0%
Trust is the currency of modern business—and security is how you earn it. Nearly 87% of customers won’t work with companies they don’t trust to protect their data. That’s why a SOC 2 compliance checklist is no longer optional for growing organizations.
Preparing for your first SOC 2 audit can feel overwhelming. SOC 2 is a voluntary framework developed by the AICPA, but in practice, it’s often driven by buyer expectations. Customers and partners increasingly demand proof that your security controls aren’t just documented, but actually working. With organizations investing heavily in privacy and security programs, getting SOC 2 right matters more than ever.
This guide cuts through the noise. It explains SOC 2 in practical terms—what it requires, how the five Trust Services Criteria apply, and what auditors actually look for. You’ll also learn the difference between SOC 2 Type 1 and Type 2 audits, and how to prepare step by step without overcomplicating your security program.
Consider this your clear, actionable roadmap to SOC 2 compliance—built for teams tackling it for the first time.
A SOC 2 compliance checklist is a practical roadmap that turns SOC 2 requirements into actionable steps. It ensures your organization meets the Trust Services Criteria—security, availability, processing integrity, confidentiality, and privacy—by guiding controls, policies, and processes.
The checklist covers access management, risk assessments, staff training, internal monitoring, and evidence collection. For first-time audits, it helps identify gaps before auditors arrive, assigns responsibilities across your team, and simplifies preparation for both Type 1 and Type 2 audits.
In short, it transforms compliance from a vague requirement into a clear, structured process that builds trust and credibility.
A SOC 2 compliance checklist is built around the Trust Services Criteria (TSC)—five pillars that define auditable security practices. Security is mandatory, while Availability, Processing Integrity, Confidentiality, and Privacy are optional, depending on your services and client needs. Understanding these criteria helps you design controls that satisfy both auditors and customers.
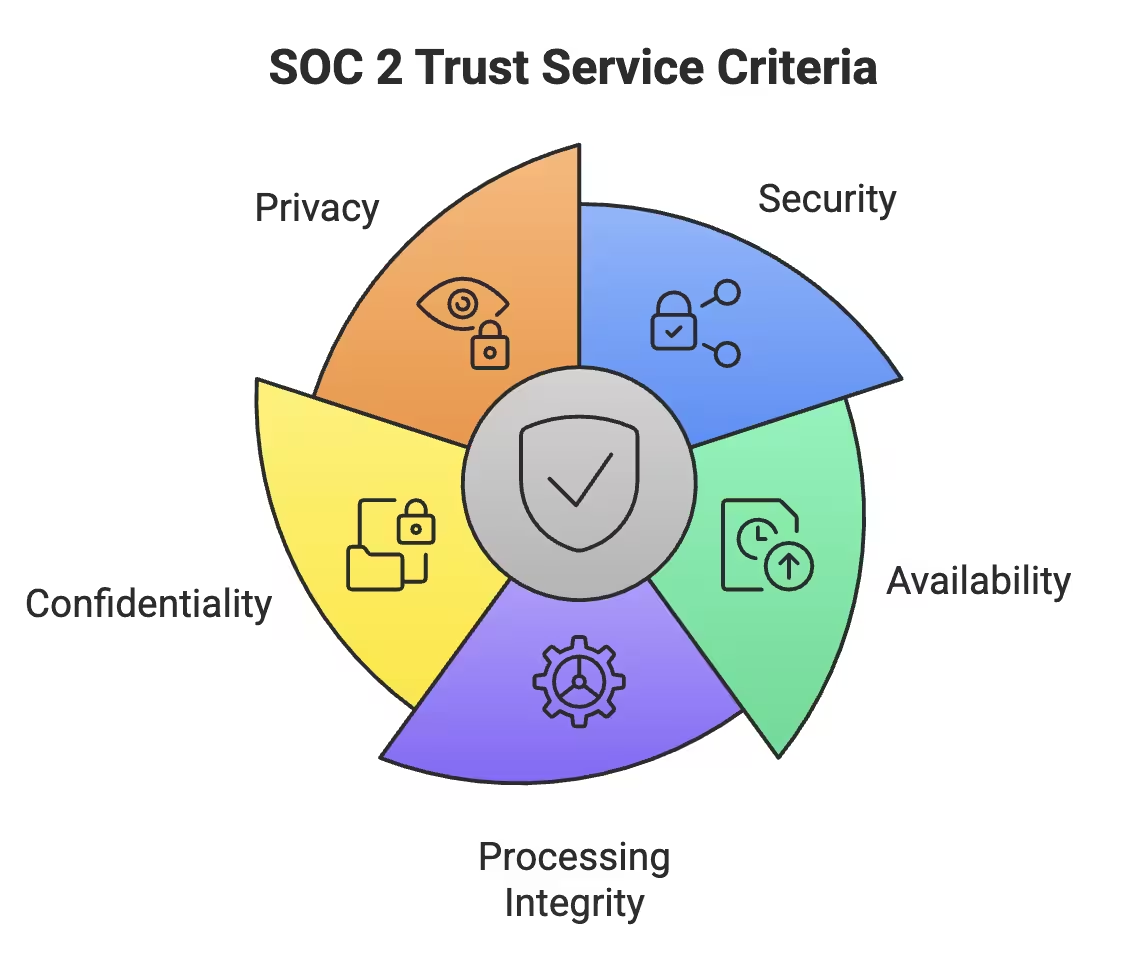
SOC 2 Trust Service Criteria
Security ensures systems are protected against unauthorized access and damage. Key points include:
This ensures only authorized users access critical systems and builds a strong security foundation.
Availability measures system reliability and uptime. Organizations should:
Reliable systems keep services running as promised, reducing disruptions and building trust.
Processing Integrity ensures accurate and timely data processing. Controls include:
Accurate and consistent data processing strengthens operational confidence and audit readiness.
Confidentiality protects sensitive business information. Organizations should:
Protecting sensitive data safeguards your business and maintains client trust.
Privacy governs personal data management. Key points include:
Proper privacy practices show respect for personal data and reinforce credibility with clients.
By applying all five Trust Services Criteria, organizations can create a SOC 2 checklist that passes audits and strengthens overall security and trustworthiness.
Passing your first SOC 2 audit isn’t about doing everything at once—it’s about doing the right things in the right order. A SOC 2 compliance checklist breaks a complex audit into manageable, auditable steps so your team stays proactive instead of reactive.
At a high level, your SOC 2 checklist follows these steps:
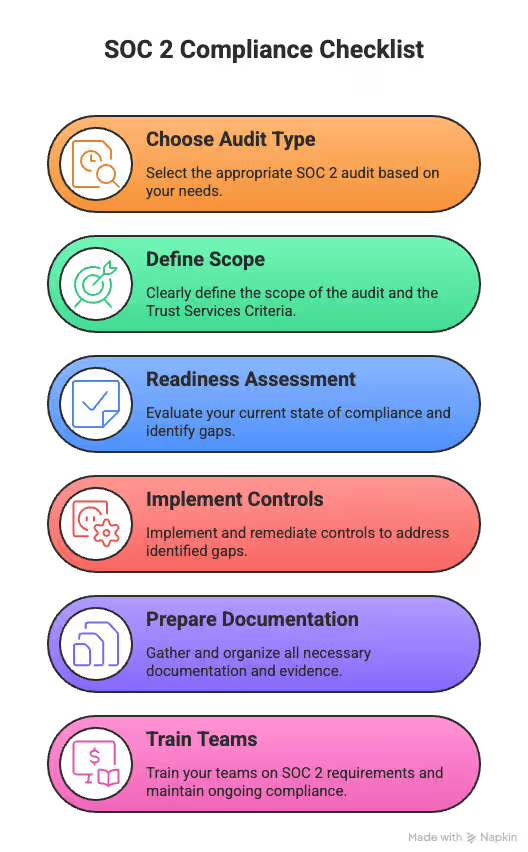
SOC 2 Compliance Checklist
Each step builds on the previous one to create a clear, repeatable audit path.
This decision sets your audit timeline. Choose between SOC 2 Type 1, which reviews control design at a point in time, and SOC 2 Type 2, which evaluates how controls perform over time.
Choosing early prevents delays, misalignment, and unnecessary rework.
Scope determines what auditors will examine and test.
Clear scoping keeps audits focused, efficient, and predictable.
A readiness assessment reveals gaps before auditors do.
This step reduces surprises and lowers audit risk significantly.
Controls turn intent into execution.
Effective controls should be practical, repeatable, and consistently followed.
Documentation is what auditors validate.
Strong documentation reduces audit friction and follow-ups.
People and processes sustain SOC 2 compliance.
Compliance becomes easier when it’s built into daily operations.
A well-structured SOC 2 compliance checklist doesn’t just help you pass your first audit—it builds a repeatable system that keeps your security program strong, credible, and ready for growth.
Achieving SOC 2 compliance goes beyond passing an audit. It’s a tangible way to show your customers, partners, and stakeholders that your organization prioritizes security, operational excellence, and trust. Here are the key benefits of SOC 2 compliance:
SOC 2 compliance signals that your organization takes data security seriously. Clients gain confidence knowing your systems and processes meet rigorous standards, making them more likely to engage and remain loyal.
Prospects often request detailed security questionnaires before doing business. A SOC 2 report streamlines this process, reducing back-and-forth, saving time, and eliminating unnecessary friction in sales cycles.
The policies, controls, and procedures implemented for SOC 2 don’t just satisfy auditors—they actively mitigate risks, improve monitoring, and enhance incident response, safeguarding sensitive information and business operations.
SOC 2 aligns with industry best practices and frameworks, helping organizations meet various regulatory and contractual obligations. This reduces potential legal and financial exposure while reinforcing internal governance.
Security incidents can happen to anyone, but SOC 2 demonstrates that you have the right detection, response, and communication processes in place. This helps minimize reputational damage and maintain customer confidence.
Many enterprise clients and partners require SOC 2 compliance before engaging vendors. Achieving SOC 2 opens doors to new markets, contracts, and high-value partnerships, positioning your organization for scalable growth.
SOC 2 compliance isn’t just a formality—it’s a strategic investment in trust, security, and business credibility.
Preparing for a SOC 2 audit can feel overwhelming, especially for first-time organizations. The key is not just implementing controls but doing so in a structured, repeatable way that demonstrates operational maturity. Following best practices ensures a smoother audit process, reduces surprises, and maximizes the value of your SOC 2 compliance efforts.
Before auditors arrive, evaluate your current systems, processes, and controls. Identify gaps between existing practices and SOC 2 requirements. Document weaknesses and prioritize remediation to ensure your organization addresses the most critical issues first.
Determine which systems, applications, and data fall under the audit. Select the relevant Trust Services Criteria—Security is mandatory, while Availability, Confidentiality, Processing Integrity, and Privacy depend on your services. A clear scope keeps the audit focused, reduces complexity, and prevents unnecessary evidence collection.
Ensure controls cover access management, change management, risk assessment, monitoring, and logging. Assign clear owners for each control so accountability is evident. Practical, repeatable, and consistently followed controls demonstrate operational effectiveness to auditors.
Collect management assertions, system descriptions, control matrices, policies, logs, and reports before the audit. Organized, easily accessible evidence speeds up auditor reviews and minimizes follow-up requests.
Employees should understand their part in maintaining controls. Conduct regular security awareness training, emphasize compliance responsibilities, and simulate audit scenarios to prepare staff for auditor interactions.
SOC 2 compliance is not a one-time effort. Monitor controls, conduct internal audits, and update processes regularly. Continuous oversight ensures your organization remains audit-ready and can quickly respond to changes or incidents.
Following these best practices creates a structured, confident approach to SOC 2 audits, reducing stress and improving the likelihood of a smooth, successful outcome.
Passing your first SOC 2 audit is just the beginning. True compliance is continuous, requiring vigilance, preparation, and proactive practices. This section covers executing your audit effectively and embedding ongoing compliance routines so your organization stays secure, audit-ready, and trustworthy.
Your auditors are partners, not adversaries.
Clear communication makes the audit smoother for everyone.
Even well-prepared teams can stumble. Watch for:
Being aware keeps your team proactive and confident.
Evidence validates your controls.
Well-prepared evidence reduces follow-ups and accelerates audit completion.
SOC 2 compliance requires constant oversight.
Monitoring keeps your organization proactive and audit-ready.
Staying compliant means keeping controls aligned with how your business actually operates.
Consistent checks strengthen security and prepare for future audits.
SOC 2 Type 2 reports typically last 12 months.
Continuous improvement ensures long-term compliance and builds lasting trust.
Merging management and maintenance into a single structured approach helps your organization move confidently from first audit to ongoing compliance, reinforcing security, credibility, and readiness for growth.
SOC 2 compliance isn’t just a checkbox—it’s proof that your organization values security, trust, and operational maturity. Understanding the Trust Services Criteria, preparing a structured compliance checklist, and training your teams all contribute to a smoother, more confident audit experience. With a clear roadmap, even first-time audits become manageable rather than overwhelming.
Passing the audit is just the start. Embedding continuous monitoring, regular access reviews, policy updates, and internal audits ensures that compliance is maintained, not just achieved once. This proactive approach reduces risks, prevents gaps, and strengthens your organization’s long-term reputation.
SOC 2 compliance also opens doors. It signals to customers and partners that you protect data seriously and operate with integrity. Following best practices, managing audits effectively, and maintaining continuous compliance allows your organization to navigate audits confidently while fostering trust and resilience in today’s competitive business landscape.
SOC 2 isn’t a destination—it’s a journey of continuous improvement and credibility.
Build trust and prove your security with UprootSecurity — turning SOC 2 compliance into your strongest sales advantage.
→ Book a demo today

Senior Security Consultant