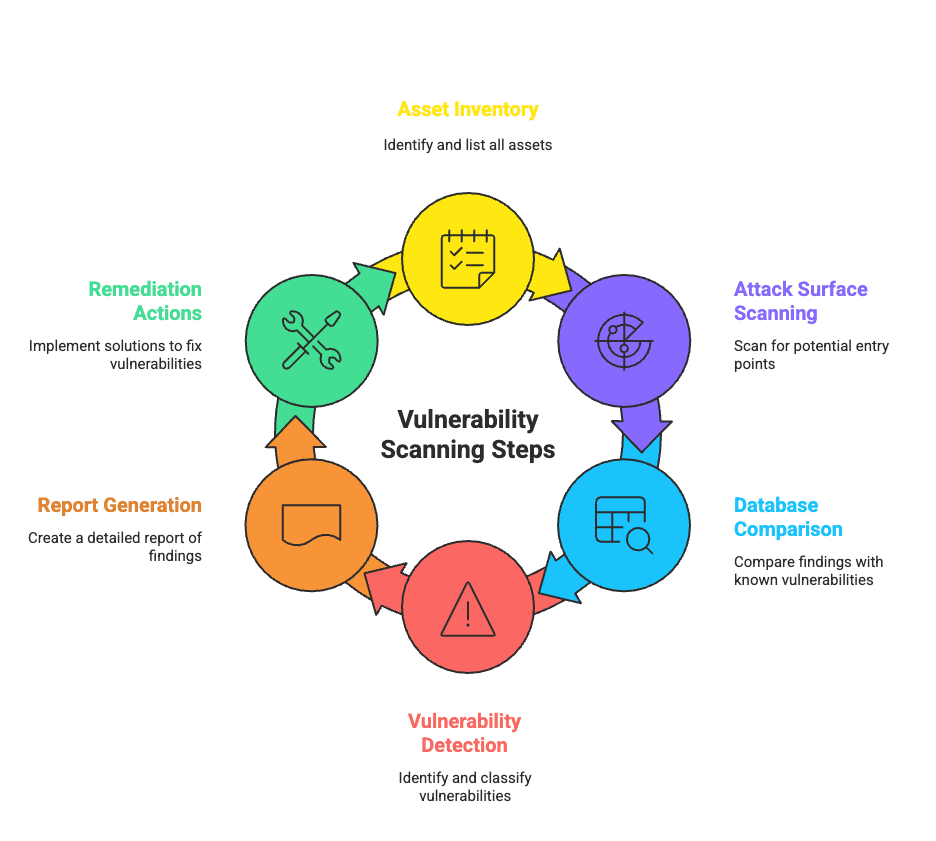
The journey typically follows six core steps:
Let’s go into each step and see how they fit together.
The first step is visibility. Every device, server, application, and database connected to the network must be identified. This includes details like operating systems, ports, and user accounts. Without this inventory, hidden or “shadow IT” assets can become blind spots attackers love to exploit.
With assets mapped, the scanner probes them for weaknesses. This includes outdated software, misconfigured firewalls, or open ports that shouldn’t exist. It’s about uncovering every possible door an attacker might try to open.
Findings are matched against databases like CVE (Common Vulnerabilities and Exposures). For example, if an unpatched Apache server is detected, the scanner links it to known exploits, highlighting how attackers could use it to gain entry.
Not all flaws carry the same weight. Classification assigns severity levels—critical, high, medium, or low—so teams know which vulnerabilities pose the biggest risks to business operations.
All findings are then distilled into clear reports. These outline vulnerabilities, rank them by severity, and recommend remediation steps, turning raw scan data into actionable guidance for IT and security teams.
Finally comes action—patching outdated systems, updating software, reconfiguring permissions, or adding extra security layers. The goal is simple: close gaps before adversaries exploit them.
Vulnerability Scanning Steps
Together, these six steps ensure vulnerability scanning isn’t just a technical process—it’s a disciplined, repeatable defence strategy that strengthens resilience against real-world threats.
The real value of vulnerability scanning lies not just in uncovering issues but in how those findings are applied to strengthen defences. Each scan delivers a set of insights that give organisations a sharper view of their security posture and the risks hiding within it.
Identified Vulnerabilities: A catalogue of flaws within systems, applications, or devices.
Risk Levels: Each vulnerability is ranked by severity, helping security teams prioritise what needs immediate attention.
Configuration Issues: Misconfigured settings—like open ports or weak permissions—that expand the attack surface unnecessarily.
Compliance Status: A snapshot of how closely the organisation aligns with security frameworks and regulatory standards.
But these results aren’t just technical findings—they’re action items. Their power comes from how they’re put to use.
Regular Security Assessments: Routine scans highlight new vulnerabilities introduced by system updates, infrastructure changes, or overlooked assets.
Pre-Deployment Checks: Before launching a new app or feature, scans ensure no critical flaws slip through, reducing the risk of costly fixes post-release.
Compliance Auditing: Scanning validates adherence to regulations like PCI DSS or HIPAA, offering evidence for audits while reducing liability.
Incident Response: After a breach, scans help identify weak points that attackers may have exploited, guiding immediate corrective measures.
Taken together, the results and their applications transform vulnerability scanning into more than a routine task. It becomes a feedback loop—where detection leads to action, and action leads to stronger, more resilient security over time.
Not all vulnerability scans are the same. Different environments, assets, and risks demand different approaches. By understanding the major types of scans, organisations can choose the right method for the right scenario—ensuring no blind spot is left unchecked.
Focuses on systems inside the organisation’s network, detecting threats that could be exploited by insiders or malware that has already breached the perimeter.
Targets internet-facing assets—websites, servers, APIs—to uncover vulnerabilities visible to external attackers.
Uses valid credentials to simulate a trusted user, offering deeper visibility into misconfigurations and permission-related flaws.
Performed without credentials, it mimics the perspective of an outsider probing for weak points.
Takes a broad view, combining different techniques to evaluate overall security posture across multiple assets.
Maps connected devices and applications, helping detect shadow IT or unmanaged systems.
Validates whether systems align with regulatory requirements like PCI DSS, HIPAA, or ISO 27001.
Zeroes in on individual machines, checking software versions, patches, and configurations.
Reviews network infrastructure, identifying active hosts and open ports as potential entryways.
Detects common flaws in web apps—like SQL injection or cross-site scripting—before attackers do.
Discovers open ports and the services tied to them, exposing possible attack surfaces.
Examines databases for insecure configurations or unpatched vulnerabilities that could put sensitive data at risk.
Analyses application code during development to catch flaws early.
Assesses cloud infrastructure for misconfigurations and risks unique to hybrid or multi-cloud setups.
Taken together, these scanning methods provide a layered defense strategy. No single type covers everything—but in combination, they give organizations the visibility and precision needed to anticipate threats and secure what matters most.
Vulnerability scanning is a cornerstone of modern cybersecurity, but running a scan is only half the battle. Turning results into meaningful action comes with its own set of hurdles. Here are some of the most common challenges organizations face:
Scanners sometimes raise alarms on harmless issues or, worse, miss real vulnerabilities. Both outcomes can waste resources and create blind spots.
Hybrid setups—mixing cloud, on-premises, and remote systems—make it hard to capture a full, accurate picture of risks.
Full-scale scans consume bandwidth and system resources, often slowing operations if not scheduled during low-traffic windows.
Without experienced cybersecurity professionals, scan results may be misunderstood or remediation delayed.
When hundreds of vulnerabilities appear, teams can struggle to decide what to fix first, leaving critical flaws unaddressed.
Connecting scanning tools with SIEMs, patching systems, and ticketing workflows is often more complicated than expected.
Fixing vulnerabilities—especially in legacy systems—requires time, coordination, and sometimes significant rework.
These challenges don’t diminish the importance of vulnerability scanning—they underscore it. By anticipating these obstacles, organisations can design smarter processes that turn scans into meaningful defence, not just reports.
Running vulnerability scans is only valuable if the process is structured, consistent, and actionable. To get the most out of scanning, organisations can follow these best practices:
Keep a living inventory of every device, system, and application on your network. Network scanners and lightweight agents help ensure no hidden asset becomes a blind spot.
Not all systems require the same attention. Critical assets—like payment servers or customer databases—should be scanned weekly or monthly. Less critical systems can be checked quarterly.
Assign clear accountability. Every asset should have an owner responsible for scheduling scans, reviewing results, and driving remediation.
Use frameworks like CVSS to score severity and focus on vulnerabilities that are critical or currently being exploited in the wild.
Create reports that do more than dump data. They should highlight severity levels, suggest remediation paths, and remain digestible for both technical teams and business leaders.
Develop a repeatable workflow for patching, updating, or reconfiguring systems. Follow up with rescans to confirm fixes.
Fine-tune scanning tools, apply filters, and keep signatures updated to reduce noise and spotlight genuine risks.
Effective vulnerability scanning isn’t just about finding flaws—it’s about building a disciplined cycle that turns detection into meaningful protection.
Scanning finds risks. But it doesn’t tell the full story. Uproot Security fills the gaps with specialized penetration testing across web apps, mobile apps, cloud, networks, and source code—showing you how attackers could actually break in.
We go beyond alerts with:
With Uproot, you get clarity—not just scan results.
Talk to our team to get started.
In today’s threat landscape, standing still is the fastest way to fall behind. Vulnerability scanning isn’t just another checkbox on a compliance form—it’s the frontline discipline that helps organisations spot cracks before attackers slip through them. From mapping every asset to uncovering misconfigurations to prioritising the flaws that matter most, scanning transforms uncertainty into clarity.
But clarity alone doesn’t stop breaches. What makes scanning powerful is what happens next—the remediation, the ownership, and the discipline of treating it as a continuous cycle, not a one-off event. Pairing strong scanning practices with best-in-class remediation and, where needed, expert penetration testing builds resilience layer by layer.
Cybercrime is fast, relentless, and opportunistic. That means security teams must be faster, smarter, and more proactive. The businesses that thrive will be the ones that see vulnerability scanning not as an obligation, but as an opportunity—a chance to anticipate risks, strengthen defences, and prove that prevention always beats reaction.
At the end of the day, resilience isn’t about being unbreakable—it’s about refusing to be caught unprepared.

Senior Pentest Consultant