0%
Ever wondered why hackers always seem to be one step ahead?
Here’s the truth. While you’re focused on running your business, cybercriminals are busy running attacks. They’re probing your networks, testing your firewalls, and searching for that one overlooked flaw to exploit. To them, every login page, forgotten database, or outdated plugin is an open invitation.
But what if you could think like a hacker before the hackers do?
That’s exactly what Vulnerability Assessment and Penetration Testing (VAPT) is built for. In today’s threat landscape, VAPT cybersecurity has become a foundational layer of defense for organizations that want to stay ahead of real-world attacks. It’s like having an ethical hacker on your payroll—someone who finds your weak spots before cybercriminals do. VAPT exposes vulnerabilities across your systems, simulates real-world attacks, and shows you what could happen if those flaws were left unpatched.
Because here’s the harsh reality: ignoring your security gaps is like leaving your front door wide open and hoping no one notices. Regular VAPT turns that around. It transforms your security from reactive to proactive—helping you fix problems before attackers even know they exist.
If you’re wondering what is VAPT, it’s the combined process of identifying security flaws and actively testing how attackers could exploit them. VAPT isn’t a single tool or test—it’s a powerful combination of two distinct but complementary security approaches that work best together. And this is exactly where most organizations get confused. The VAPT meaning is simple: find weaknesses early and validate how damaging they could be before real attackers get the chance.
A Vulnerability Assessment acts like a high-powered security scanner. Automated tools comb through your systems, applications, networks, and cloud setups to identify known weaknesses. It’s broad, fast, and detailed—giving you a comprehensive list of what’s wrong. But it stops short of showing you how dangerous those flaws really are.
That’s where Penetration Testing comes in. Instead of relying solely on automation, ethical hackers manually test your systems, simulating real-world attack scenarios. They exploit vulnerabilities, escalate access, and demonstrate the potential damage an attacker could cause if those issues went unpatched.
In essence, vulnerability assessments reveal what is broken, while penetration testing proves how bad it can get. In practical terms, VAPT means actively thinking and testing like an attacker so you can fix issues before they are ever exploited. When combined, VAPT offers both visibility and validation—giving you the clearest, most actionable picture of your organization’s true security posture.
Look, choosing the wrong security tools is like bringing a butter knife to a gunfight.
The right vulnerability assessment and penetration testing tools can spot threats before they become headlines. The wrong ones? They'll give you a false sense of security while hackers walk right through your defenses.
Here is the list of VAPT tools security pros actually use when they need results:
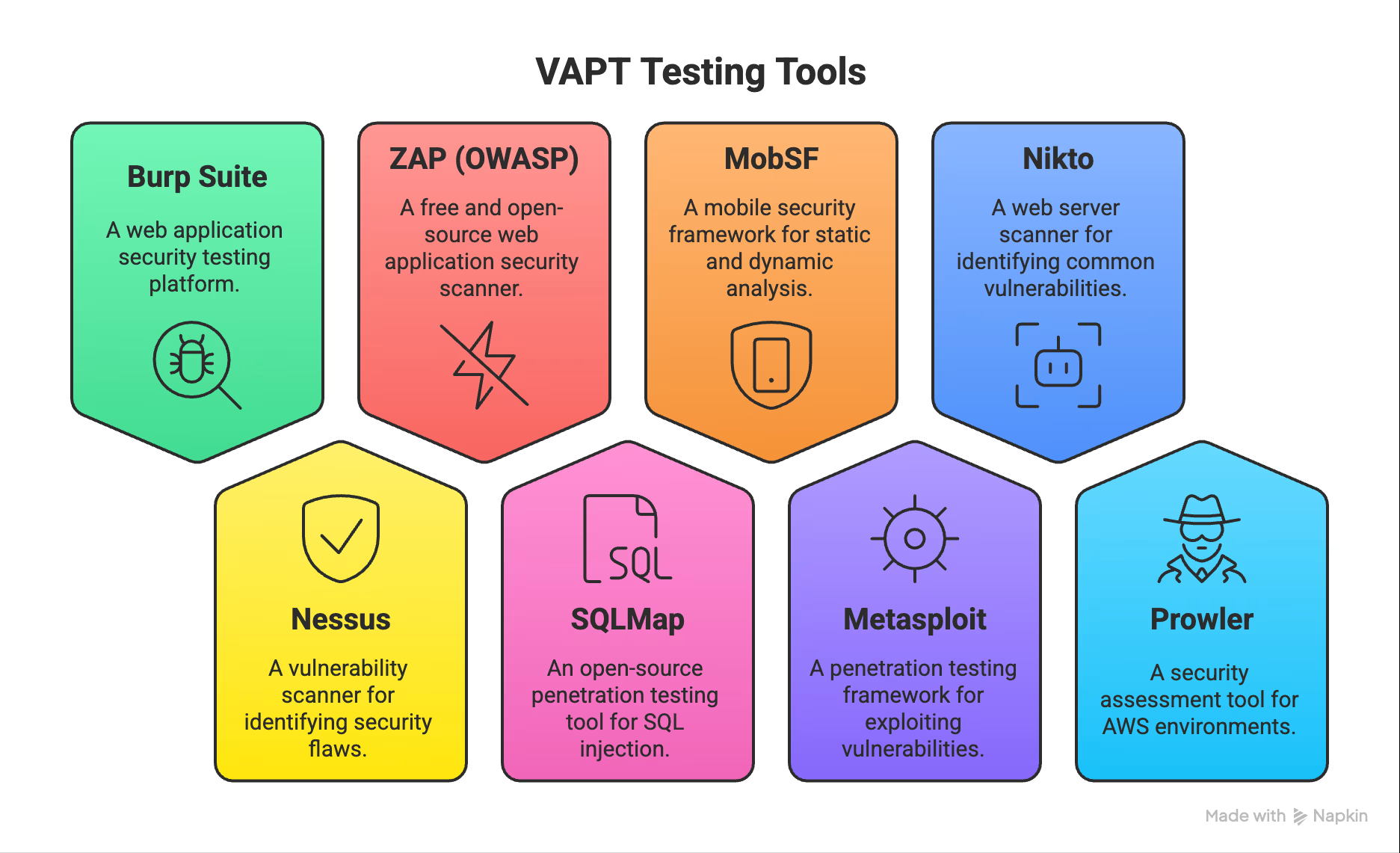
VAPT Testing Tools
Let’s get into each of these and see why they matter.
This one's the undisputed champion for web app security testing. If you're doing penetration vulnerability testing on web applications and you're not using Burp Suite, you're doing it wrong.
Why It Matters:
Nessus has been the gold standard for vulnerability testing service for years, and there's a reason why. This thing scans over 77,000 Common Vulnerabilities and Exposures (CVEs) as of January 2025.
Why It Matters:
Not everyone has the budget for expensive tools. That's where ZAP comes in. This free, community-driven scanner for vulnerability assessment penetration testing has become one of the most popular web application scanners worldwide.
Why It Matters:
SQL injection attacks are still wreaking havoc in 2025. SQLMap automates the tedious process of finding and exploiting these flaws - a must-have for thorough vulnerability and penetration testing.
Why It Matters:
Mobile apps are everywhere, and most of them have serious security issues. For vulnerability assessment and penetration testing service on mobile applications, MobSF handles both Android and iOS security analysis.
Why It Matters:
Want to know if your vulnerabilities are actually exploitable? Metasploit is your answer. This framework is essential for pentest vulnerability assessment because it has a massive exploit database.
Why It Matters:
Nikto might look old school, but don't let that fool you. With about 6,700 known vulnerabilities in its database, this command-line scanner is incredibly valuable for vulnerability testing and penetration testing web servers.
Why It Matters:
Cloud security is a whole different beast. Prowler has become the go-to tool for vulnerability assessment and penetration testing vapt in AWS environments.
Why It Matters:
Bottom line: Your security is only as good as the tools you use. Choose wisely.
Look, picking the wrong vulnerability assessment and penetration testing service is like hiring a security guard who sleeps on the job. You think you're protected, but you're actually just paying for false confidence.
The right choice isn't about fancy marketing claims or the cheapest price. It's about finding a provider who can actually deliver what your specific environment needs.
First things first - know what you're protecting.
Web applications need specialized scanners like Burp Suite. Networks require comprehensive tools such as Nessus. Mobile applications demand dedicated platforms like MobSF. Pretty straightforward, right?
Here's what most vendors won't tell you: they love selling you everything even when you only need specific testing. A good service provider should be brutally honest about what you actually need instead of pushing their entire toolkit on you.
The automation vs. manual testing debate is where vendors love to confuse you with technical jargon.
Here's the truth:
Anyone telling you that one approach is always better than the other is selling you something.
Modern vulnerability testing services should plug into your existing development workflows without causing headaches. Security experts know that embedding VAPT tools into CI/CD pipelines automates vulnerability detection, cuts down on manual work, and gives you real-time security insights throughout development.
If a provider can't integrate with your current setup, they're asking you to change your entire workflow for their convenience. That's a red flag.
This is where the rubber meets the road. 72% of security professionals say false positives kill their team's productivity. Think about it - if your security tool is crying wolf every other day, your team stops paying attention to real threats.
Ask any potential provider for their false positive rates. If they dodge the question or give you vague answers, walk away.
Compliance isn't optional. PCI DSS requires manual penetration testing. ISO 27001 mandates regular VAPT as part of information security controls.
The best providers understand your industry's specific requirements and deliver documentation that actually helps during audits. They don't just run tests - they give you the paperwork that keeps regulators happy.
Choose providers who know your compliance landscape inside and out. Because failing an audit because your security provider didn't understand the requirements? That's on you.
Let’s be honest — vulnerability assessment and penetration testing sound great in theory, but where do you actually start? Most security guides skip the messy reality of getting this stuff to work in your organization.
Here’s your step-by-step guide to implementing a VAPT program that actually works:
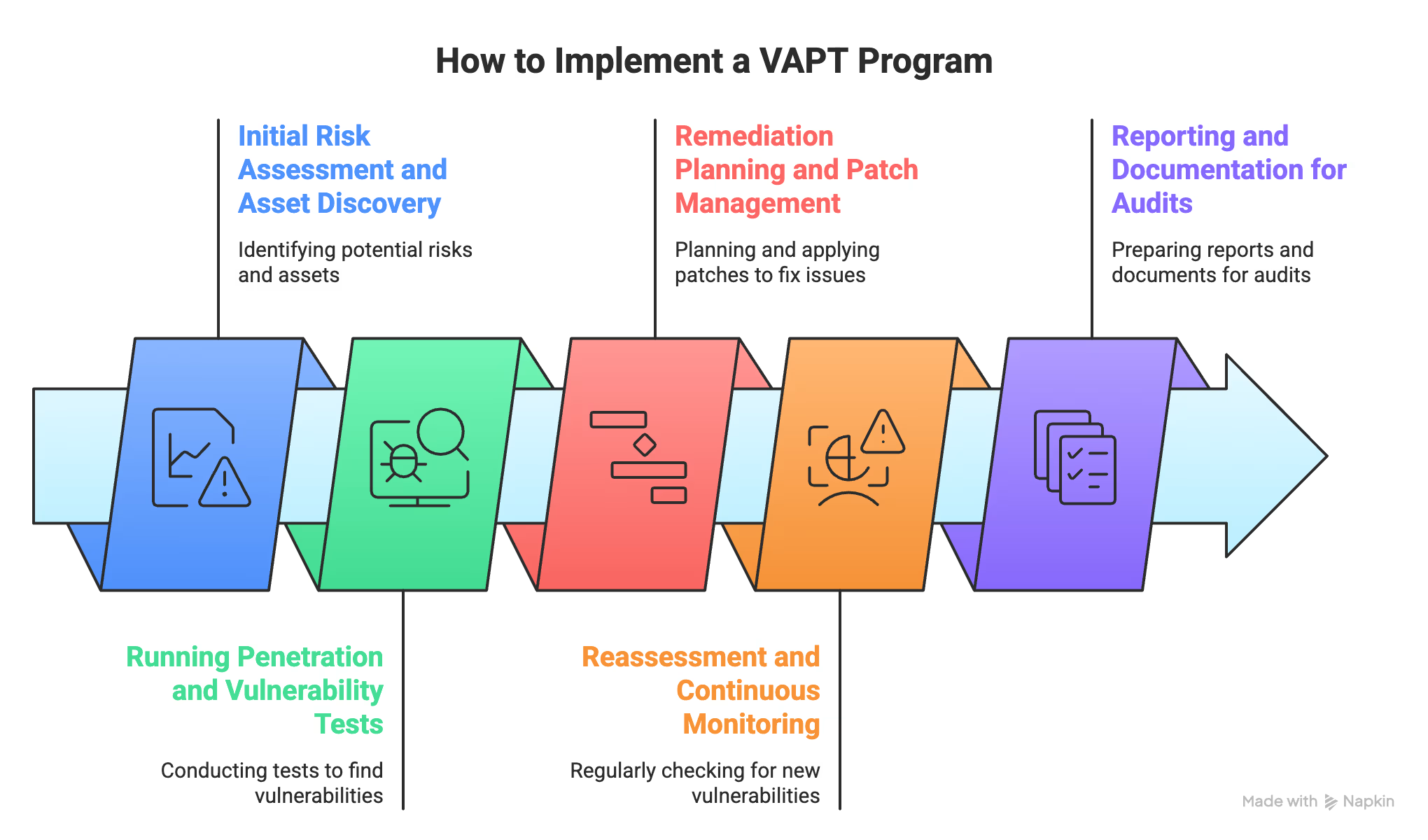
How to Implement a VAPT Program
Let’s break down each step and see how to actually make it work.
You can't protect what you don't know exists. And here's the kicker - 43% of security breaches happen because of assets nobody even knew they had. Ouch.
Your first job isn't fancy scanning. It's making a list:
Here's something most people don't tell you: "Credentialed scans provide more detailed results that can help to detect outdated software, vulnerabilities, and compliance issues," according to security experts. Translation? Authenticated scans find up to 10 times more problems than unauthenticated ones.
Worth the extra setup hassle? Absolutely.
Once you know what you're working with, choose your testing approach:
For web apps and APIs, white-box testing usually gives you the most bang for your buck. Pro tip: scan at least twice weekly with all plugins enabled if you want complete vulnerability data.
Less frequent scanning means you're missing stuff.
Getting a report full of vulnerabilities is overwhelming. Here's how to tackle remediation without losing your mind:
Priority matters. High vulnerabilities need fixing within 30 days, critical ones within 15 days. No exceptions.
Your remediation checklist:
One-and-done penetration test vulnerability assessment doesn't work in 2025. Threats evolve daily, and continuous monitoring catches new problems before they become disasters.
Set up regular testing based on:
Nobody wants another 200-page technical document gathering dust. Your VAPT report needs to work for everyone:
Remember - VAPT reports aren't just checklists. They're your roadmap for fixing vulnerable areas before attackers find them. Make them count.
Cyber threats aren’t slowing down—they’re getting sharper, faster, and far more unpredictable. You can either get ahead of the problem or wait for it to find you. We know which side you’d rather be on.
The numbers say it all: 85% of organizations have increased their penetration testing budgets. Around 43% of breaches come from assets no one even knew existed. Authenticated scans detect up to 10 times more vulnerabilities than unauthenticated ones, and critical issues need fixing within 15 days—not 15 weeks.
Tools like Burp Suite, Nessus, and MobSF matter, but they’re only part of the equation. VAPT isn’t a one-time checkbox—it’s a continuous process of identifying, testing, and strengthening your defenses as new threats emerge.
Yes, building a mature VAPT program takes time, skill, and investment. But when the average data breach costs $4.45 million, prevention isn’t expensive—it’s essential.
At the end of the day, finding your own weaknesses before attackers do isn’t just smart cybersecurity. It’s survival. The clock’s ticking—so which side will you choose?

Senior Security Consultant