Ever noticed how logging into your favorite app feels effortless, but accessing your company systems feels like solving a riddle? That’s the gap between great Customer Identity and Access Management (CIAM) and everything else.
CIAM sits right where cybersecurity meets customer experience. It’s the invisible gatekeeper deciding who gets in, how they get in, and what they can do once inside. But unlike traditional IAM systems—built for employees—CIAM is designed for your customers and external users, scaling to millions without compromising on security or speed.
And that distinction matters more than ever. Today, 88% of customers say the experience you deliver matters just as much as your product. Meaning: your login flow now carries as much weight as your actual offering.
Companies that invest in mature CIAM systems see a 40% drop in identity-related security incidents. That’s not just stronger security—it’s smarter business.
Because at the end of the day, CIAM isn’t just about keeping intruders out. It’s about letting the right people in—smoothly, securely, and without friction, turning every login into a trust-building moment.
What Is CIAM and Why It Matters for Enterprise IT?
Customer Identity and Access Management (CIAM) is the system that manages how customers log in, register, and interact with your digital platforms—safely, smoothly, and without friction. Think of it as your digital front door, blending convenience with airtight security to protect both your users and your business.
Unlike traditional IAM systems built to manage internal employee access, CIAM is designed for scale. It can handle millions—even billions—of customer identities while maintaining performance and trust.
For enterprise IT teams, CIAM has moved from a nice-to-have to a must-have. It offers a single, unified view of every customer, stops credential-based attacks before they start, and simplifies compliance with privacy laws like GDPR, CCPA, and PSD2.
The result? Fewer breaches, smoother logins, and happier customers. Companies with mature CIAM programs see up to a 48% jump in customer satisfaction for digital experiences.
In essence, CIAM transforms identity management into a business advantage—fueling trust, loyalty, and growth.
Core CIAM Capabilities for Modern Identity Access Management
You've got the why. Now let's talk about the what.
Modern CIAM isn't just a fancy login system. It's the digital backbone that keeps your customers happy and hackers frustrated.
CIAM Authentication and Authorization Mechanisms
Forget everything you know about passwords. Modern CIAM blends intelligence, security, and simplicity for seamless logins.
- Passwordless Authentication – Biometrics, magic links, and passkeys.
- Adaptive Authentication – Real-time checks by device and behavior.
- Multi-Factor Authentication (MFA) – Layered protection customers expect.
Authorization has evolved too—fine-grained controls and step-up checks act like a smart bouncer who knows exactly who belongs.
User Lifecycle Management and Self-Service
Nobody wants to call support to reset their password. Good news: they don't have to anymore.
Modern CIAM lets customers handle their own stuff:
- Account recovery without human intervention
- Profile updates that sync everywhere
- Preference management that follows them across every touchpoint
The system handles the entire customer journey—from "hello" to "goodbye"—keeping everything consistent.
Single Sign-On (SSO), Federation, and Extensibility
Single Sign-On is like having a backstage pass that works at multiple venues. One login, access to everything you need.
Federation takes this further:
- Cross-domain authentication between different organizations
- SAML and OIDC support for playing nice with others
- B2B scenarios where partners keep their own identity systems
Your customers don't care about your technical architecture. They just want stuff to work.
Consent and Preference Management
Here's something most companies get wrong: consent management.
Effective CIAM solutions track:
- Version-controlled consent records (audit-ready)
- User-friendly privacy controls
- Centralized consent that works globally
This isn't just about checking boxes for GDPR and CCPA. It's about building trust through transparency. When customers know exactly what you're doing with their data, they're more likely to stick around.
CIAM Data Handling and Secure Storage
The foundation of everything: how you handle customer data.
Modern CIAM platforms lock this down tight:
- Encryption everywhere (in transit, at rest)
- Centralized, secure repositories
- Audit trails for everything
The smartest platforms use progressive profiling. They start with the basics and gradually build customer profiles through continued interactions. No overwhelming forms. No data collection fatigue.
Just clean, secure, customer-friendly identity management.
How CIAM Cybersecurity Strengthens Enterprise Security
Enterprise security is under constant attack, and traditional username-password logins just don’t cut it anymore. CIAM cybersecurity doesn’t just build walls—it creates smart, adaptive defenses that stop attacks while keeping logins seamless.
Multi-Factor and Adaptive Authentication
Modern CIAM platforms strengthen every login with layered security:
-
Multi-Factor Authentication (MFA) – Adds an extra verification step, drastically reducing unauthorized access. One additional step, massive protection.
-
Adaptive Authentication – Monitors device, IP, location, and behavior. If something seems off, extra proof is required. Legitimate users glide through; threats hit a wall.
-
Biometric Authentication – Fingerprints, face, and voice recognition. Passwords can be stolen; biometrics cannot.
These methods show convenience and security can coexist.
Protection Against Credential Stuffing and Brute Force Attacks
Credential attacks are rampant, affecting 80% of organizations. CIAM defends automatically:
- Bot Detection – Blocks fake login attempts before reaching your systems.
- Rate Limiting – Restricts repeated login attempts to neutralize brute-force attacks.
- Breached Password Detection – Checks credentials against breach databases in real time and forces resets if compromised.
Attackers are stopped, and users stay safe, keeping enterprise systems resilient.
Encryption, Tokenization, and Data Protection
CIAM protects not just logins, but everything behind them:
- Encryption – Shields data with AES-256 and TLS/SSL so stolen information stays unreadable.
- Tokenization – Replaces real data with valueless tokens—breaches yield nothing useful.
- Data Masking – Shows sanitized data to unauthorized users while keeping systems functional.
Together, these create airtight data defenses.
Audit Trails, Monitoring, and Compliance Reporting
Visibility is power. CIAM keeps every move traceable and compliant:
- Audit Logs – Capture every authentication event for forensics.
- Anomaly Detection – Uses ML to spot suspicious behavior early.
- Compliance Reports – Automate documentation for GDPR, SOC 2, and ISO audits.
Unified, these layers form an adaptive security fabric—keeping users connected, attackers blocked, and enterprises resilient.
Implementing CIAM IT in Enterprise Environments
Talk is cheap. Implementation is where CIAM projects either soar or crash. Buy-in, a business case, and a roadmap are one thing. Making CIAM work inside your existing IT environment without breaking systems is the real test.
CIAM Management via APIs, SDKs, and Automation
Integration is the key. Leading platforms offer robust APIs and SDKs for real-time data sync with CRMs, CMSs, and e-commerce tools. Developer experience matters—clear documentation, prebuilt components, and SDKs for major languages help teams deploy faster, reduce complexity, and avoid costly mistakes.
When your ecosystem communicates seamlessly through APIs and automation, CIAM becomes more than a tool—it’s a backbone. Faster rollouts, fewer bottlenecks, and consistent identity experiences across platforms follow.
Integration with Load Balancers and Hybrid Systems
Complex infrastructures need CIAM that keeps up. Load balancer integration (e.g., AWS ALB with Cognito) automates authentication at scale, reducing latency, manual overhead, and potential points of failure.
Hybrid and multi-cloud deployments require fault tolerance. Split-cluster setups balance loads, manage capacity, and deliver consistent authentication across web, mobile, and IoT channels. Your users experience smooth logins everywhere, even during traffic spikes.
Migration from Legacy IAM to Modern CIAM
Replacing legacy IAM overnight invites chaos. Start with a gap analysis, define objectives, and migrate low-risk segments first. Map authentication flows, preserve user data, and maintain trust.
Slow, deliberate moves minimize downtime, customer friction, and potential security gaps. The goal: migrate quietly, without disruption, while maintaining full operational continuity.
Continuous Monitoring and Performance Optimization
CIAM isn’t set-and-forget. Dashboards and SLAs should inform, not overwhelm. Regular load testing ensures stability under stress.
Cloud-native designs with Docker and Kubernetes provide elasticity. Auto-scaling based on CPU, traffic, or latency keeps logins smooth, reliable, and uninterrupted.
When implemented correctly, CIAM becomes the invisible engine powering secure, seamless customer experiences. Get it wrong, and you spend months untangling what should have worked from day one.
Enhancing Customer Experience Through CIAM
Here's the truth nobody wants to admit: your customers judge you in the first 10 seconds.
91% of adults ages 18 to 49 have purchased products online using smartphones.Your login is your storefront, registration your first impression, and authentication your handshake. CIAM turns these critical moments into seamless, competitive advantages.
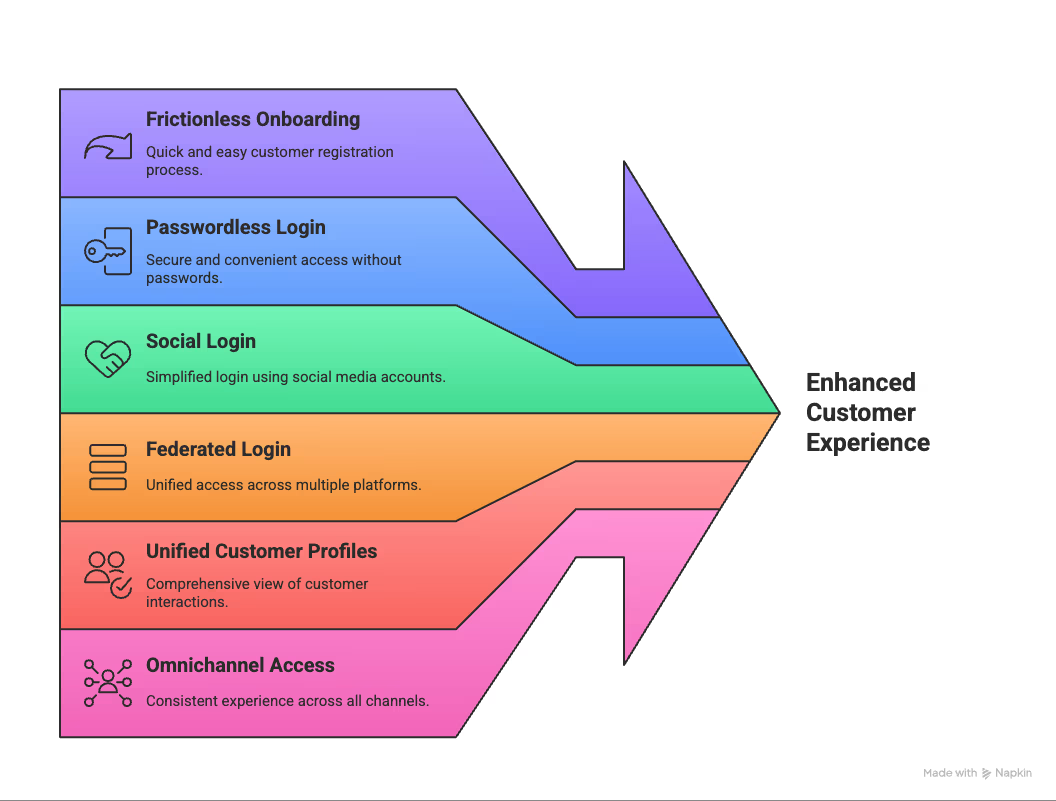
How CIAM Improves Customer Experience
Frictionless Onboarding and Passwordless Login for Seamless First Impressions
You get one shot at onboarding—mess it up, and 74% of potential customers leave for a competitor. Smart CIAM ensures the first interaction is smooth:
- Account creation feels effortless across devices
- Passwordless options remove friction, including magic links, biometrics, and one-time codes
- No more confusing password rules that frustrate users
CIAM turns onboarding into a competitive advantage, making registration simple and fast without sacrificing security.
Social and Federated Login for Higher Engagement and Reduced Drop-Off
Forgotten passwords cause abandoned carts and lost revenue. CIAM solves this:
- Form abandonment drops up to 80%
- One-click login via Google, Facebook, or Apple accounts
- Eliminates the need for users to remember new passwords
For B2B environments, federated identity allows partner organizations to maintain their own systems while accessing your platform securely. Everyone wins with less friction and faster access.
Unified Customer Profiles for Personalized Experiences
CIAM centralizes fragmented data into one complete view:
- Every customer touchpoint contributes context
- Progressive profiling avoids overwhelming forms
- Authentication systems integrate with marketing platforms
Organizations using unified profiles see 47% higher retention and 29% higher average order values, turning identity management into a growth engine.
Omnichannel Access Across Devices and Platforms for Consistency
Customers switch devices constantly. CIAM ensures identity follows them seamlessly:
- Start on mobile, continue on desktop, finish in-store
- Preferences and authentication stay consistent
- No re-entering information, no friction
Smooth, unified access builds trust and keeps customers engaged and loyal.
CIAM B2B and Multi-Tenant Enterprise Environments
B2B identity management operates on a different scale. Instead of individual users, you’re managing entire organizations—each with unique hierarchies, access policies, and admin structures. One client might bring 50,000 users, all with different roles and privileges. Traditional CIAM platforms often crumble under that complexity. Modern CIAM systems don’t—they’re built for it.
Fine-Grained Access Control and Role Management
When it comes to B2B identity, basic role management won’t cut it.
-
Attribute-Based Access Control (ABAC) – Goes beyond simple roles by evaluating user attributes such as department, project, and clearance before granting access. It enables precise, contextual decisions at scale.
-
Granular Role Assignment – Treats each organization as a secure entity with its own permissions, roles, and boundaries—ensuring isolation and flexibility.
-
Delegated Administration – Allows partner organizations to manage their own user base without waiting on your IT team.
These controls prevent “role explosion,” where hundreds of overlapping roles create confusion and compliance risk.
Federation with SAML and OIDC for Partner Portals
Federation lets organizations collaborate securely—without sharing passwords.
-
SAML 2.0 – Enables identity trust across systems, so partners can authenticate seamlessly using their existing credentials.
-
OIDC (OpenID Connect) – Adds modern authentication for web and mobile integrations.
-
Cross-Tenant Synchronization – Ensures consistent access for organizations using multiple Entra ID tenants.
-
Just-in-Time (JIT) Provisioning – Automatically creates user accounts at first login, applying correct roles instantly.
Leveraging CIAM AWS and CIAM Azure in Multi-Tenant Architectures
Cloud CIAM takes scalability to the next level.
-
AWS Cognito – Offers three isolation models: Silo (separate resources per tenant), Bridge (shared infrastructure with schema-based separation), and Pool (row-level security).
-
Microsoft Entra ID – Adds centralized SSO, adaptive authentication, and hybrid cloud integration.
Together, they deliver fast, secure, and consistent onboarding—reducing setup time from weeks to minutes while maintaining airtight identity boundaries.
Comparing Leading CIAM Platforms: Auth0, AWS, and Azure
The CIAM market has plenty of options, but Auth0 CIAM, AWS Cognito, and Microsoft Entra stand out. Each platform solves the same problem—managing and securing digital identities—but they do it differently. This table breaks down where each shines, how customizable it is, how it scales, and the security features that matter most.
| Aspect | Auth0 | AWS Cognito | Microsoft Entra (Azure) |
|---|---|---|---|
| Best For | Developer-first teams | Businesses in the AWS ecosystem | Enterprises using Azure & Microsoft 365 |
| Core Strength | Flexible, extensible, developer-friendly | Deep AWS integration, scalable | Enterprise-grade, compliance-ready |
| Customization | Flexible authentication pipelines using custom JavaScript | Limited UI customization, strong backend integration | Customizable sign-up flows with policy-driven controls |
| Security | Built-in protection against bots and credential attacks | WAF integration, adaptive authentication | MFA, conditional access, Verified ID |
| Scalability | Great for startups to mid-size enterprises | Scales effortlessly across millions of users | Designed for large enterprises with existing Azure footprint |
| Ideal Use Case | Teams wanting custom, code-driven identity management | Companies already using AWS who need seamless scale | Organizations prioritizing governance, compliance, and hybrid IT |
No one-size-fits-all. Auth0 is flexible, Cognito scales with AWS, and Entra excels at governance and compliance. Choose the CIAM platform that fits your architecture, user base, and growth plans—so identity management stays seamless, secure, and future-ready.
Certified Identity and Access Manager (CIAM) Certification Insights
The Certified Identity and Access Manager (CIAM®) from IMI is a vendor-neutral credential designed for identity professionals. To earn it, you need IMI membership, pass a 100-question exam with at least 70%, and gain 40 points through professional experience, education, or other certifications.
This certification is ideal for anyone managing multiple CIAM systems, aiming to specialize in identity governance, or looking to boost career credibility. It provides practical knowledge that applies across platforms and enterprise environments.
Choosing the right CIAM platform isn’t about features alone—it’s about ensuring it fits your users, architecture, and workflows seamlessly.
CIAM: Your Edge in the New Security Race
CIAM isn’t another item on your IT checklist—it’s the line between brands that scale and those that fade. Customers won’t wait while you fix login friction or patch weak security. They want seamless access and rock-solid protection, right now.
The companies winning with CIAM aren’t guessing. They’re cutting registration drop-offs to near zero, turning personalization into measurable engagement, and letting compliance run quietly in the background. Security incidents? Rare, not routine.
Passwordless login. Adaptive authentication. Real-time risk analysis. These aren’t futuristic anymore—they’re the new baseline. Platforms like Auth0, AWS Cognito, and Microsoft Entra deliver that edge at enterprise scale. The best platform depends on your stack, but waiting too long costs far more than any license fee.
Because CIAM isn’t just identity management—it’s trust management. It’s retention. It’s growth. And every week you delay, competitors widen the gap.
CIAM isn’t a side project anymore. It’s the backbone of your digital survival.
Your move.
Secure customer identities, streamline compliance, and reduce risk with UprootSecurity — where GRC meets real-world protection.
→ Book a demo today
Frequently Asked Questions

Robin Joseph
Senior Security Consultant
