0%
46% of all cyberattacks hit businesses with fewer than 1,000 employees, according to Verizon’s Data Breach Investigations Report. That’s nearly half the attacks zeroing in on companies that often don’t have the same level of defenses as global giants. And when customer trust and compliance are on the line, the impact can be devastating.
That’s where SOC 2 penetration testing comes in. Unlike generic security assessments, SOC 2 pentesting isn’t just about finding holes—it’s about proving you’re aligned with compliance-driven trust principles. It’s designed to test how well your systems actually hold up under attack, while also ensuring you’re living up to the expectations of auditors, customers, and regulators.
In today’s threat landscape, protecting customer data isn’t optional—it’s the baseline. With cloud adoption, SaaS models, and third-party integrations expanding your attack surface, SOC 2 penetration testing helps validate that your defenses match the promise of your policies.
This blog breaks down 10 things you need to know about SOC 2 penetration testing—what it is, why it matters, and how it can make or break your compliance journey.
SOC 2 penetration testing isn’t just a routine security check—it’s a reality check. It’s a controlled simulation of cyberattacks designed to test your defenses against real-world threats, with one critical difference: it’s aligned with SOC 2 compliance. Every test, finding, and recommendation ties directly to how well your organization protects customer data under the SOC 2 framework.
SOC 2—short for System and Organization Controls 2—is the leading standard for service providers handling sensitive customer information. It’s built around the Trust Services Criteria (TSC), which focus on security, availability, processing integrity, confidentiality, and privacy. SOC 2 penetration testing evaluates your systems through this lens, ensuring you’re not just compliant on paper but resilient in practice.
Here’s what it delivers:
Risk identification: Finds weaknesses attackers could exploit, from misconfigured cloud storage to insecure APIs.
Compliance validation: Proves that your controls work under pressure, not just in documentation.
End-to-end evaluation: Covers web apps, networks, cloud environments, and third-party systems.
Stakeholder confidence: Demonstrates to clients, auditors, and investors that security and compliance are taken seriously.
In short, SOC 2 penetration testing bridges the gap between compliance and real-world security, turning policies into actionable proof of defense.
SOC 2 penetration testing isn’t just a compliance checkbox—it’s a reality check for your security. Here’s why it matters:
Expose Critical Vulnerabilities: Identifies weaknesses attackers could exploit in applications, APIs, cloud environments, and networks.
Test Real-World Resilience: Goes beyond documentation to validate how your systems perform under realistic attack scenarios.
Ensure Availability: Highlights risks that could trigger downtime or service disruptions, directly supporting business continuity.
Prove Commitment to Security: Demonstrates to clients, investors, and partners that your security controls are actively tested and reliable.
Strengthen Trust: Builds confidence in your organization’s ability to protect sensitive customer data, reinforcing loyalty and credibility.
Stay Ahead of Threats: Helps you act proactively before minor vulnerabilities escalate into costly breaches or operational issues.
In short, SOC 2 penetration testing bridges the gap between compliance and real-world security, delivering confidence, protection, and stakeholder assurance.
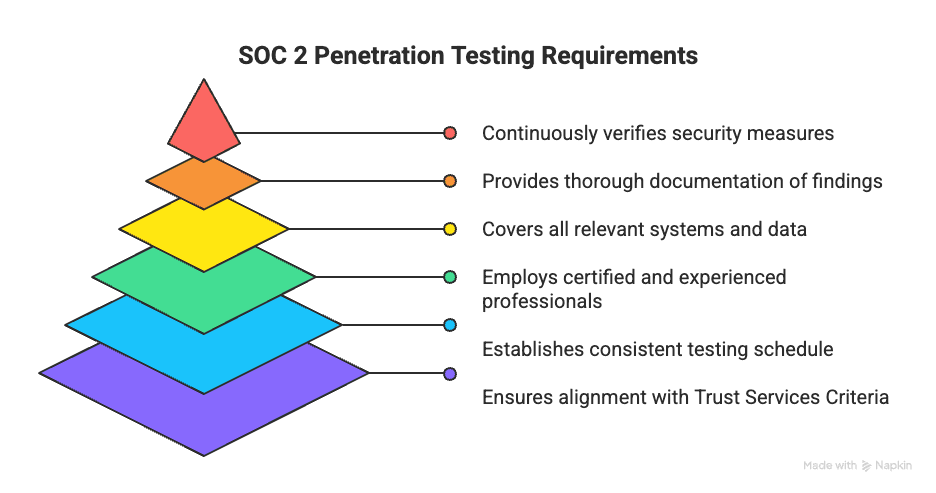
SOC 2 penetration testing isn’t just a routine exercise—it’s a structured process built to align with the Trust Services Criteria (TSC). The TSC, developed by the Assurance Services Executive Committee (ASEC) of the AICPA, sets the foundation for evaluating how well your controls actually protect sensitive data. At its core, it focuses on five pillars: security, availability, processing integrity, confidentiality, and privacy.
To meet SOC 2 expectations, penetration testing should follow these requirements:
Alignment with TSC: Every test must map back to the five trust principles, ensuring your systems safeguard data in storage, transit, and processing.
Regular testing cadence: While SOC 2 doesn’t dictate a fixed frequency, most organizations run tests annually—or after major infrastructure changes, new deployments, or emerging threats.
Qualified testers only: Testing must be conducted by certified professionals, whether internal experts or external firms, to ensure accuracy and credibility.
Comprehensive scope: Web apps, APIs, cloud environments, and supporting infrastructure should all be included to capture every potential entry point.
Detailed reporting: Findings must outline vulnerabilities, their severity, and practical remediation steps. Clear evidence of testing and fixes becomes a key artifact for SOC 2 audits.
Ongoing validation: Reports should not sit on a shelf—they’re living proof of your organization’s continuous effort to strengthen controls.
When done right, SOC 2 penetration testing doesn’t just satisfy auditors. It creates a defensible record that your organization takes data security seriously, keeps systems resilient, and aligns with industry best practices at every level.
SOC 2 Penetration Testing Requirements
SOC 2 penetration testing isn’t one-size-fits-all. The scope defines exactly what’s tested, making sure audit and security goals line up. A well-defined scope usually includes:
Web Applications & APIs: Any interface handling customer data or internal processes.
Networks & Infrastructure: Servers, firewalls, and cloud environments powering critical services.
Third-Party Integrations: Vendor or partner systems that could open doors to attackers.
Access Controls & Authentication: How roles, permissions, and identity management are enforced.
Data Storage & Transmission: Encryption, backups, and handling of sensitive data in motion and at rest.
A clear scope closes blind spots, keeps testing focused on high-risk areas, and gives auditors concrete proof that your controls were validated end-to-end. Every element tested becomes a confidence-building checkpoint for compliance and security.
SOC 2 penetration testing isn’t just a technical exercise—it’s a balancing act between compliance, security, and operational realities. Organizations that don’t anticipate challenges risk incomplete assessments, wasted resources, or gaps in protection. Understanding common hurdles and addressing them upfront ensures your pentesting is effective and audit-ready.
Defining the right scope is critical—and surprisingly tricky. Too narrow, and you miss vulnerabilities; too broad, and you dilute focus and waste time. A well-scoped test targets high-risk systems, processes, and data flows, aligning with SOC 2 priorities without overextending resources.
SOC 2 pentesting is compliance-driven, but focusing solely on ticking boxes can leave real-world threats unaddressed. Organizations must strike a balance, ensuring that tests validate control effectiveness while also identifying vulnerabilities outside the explicit Trust Services Criteria.
The threat landscape evolves faster than many traditional testing methodologies. New attack vectors, zero-day vulnerabilities, and API weaknesses appear constantly. Effective SOC 2 pentesting integrates the latest threat intelligence and attack simulations to stay ahead of attackers.
Finding testers who understand both cybersecurity and SOC 2 compliance is challenging. The skill set is specialized, and demand often exceeds supply. Engaging experienced third-party experts helps fill this gap, bringing both technical and compliance expertise.
Comprehensive SOC 2 testing requires time, expertise, and tools. Limited budgets can lead to shallow assessments or missed vulnerabilities. Prioritizing critical assets and leveraging external partners can optimize resources without sacrificing coverage.
Navigating these challenges proactively ensures your SOC 2 penetration testing is thorough, actionable, and aligned with both compliance and real-world security needs.
SOC 2 penetration testing only delivers value when the right people run it—and at the right time. Not every tester is qualified. To make your SOC 2 compliance meaningful, you need a mix of deep technical security expertise and a solid understanding of SOC 2 requirements. Without both, findings can be incomplete, inaccurate, or even misleading during audits.
Look for testers with recognized certifications like:
Independence matters. Internal teams may know your environment too well, creating blind spots or assumptions that leave vulnerabilities unchecked. An independent third-party testing firm brings objectivity, credibility with auditors, and real-world attack simulation—proving your SOC 2 controls hold up under scrutiny.
Timing is just as critical as expertise. SOC 2 pentesting should follow a strategic rhythm:
At least once a year to demonstrate ongoing commitment to compliance.
After major system changes—new deployments, infrastructure updates, or application overhauls—when potential risks emerge.
Post-incident, including breaches, intrusion attempts, or suspicious activity, to confirm that fixes worked and no hidden vulnerabilities remain.
Think of it as both preventive maintenance and proof of resilience. The right testers, at the right time, ensure your controls aren’t just documented—they’re battle-tested, audit-ready, and trustworthy.
Both SOC 2 and regular penetration testing aim to uncover vulnerabilities—but their goals and scope differ. SOC 2 pentesting is compliance-driven, zeroing in on systems and processes that prove your controls align with the Trust Services Criteria. Regular penetration testing, meanwhile, takes a broader, more exploratory approach, probing networks, applications, and infrastructure for weaknesses attackers could exploit.
Here’s how they stack up side by side:
| Aspect | SOC 2 Penetration Testing | Regular Penetration Testing |
|---|---|---|
| Purpose | Compliance with SOC 2 and Trust Services Criteria. | Strengthen overall security with proactive vulnerability detection. |
| Scope | Systems and processes under SOC 2 mandates. | Networks, applications, and infrastructure across the business. |
| Focus Areas | Encryption, access control, and compliance-aligned controls. | Insecure APIs, misconfigurations, outdated software, and more. |
| Methodology | Follows compliance frameworks (e.g., NIST, OWASP). |
The takeaway? SOC 2 penetration testing helps you pass the audit and prove compliance. Regular pentesting helps you get ahead of attackers by hardening your defenses everywhere. Together, they cover both the letter of compliance and the reality of security.
SOC 2 penetration testing only delivers value when it’s done the right way. A structured, thoughtful approach not only uncovers vulnerabilities but also strengthens your compliance posture and streamlines audits. Here’s how to get it right.
Security isn’t static, and neither should your testing be. Regular pentests catch new vulnerabilities before they can be exploited. Annual tests are the baseline, but additional tests after system changes or incidents help keep your defenses up to date.
A pentest is only as effective as its scope. Define it clearly and align it with your SOC 2 processes and systems. Cover web applications, APIs, cloud environments, and infrastructure—anywhere an attacker could gain a foothold.
Finding vulnerabilities is essential—but it’s not the whole picture. SOC 2 pentesting should also evaluate how well your security controls and incident response processes perform under pressure. Objectives should be specific, measurable, and tied to compliance goals.
External testers bring fresh eyes and unbiased perspectives. Internal teams, familiar with your environment, may overlook obvious flaws. Third-party experts simulate real-world attacks more effectively and lend credibility to your audit.
Reports are more than a formality—they’re your evidence. Detailed documentation of findings, severity, remediation steps, and compliance mapping simplifies audits and demonstrates that your organization takes data protection seriously.
Following these best practices ensures SOC 2 penetration testing is more than a checkbox—it becomes a strategic tool for resilience, compliance, and trust.
Short answer: Not exactly—but it might as well be.
SOC 2 doesn’t spell out “you must run penetration tests.” Instead, it focuses on the Trust Services Criteria—security, availability, processing integrity, confidentiality, and privacy. Auditors aren’t impressed by policies sitting on a shelf—they want proof your controls actually work in the real world.
Here’s the reality: if your systems handle sensitive customer data, you need to demonstrate that vulnerabilities are actively identified and remediated. That’s where penetration testing comes in. By simulating real-world attacks, it shows that your security controls aren’t just documented—they hold up under pressure.
Skip it, and auditors may question whether your defenses are effective. A pentest isn’t just a “nice-to-have.” It’s a practical, audit-ready step to prove compliance, secure sensitive data, and reinforce trust with clients, partners, and stakeholders.
Bottom line: SOC 2 may not explicitly mandate penetration testing, but any organization serious about compliance treats it as essential.
Here’s the deal: SOC 2 doesn’t list vulnerability scanning as a hard rule, but auditors expect to see it in action.
SOC 2 is all about proving that your controls actually protect sensitive data. Policies on a shelf won’t impress anyone—auditors want evidence that you’re actively finding and fixing weaknesses. That’s where vulnerability scanning fits in.
Regular scans catch misconfigurations, outdated software, and known exploits—the easy targets attackers love. Running them consistently shows auditors that your systems are being monitored, risks are prioritized, and vulnerabilities don’t linger.
Scans aren’t enough on their own. Most organizations pair them with penetration testing. Scans spot the obvious issues, while pentests dig deeper, simulating real-world attacks to uncover hidden weaknesses. Together, they give a clear, audit-ready view of your security posture.
Bottom line: SOC 2 may not explicitly require vulnerability scans, but skipping them is risky. They’ve become a de facto expectation for any organization serious about compliance and protecting customer data.
Selecting the right penetration testing partner can make or break your SOC 2 compliance journey. Here’s what to keep in mind:
External Expertise Matters: Third-party vendors bring an outsider’s perspective, simulating attacks the way real threat actors would. Internal teams are familiar with your systems, which can create blind spots.
Deep Technical and Compliance Knowledge: The ideal partner blends cybersecurity expertise with a solid understanding of SOC 2 requirements. They don’t just find vulnerabilities—they evaluate control effectiveness against the Trust Services Criteria.
Actionable Insights, Not Just Reports: Look for partners who provide detailed recommendations, remediation strategies, and practical guidance. Reports should translate findings into actions your team can implement immediately.
Audit Readiness Support: A strong partner ensures your testing aligns with SOC 2 audit expectations. Their documentation and methodology should make the auditor’s job easier and demonstrate compliance without friction.
Strategic Security Planning: Beyond identifying gaps, the right vendor helps you strengthen your overall security posture, prioritize critical assets, and reduce future risk exposure.
Choosing the right penetration testing partner isn’t just about running tests—it’s about building trust, credibility, and a resilient security foundation that supports compliance and business growth.
When it comes to SOC 2 compliance, you need more than just a penetration test—you need confidence. UprootSecurity delivers exactly that. Our team combines the expertise of the top 100 ethical hackers worldwide with a compliance-first approach, ensuring your security controls not only meet but exceed industry benchmarks.
We don’t just find vulnerabilities. We provide actionable insights, practical remediation suggestions, and full compliance mapping—all packaged in a single, comprehensive report. Every detail is designed to simplify your SOC 2 audit process, strengthen your security posture, and give stakeholders tangible proof that customer data is protected.
Partnering with UprootSecurity means proactive defense, reduced audit stress, and a stronger reputation in the eyes of clients, partners, and regulators.

Senior Pentest Consultant
| Simulates real-world attack scenarios with exploratory techniques. |
| Deliverables | Compliance-focused report for SOC 2 audits. | Technical report detailing vulnerabilities, risks, and remediation steps. |
| Frequency | Typically annual or during audit cycles. | Ad-hoc or periodic, based on business needs. |