0%
Every year, cyberattacks get smarter — and companies fall even further behind. Data breaches are now draining companies a staggering $4.45 million on average. And the worst part? Most organisations are wide open to attack, completely unaware of the threats lurking inside their own systems.
We've been fighting this battle for years, and here’s the ugly truth—companies take an average of 277 days to even realise they’ve been breached. That’s nine months of hackers roaming free before anyone notices. Why do so many breaches make headlines? Because most companies run weak, half-baked security tests that miss real threats. It’s security theatre—flashy, shallow, and dangerously ineffective.
There’s blind testing, targeted testing, internal and external approaches—but without a clear strategy, it’s just noise. AI and automation can now spot vulnerabilities faster than ever, yet most organisations are still unprepared for modern threats—especially those aimed at cloud environments and Large Language Models. So which penetration testing framework will actually protect your systems in 2025? Not the flashiest. Not the most expensive. The one that actually works.
In the ever-evolving landscape of cybersecurity, penetration testing is a crucial component in identifying vulnerabilities and boosting security. As new threats emerge, penetration testing methodologies evolve to keep up with them. Below are the top 5 methodologies that businesses and security professionals should follow in 2025 to ensure comprehensive and effective security assessments:
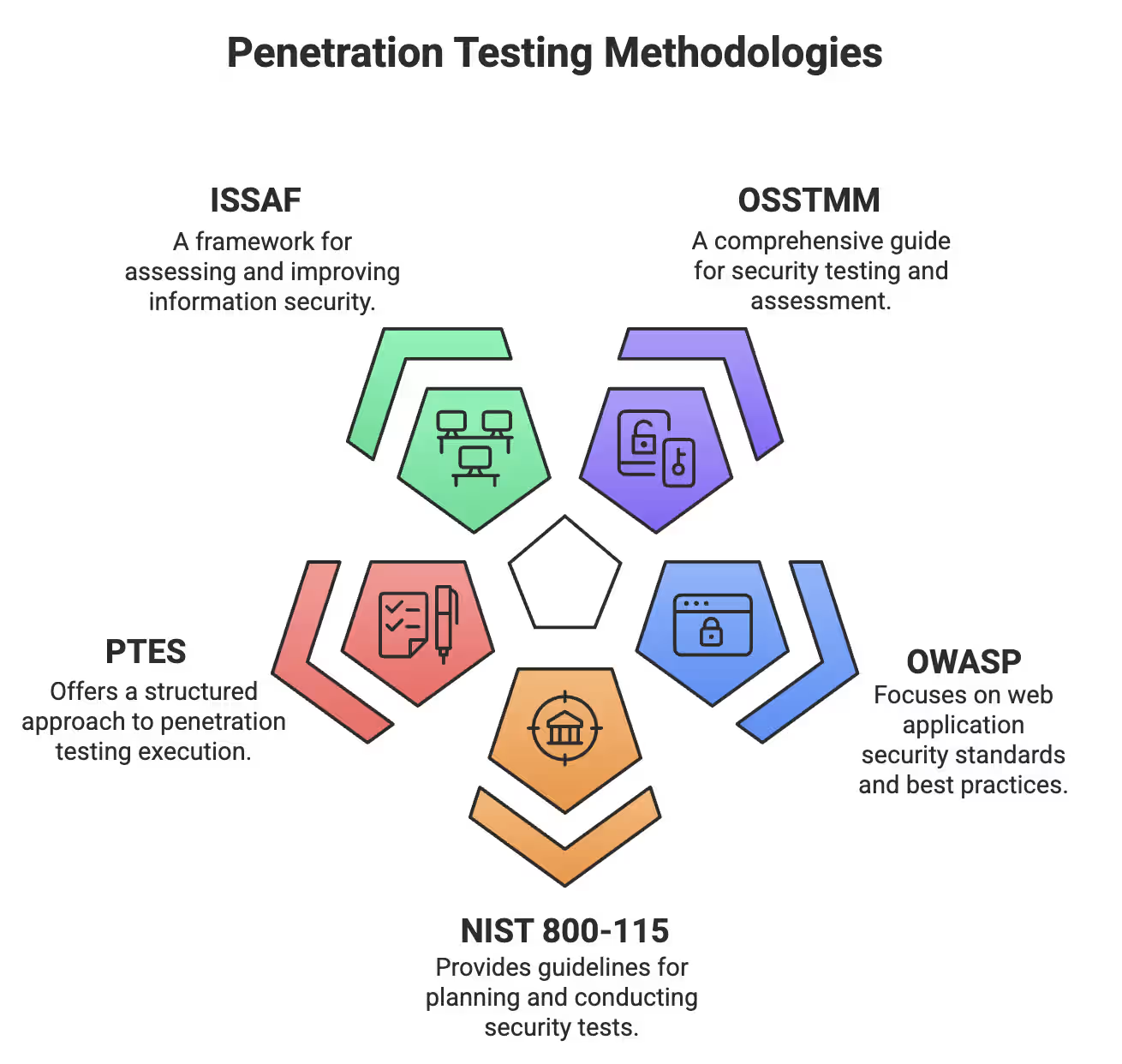
Penetration Testing Methodologies
Let's break down each of them.
OSSTMM (Open Source Security Testing Methodology Manual) offers a detailed approach to penetration testing through a well-structured scientific method. It delivers thorough security evaluations. Instead of depending on checklists like other methods, OSSTMM focuses on examining five key aspects: information security, process security, internet technology security, communications security, and physical security.
OSSTMM still plays a big role in 2025 because it uses practical methods. It mimics how hackers operate and addresses every layer of security, including physical and digital safety as well as daily operations. It works well with rules like ISO27001 and COBIT. Being open-source lets it keep up with new risks through updates. The system also uses clear metrics, like RAVs and SAFE, which help to measure and improve security levels .
Organisations seeking a complete, real-world security assessment should use OSSTMM. It’s ideal for those needing to meet regulatory standards, strengthen security measures, or show measurable security progress to their stakeholders. Its comprehensive approach is suited for businesses with complex security needs.
The Open Web Application Security Project (OWASP) offers a useful framework to secure web applications. The Web Security Testing Guide, now in version 4.2, divides security testing into 12 categories. It provides clear instructions, tools, and solutions to address vulnerabilities. OWASP also creates standards like the OWASP API Security Project and the Mobile Application Security Verification Standard (MASVS) to secure APIs and mobile applications.
OWASP stays essential in 2025 since web apps, mobile platforms, and APIs still drive how businesses work. Research highlights serious problems like broken access control, insecure designs, and cryptographic issues. OWASP adjusts to new threats, including risks tied to Large Language Models, by staying flexible and adaptive to tech changes. This keeps OWASP valuable in tackling current security issues.
Companies working on web apps, APIs, or mobile apps rely on OWASP to find and fix security issues. Security professionals gain from its clear and structured methods. This becomes crucial for companies handling sensitive data and those aiming for strong, verifiable cybersecurity practices.
NIST 800-115 serves as a structured, disciplined approach to penetration testing. Instead of random testing, it breaks testing into four distinct parts—Planning, Discovery, Attack, and Reporting. This framework makes sure the testing is legal, thorough, risk-focused, and leads to real improvements, not just surface-level fixes.
NIST 800-115 remains vital in 2025 since cybersecurity rules grow stricter, affecting federal contractors and regulated industries. Its emphasis on simulating real-world attacks, creating useful reports, and integration with standards such as NIST SP 800-53 and 800-171 helps it remain crucial in government and private sectors.
Federal agencies, government contractors, and businesses handling Controlled Unclassified Information (CUI) rely on NIST’s structured approach to penetration testing. It also proves valuable to organisations in healthcare, finance, and critical infrastructure, as well as big companies with complex networks.
PTES (Penetration Testing Execution Standard) lays out a step-by-step plan to perform penetration tests. It includes everything from pre-engagement interactions to post-exploitation and reporting. PTES emphasizes real-world, targeted attacks, threat modeling, and ethical practices, making security tests organized and effective.
PTES remains a top choice because it blends deep technical exploitation with business risk awareness. It tackles advanced issues like memory-resident attacks and stealth techniques while also helping industries follow regulations and handle increasing cyber security threats.
Organizations in financial services, healthcare, government contracting, critical infrastructure, and any company aiming to gain ethical and practical penetration testing can use PTES. Its adaptable yet systematic method helps businesses seeking real security instead of just meeting compliance standards.
The Information Systems Security Assessment Framework, known as ISSAF, was developed by OISSG as an extensive guide. It does more than identify technical flaws. It looks at human behaviour, physical defences, and business operations. With over 1,200 pages, the framework divides security testing into three main stages: Planning, Assessment, and Reporting. It gives precise guidelines to help security experts perform both offensive and defensive tests using specialised tools.
ISSAF remains crucial in 2025 because it does more than just basic compliance checks. It focuses on practical testing that imitates real-world scenarios. Its flexible structure tackles challenges in modern hybrid setups like AI systems, cloud , and IoT environments. With its attacker-aware and defender-friendly approach, industries can better prepare for advanced cyber threats.
Financial institutions, healthcare providers, and any highly regulated or security-critical organisation rely on ISSAF to perform thorough, practical, and customisable penetration testing. This helps them meet frameworks like ISO27001, HIPAA, and NERC CIP while staying a step ahead of real-life attackers.
Here's the naked truth about security testing – if you're just randomly poking at your systems hoping to find holes, you're doing it wrong. Dead wrong.
Want real security? You need a step-by-step approach that doesn't skip a single stage. Because hackers don't skip steps. They follow a precise playbook.
These are the 5 stages of pentesting (skip one at your peril):
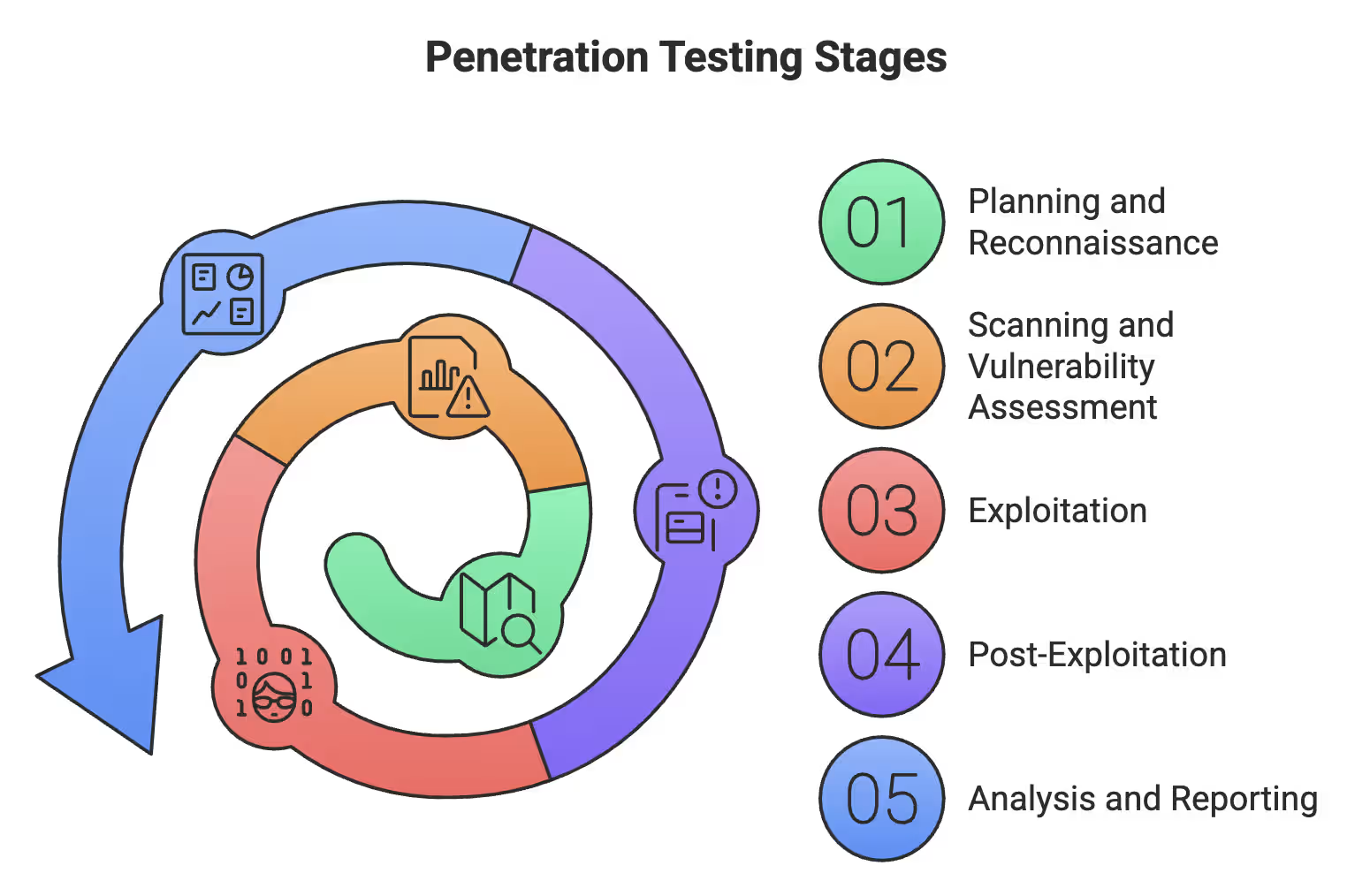
Penetration Testing Stages
Some fancy frameworks split these into seven steps, but they're all variations of this same process. Don't be fooled by complexity that adds no value. With half of all attacks now affecting multiple systems, rushing security work is asking for trouble. If your security team cuts corners, they don’t become more efficient. They simply make it easier for attackers to walk right in.
Let me tell you a brutal story. A regional bank decided post-exploitation testing was "optional" during their annual security check. Guess what happened?
Attackers found what the testers missed. They established persistent access through a VMware vulnerability and kept the bank offline for TWO WEEKS. The damage? Over $4 million in losses.
One skipped step. Four million dollars gone. That's the price of incomplete testing.
Let's face it – most folks trying to pick a penetration testing methodology are completely confused by the options. They hide all the critical differences in microscopic font at the back of white papers.
But we've got #nothingtohide. So here's the naked truth about each methodology:
| Methodology | What It Really Does | The Actual Steps | Who Should Actually Use It | Why It's Special | Does Anyone Update It? |
|---|---|---|---|---|---|
| OSSTMM | Scientific security testing across multiple channels | Information, Process, Internet, Communications, and Physical security | Organizations needing comprehensive security evaluation | RAVs and SAFE metrics for quantifiable results | Updated every 6 months |
| OWASP | Web application security | 12 testing categories including Authentication, Authorization, Input Validation | Web applications and API security | Includes specialized Top 10 lists for web apps and LLMs | Regular community updates |
Security methodologies aren't always pretty. But they actually work! That's the proof that we didn't tamper with reality.
Remember, fancy marketing language won't protect your systems. Only honest, thorough testing will.
Here’s the real takeaway: no single penetration testing methodology covers everything. The smartest security teams in 2025 start with a core approach that fits their systems — whether that's NIST, PTES, OSSTMM, ISSAF, or OWASP — and then mix in elements from others to cover the gaps. Structured testing isn’t just about checking boxes; it focuses on staying ready for actual real-world threats.
The rise of AI-driven attacks, cloud vulnerabilities, and supply chain threats makes old testing methods ineffective. Organisations that adopt a disciplined, layered approach are able to identify weak spots more quickly, experience fewer breaches, and prevent the loss of millions in damages. In a world where cyberattacks are inevitable, your choice of methodology might be the only thing standing between resilience and disaster.
Bottom line: modern security needs total dedication—no shortcuts, no guesswork, and definitely no pretending.

Senior Security Consultant
| NIST 800-115 | Government-grade security assessment | Planning, Discovery, Attack, Reporting | Federal agencies, contractors, regulated industries | Compliance-focused approach | Government-mandated updates |
| PTES | End-to-end penetration testing | 7 phases from pre-engagement to reporting | Organizations seeking consistent, repeatable testing | Detailed exploitation and post-exploitation guidance | Not mentioned |
| ISSAF | Holistic security assessment | Planning, Assessment, Reporting/Clean-up | Finance and healthcare sectors | 1,200+ pages of detailed guidance, balanced offensive/defensive approach | Not mentioned |
| Stages of Pen Testing | Sequential testing process | Planning, Scanning, Exploitation, Post-Exploitation, Reporting | All organizations | Focuses on practical attack simulation | Evolves with threat landscape |