0%
Getting ISO 27001 certified? Then you've probably heard the terms VAPT and penetration testing thrown around like buzzwords. But here’s the thing—these aren’t just checkboxes for your compliance spreadsheet. They're crucial tools for proving that your security controls actually work in the real world.
ISO 27001 lays out a strong framework for managing information security through an ISMS (Information Security Management System). But frameworks alone don’t catch flaws—testing does. That’s where VAPT (Vulnerability Assessment and Penetration Testing) comes in. These tests simulate real-world attacks to find the gaps in your systems before malicious hackers do.
They also play a vital role in meeting control objectives under Annex A of ISO 27001.
Whether you’re preparing for certification or tightening up your ongoing compliance efforts, VAPT helps you validate risk treatment decisions, strengthen technical controls, and satisfy auditors with confidence.
In this guide, we’ll break down how VAPT fits into ISO 27001, the difference between VA and PT, when and how often to test, and what a good testing report should actually include. Let’s dive in—minus the jargon.
Technically? No. But if you're aiming for actual security—not just a framed certificate—then penetration testing isn’t just useful, it’s essential.
ISO 27001 won’t outright demand a pen test. What it does demand is smart, ongoing risk management. You’re expected to identify threats, evaluate their impact, implement controls, and—critically—verify that those controls work in the real world. That’s exactly where penetration testing shines.
Routine assessments like VAPT (Vulnerability Assessment and Penetration Testing) help you catch the cracks before attackers find them. They simulate real-world breaches, stress-test your defences, and expose whether your risk mitigation plan is more than just paperwork. Skip this step, and you’re operating on faith, not facts.
While the standard leaves room for interpretation, Annex A controls like A.12.6.1 (technical vulnerability management) and A.18.2.3 (technical compliance review) set the expectation: validate what you deploy.
So no, penetration testing isn’t a checkbox in ISO 27001. But it’s one of the clearest, most actionable ways to prove your ISMS isn’t just compliant—it’s battle-ready. And that’s what really matters.
ISO 27001 isn’t just another compliance badge—it’s your blueprint for building trust and proving you take data protection seriously. This globally recognised standard helps organisations design and operate an effective Information Security Management System (ISMS)—one that’s repeatable, risk-aware, and built to last.
At its heart, ISO 27001 brings your people, processes, and technology into alignment. It’s not about ticking boxes—it’s about understanding your threats and applying controls that fit. No generic band-aids. Just focused, context-aware security.
Every ISMS under ISO 27001 is anchored by three principles:
Confidentiality: Sensitive data is seen only by those who should. No leaks, no guesswork.
Integrity: Data stays accurate, untampered, and trustworthy.
Availability: The right users can access the right data—when they need it. No bottlenecks, no downtime.
Get these right, and you don’t just pass audits—you build a security posture that actually works.
ISO 27001 doesn’t spell out “run a pen test”—but it’s loud and clear on risk. Clause 12.6.1 (Technical Vulnerability Management) expects you to:
That’s where penetration testing, red teaming, and offensive security come in. They go beyond the basics, pressure-testing your defences under simulated real-world attacks. They show you not just what’s broken, but how it breaks under fire.
In practice, organisations aiming for ISO 27001 compliance typically run pen tests:
Security testing isn’t just for auditors—it’s fuel for a living, breathing ISMS that adapts to today’s threat landscape.
Penetration testing is what happens when you stop guessing and start verifying. It’s a hands-on, adversary-style security assessment where ethical hackers simulate real-world attacks on your systems, apps, and infrastructure. The mission? Expose your weak spots before someone else does—and fix them fast.
Forget surface-level scans. Pen tests go deep. Testers think like attackers—chaining exploits, dodging access controls, escalating privileges, and proving what real damage could be done. It’s not about “what could go wrong”—it’s about what actually would.
For ISO 27001, this isn’t just a checkbox exercise. Penetration testing supports Clause 12.6.1 by showing your security controls don’t just exist—they work. It validates your ISMS and keeps your risk management tight, relevant, and defensible.
Bottom line: a pen test gives you proof, not promises—and shows auditors you’re not just playing compliance bingo.
Same goal—very different game.
Vulnerability assessments are your wide-angle lens. They use automated tools to scan systems for known flaws—unpatched software, default credentials, open ports, misconfigurations. They’re fast and efficient, but they stop at detection. They tell you what might be wrong—not what could happen.
Penetration tests zoom in. Ethical hackers take those findings and ask, “So what?” They exploit the gaps, chain attacks, and simulate real breaches to show how vulnerabilities could actually be used against you.
Think of it like this: a vulnerability assessment says the door is unlocked. A pen test walks through, checks the valuables, and tells you what would’ve been stolen.
For ISO 27001, both matter. The standard expects more than just a list of issues—it wants proof you can identify, evaluate, and manage real risk. Run both, and you turn your security from theoretical to tactical.
Penetration testing for ISO 27001 isn’t just about running a few scans—it’s about tailoring your testing to the real threats your business faces. From your network to your people, each layer needs scrutiny. A one-size-fits-all approach won’t cut it.
Here are the five most critical types of penetration tests to consider:
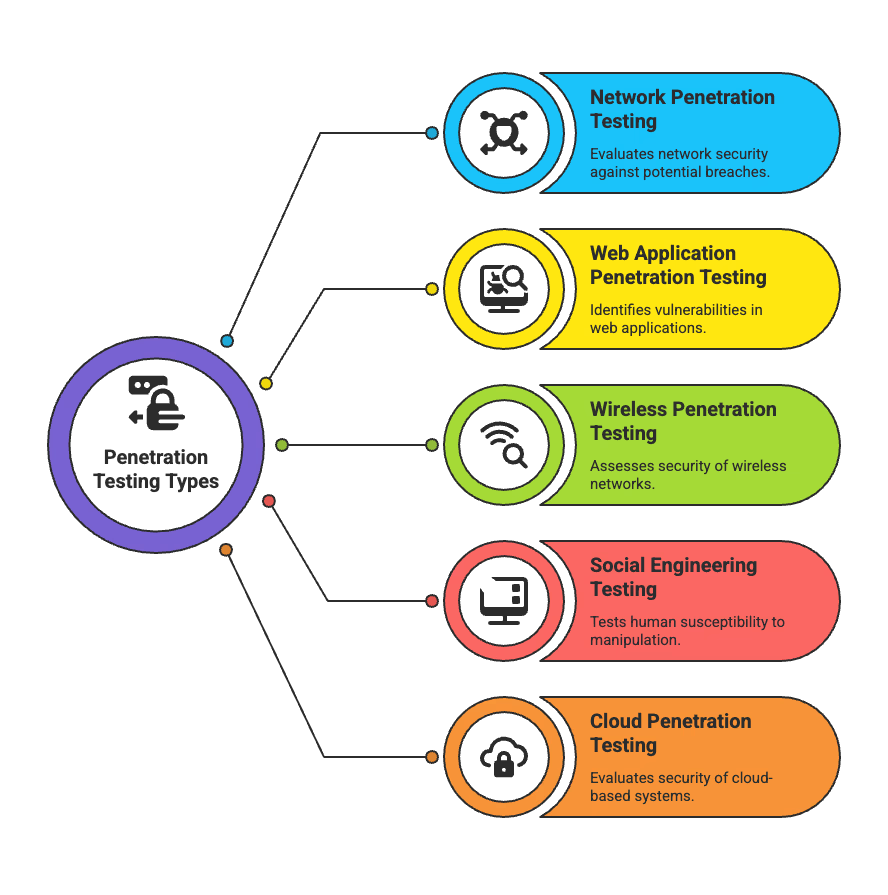
Types of Penetration Testing
Each of these targets a different part of your attack surface—and skipping any one of them could leave a blind spot. Let’s break them down:
Network penetration testing targets both internal and external infrastructure. It hunts down exposed ports, outdated services, misconfigurations, and insecure protocols—basically, anything that gives attackers a foothold. Your network is your backbone, and this test makes sure it’s not also your weakest link.
Web application penetration testing focuses on your front-facing apps—especially those handling sensitive data. It simulates attacks like SQL injection, XSS, and broken authentication to see if login forms, APIs, and user input fields could be weaponized against you.
Wireless penetration testing evaluates your Wi-Fi landscape. It looks for weak encryption, rogue access points, or misconfigured networks that let attackers breach your perimeter without ever plugging in. Unsecured airspace? That’s free real estate for hackers.
Social engineering testing puts your people to the test. Phishing emails, fake tech support calls, and baited USBs are all fair game. It’s less about breaking systems and more about testing awareness—because even strong tech fails if your staff clicks the wrong link.
Cloud penetration testing dives into your IaaS or SaaS environments—AWS, Azure, Google Cloud, and the rest. It checks for open S3 buckets, misconfigured IAM roles, exposed secrets, and other common cloud missteps. Just because it’s managed doesn’t mean it’s secure.
Blending these testing types gives you more than just compliance—it gives you clarity. For ISO 27001, that’s what matters: proving you understand your risks and are actively managing them.
ISO 27001 doesn’t just want you to slap on a few firewalls and call it a day. It demands proof—real, tested, continuous proof—that your security controls actually work. That’s where penetration testing comes in.
Anyone can claim they're “secure.” A pen test puts that claim under pressure. Ethical hackers simulate real attacks to expose weaknesses that policies alone won’t catch—whether in your tools, your tech stack, or your team. It’s how you meet ISO’s risk-based mandates under Clause 6 and test technical controls under Clause 12.
A good pen test doesn’t just hand you a PDF—it tells you what needs fixing now. Whether it’s tightening access, patching misconfigurations, or preparing for phishing campaigns, this is the kind of feedback that hardens your defense and sharpens your response.
When auditors come knocking, your pen test reports are your receipts. They show that your security program isn’t just reactive or theoretical—it’s tested, validated, and improving over time. That’s how you move from compliance to credibility.
A pen test isn’t just a technical drill—it’s a reality check for your controls. If you're aiming for ISO 27001, here’s how to run a test that actually moves the needle.
The key steps for conducting an ISO 27001-compliant penetration test are:
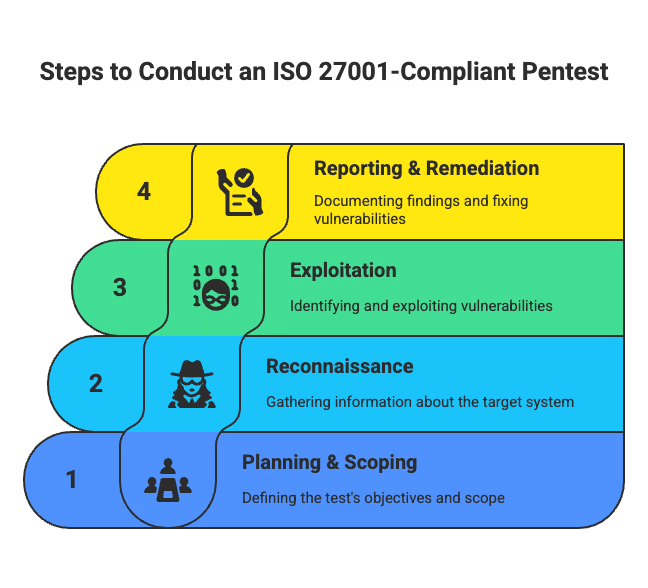
Steps to Conduct an ISO 27001-Compliant Pentest
Let’s go into each step to see what ISO 27001-ready pen testing really looks like.
Define what’s in play—and what’s at stake.
Before any test begins, nail down the why, what, and how.
Think of this step as aligning your offensive testing with your organization’s actual risk appetite.
Study the terrain like an attacker would.
This is all about gathering intel.
You're not launching attacks yet—just laying the groundwork.
Turn findings into controlled chaos.
Now, test the cracks. Ethically.
This isn’t about breaking things for fun. It’s about demonstrating how bad it could get if left unpatched.
Translate risks into actions.
A good report is more than screenshots—it’s a roadmap.
The goal? Help teams close gaps fast—and prove to auditors that your security program isn’t theoretical.
Pen testing for ISO 27001 isn’t a one-and-done exercise. To stay compliant—and secure—you need a structured, consistent approach. Here’s how to do it right.
ISO 27001 doesn’t prescribe a fixed schedule, but “set it and forget it” won’t cut it.
Real-world attacks don’t wait for your calendar—your testing shouldn’t either.
Who should do the testing? It depends.
Third-party ethical hackers bring a fresh, unbiased view—and often uncover risks your internal team might overlook.
In-house teams know your systems intimately and can perform regular, lower-impact assessments.
Best of both worlds? Use third parties for formal assessments and internal teams for ongoing hygiene.
It’s not either-or. It’s both—and it works better that way.
Compliance lives and dies by documentation.
Keep detailed reports on every pen test—what was tested, what was found, and how you responded.
Track remediation progress to show you're closing gaps, not just identifying them.
Update records regularly. Stale documentation can sink an audit.
Bottom line: Good pen testing is about consistency, credibility, and clean paperwork. Get those right, and ISO 27001 compliance becomes a whole lot easier.
Pen tests can fall flat when the basics are overlooked. Here are common ISO 27001 missteps—and how to sidestep them.
Testing only a slice of your infrastructure leaves major blind spots. If APIs, cloud services, or third-party systems aren’t in scope, you're not simulating real-world risk. Define scope with input from all key stakeholders.
A pen test report isn’t a trophy—it’s a to-do list. Skipping remediation or failing to verify fixes puts your compliance (and security) at risk. Always follow up, especially on high-risk findings.
Cyber threats don’t rest—and neither should you. Treating pen testing as a yearly checkbox undermines its value. Continuous testing and retesting should be part of your ongoing security process.
When findings don’t reach the right teams—or aren’t understood—nothing changes. Pen test insights need to flow clearly across security, IT, and leadership.
Bottom line: Pen testing isn’t just a task. It’s a strategy. Do it holistically, and it becomes a real ISO 27001 enabler—not just an audit artifact.
Penetration testing isn’t just a checkbox for ISO 27001—it’s your frontline defense against unknown risks. While the standard gives you flexibility in how you manage security, pen testing brings that strategy to life. It doesn’t just uncover vulnerabilities—it exposes what they actually mean for your business, in real-world terms.
Done right, penetration testing gives you more than just a report. It gives you clarity. You’ll know which weaknesses matter, how attackers might exploit them, and what needs fixing—now, not later.
By building regular testing into your security rhythm, you:
But beyond compliance, pen testing helps shift your mindset from reactive to resilient. It’s how modern organisations stay ahead—not just of audits, but of attackers. And in today’s threat landscape, that’s not optional.
Whether you're pursuing ISO 27001 or SOC 2, the right VAPT approach strengthens both compliance and real-world confidence—internally and externally. So don’t treat it like a formality. Use penetration testing as a strategic tool to harden your defences, test your assumptions, and build a security program built to last.

Senior Pentest Consultant