0%
Ever wondered why penetration testing quotes swing from a few thousand dollars to well over $100,000 for what seems like the same service? You’re not alone. Most organizations land somewhere in the middle—$10,000 to $30,000 for a thorough assessment. But here’s the truth: there’s no such thing as a “standard” pen test. Your systems, your applications, and your risks are unique. Why would your security testing be any different?
Investing in penetration testing isn’t just about paying for a report. It’s about buying expertise, foresight, and protection. The costs may seem high, but consider the alternative: a single breach can cost millions in damages, regulatory fines, and lost customer trust. Compared to that, a $20,000 test looks more like insurance than an expense.
A well-scoped penetration test uncovers hidden vulnerabilities, informs risk management decisions, and strengthens incident response capabilities. It’s not a checkbox—it’s a proactive strategy to prevent financial and reputational disaster.
Understanding the cost of a pentest and how it varies by type is crucial. Next, we’ll break down the average cost of a pentest by test type so you can plan your security investment with clarity.
Pentesting costs vary widely because not all tests look the same. Each type—web app, cloud, mobile, infrastructure—uncovers different risks, using different tools and levels of expertise. Below is a breakdown of how much you can expect to pay depending on the kind of test your business needs.
Web application tests typically cost $4,000 – $30,000, averaging around $12,500. These assessments dig into authentication, session management, and logic flaws across your web apps.
Factors that increase cost:
Expect $5,000 – $40,000 for mobile testing, averaging $25,000 for iOS and Android combined. These tests uncover insecure storage, API flaws, and poor encryption.
Price is influenced by:
Internal infrastructure tests usually range $5,000 – $35,000, depending on the size and network complexity. These tests simulate internal attacker movement and privilege escalation.
Costs rise with:
External pentests focus on internet-facing assets and typically cost $2,000 – $20,000. They’re simpler, faster, and don’t require internal access.
Why it’s cheaper:
Cloud pentests range $10,000 – $50,000, examining misconfigurations, IAM flaws, and exposed APIs.
Costs depend on:
IoT testing starts around $8,000 and can exceed $50,000, while full product assessments may surpass $100,000.
Factors:
Red team exercises are the most intensive, costing $30,000 – $150,000+. These simulate real-world attacks across people, networks, and apps—often over several weeks.
Price drivers:
Spear phishing simulations run $3,000 – $15,000, testing employee awareness and real-world response.
Key points:
Penetration testing costs scale with depth and realism. Basic scans might flag surface issues, but expert-led manual testing exposes real attack paths—before attackers do.
Behind every pen test quote lies a reality most vendors won't tell you upfront. You're not just buying a report. You're buying expertise, tools, time, and follow-through. Here's exactly where your money goes.
Day rates form the backbone of every quote:
Experience costs more. But it finds vulnerabilities that junior testers miss and ensures your systems are tested thoroughly, reducing the likelihood of costly oversights later.
Commercial security tools cost serious money—and those costs get passed to you:
Automation reduces manual hours, but premium tools deliver deeper insights and allow testers to identify complex vulnerabilities that simple scans would miss. You’re paying for capability, not just time.
Post-testing support separates quality providers from scan-and-dump operations:
Documentation eats up significant consultant time:
Vendors offering rock-bottom prices are cutting corners somewhere. The cheapest option rarely delivers what you actually need. Paying for thorough testing ensures issues are properly identified and fixed, saving time, cost, and risk down the line.
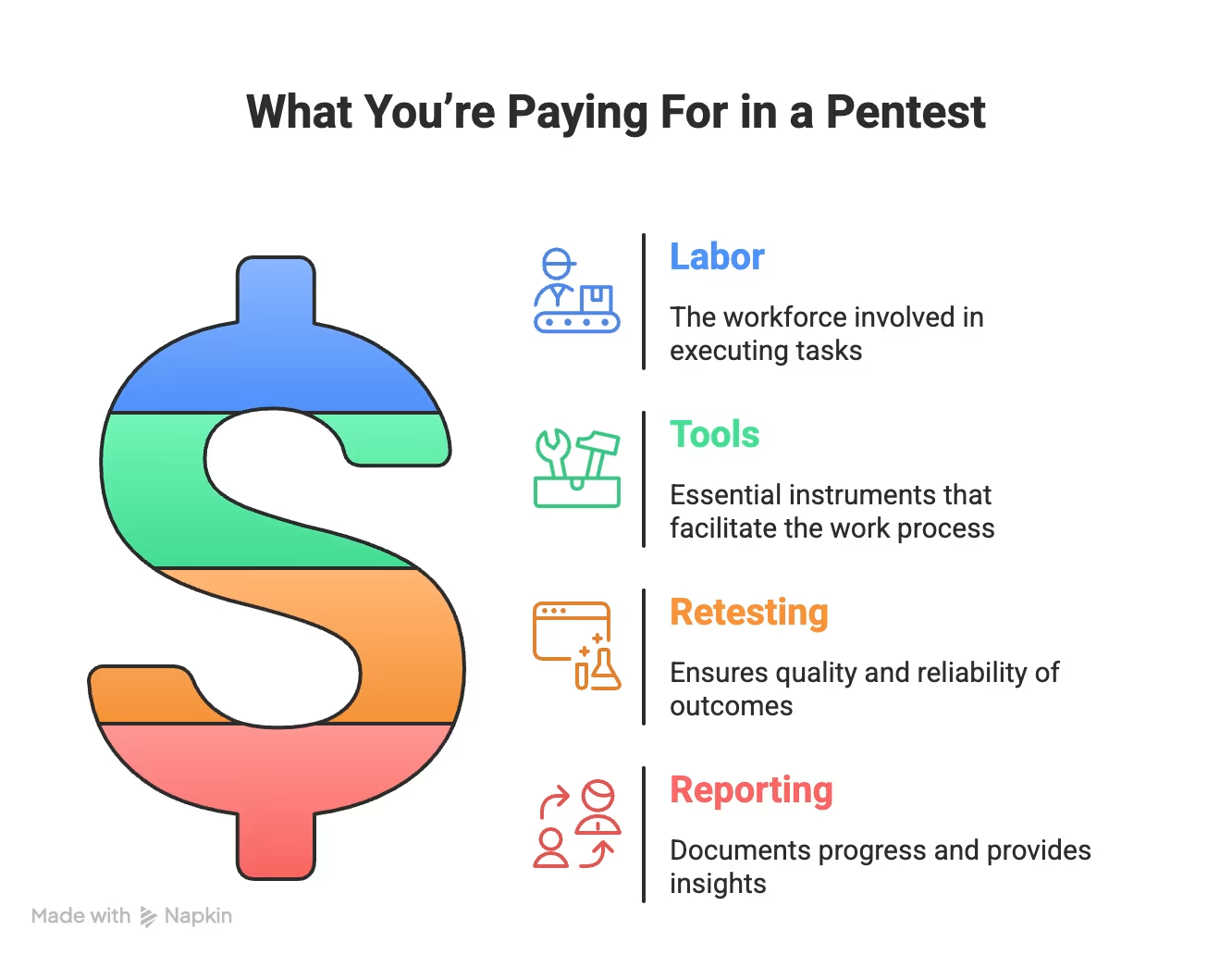
What You’re Paying For in a Pentest
Six factors control what you'll pay for quality pen testing. Master these, and you'll never get blindsided by surprise costs again.
Simple truth: bigger environments cost more.
Testing includes:
Key areas affecting price: web apps, mobile apps, network infrastructure, cloud services, IoT devices. Complex, interconnected systems create a multiplier effect, often requiring more than double the effort of standalone applications.
You get what you pay for.
Tester qualifications directly impact costs:
Experienced testers provide thorough testing and actionable insights. Higher upfront costs translate to better long-term value.
The approach you choose changes everything:
Black box takes more discovery time but may miss internal flaws. White box allows comprehensive analysis but costs significantly more.
Location affects pricing:
Regulatory frameworks increase cost:
Your tech stack dictates pricing:
Modern infrastructures with APIs and microservices demand specialized tools and expertise—higher quality, higher costs.
Here's the dirty secret about penetration testing quotes: they can swing from $5,000 to well over $100,000 for what looks like the same service. Security managers stare at these numbers thinking: "What am I actually paying for?" Fair question. The industry has some explaining to do.
The gap between cheap and quality testing is massive.
Bargain-basement testing ($5,000–$10,000):
Proper comprehensive testing ($25,000–$50,000):
In the industry, if a penetration testing offer seems unusually cheap, it usually indicates lower quality. Fixing a vulnerability in production costs 100 times more than during design. Ouch.
Working with a tighter budget? External testing is a solid starting point:
What you get: scope definition and pre-testing reconnaissance, vulnerability identification and exploitation, documentation of findings, and initial remediation guidance.
Size matters. Big time.
Understanding VAPT testing cost helps organizations budget accurately for security assessments.
Different regions play by different rules. In India, basic scans start at ₹40,000 ($480), while complex infrastructure can reach ₹25,00,000 ($30,000).
With the average U.S. data breach at $10.22 million, even a $30,000 comprehensive test delivers a potential 340:1 ROI. That’s not an expense—it’s the bargain of the century.
Here's the truth about pricing models. Most vendors won’t explain this upfront, but understanding how they structure costs can save you thousands.
These are the main pentesting pricing models:
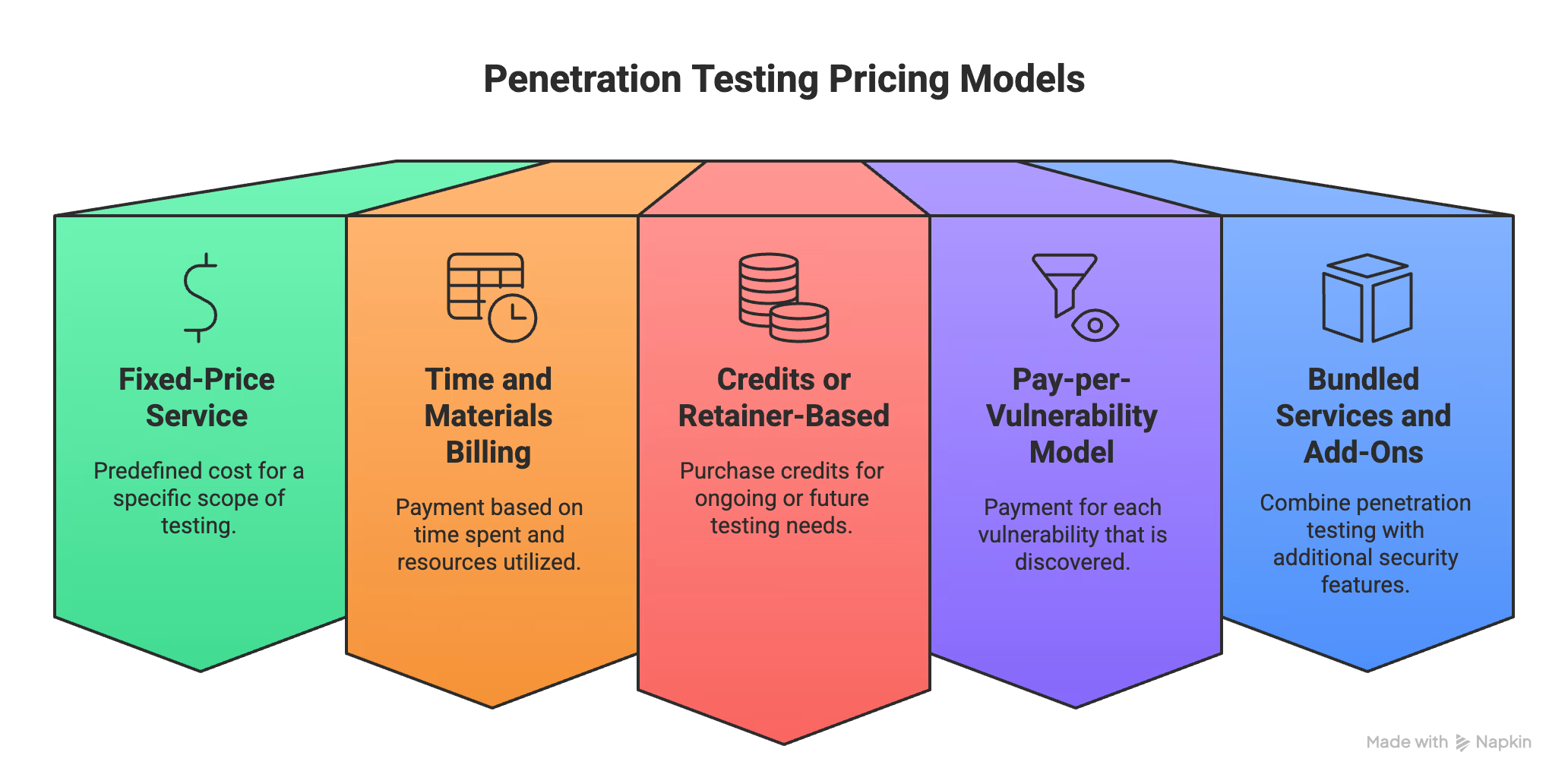
Penetration Testing Pricing Models
Let’s get into each of these in detail.
The "set it and forget it" approach. You know exactly what you’re paying before you start.
Sounds simple? Until your environment is more complex than expected, leaving you with incomplete testing or surprise bills. Some providers offer $995 fixed price for up to 25 external IPs—report included.
Pay for what you actually get tested. Flexible, but potentially expensive.
The catch: without clear boundaries and solid project management, costs can spiral. Communication with testers isn’t optional—it’s survival.
Buy security testing "credits" in bulk, like a gym membership for vulnerabilities.
Credits typically expire in 12 months, so this works for frequent testing, not one-off projects.
Only pay for actual security issues found.
This flips traditional thinking: pay for problems discovered, not hours spent.
The "combo meal" of security testing.
Just ensure the bundle matches your needs. No point paying for mobile testing if you don’t have mobile apps.
Which model works best? It depends on your situation, budget predictability, and testing frequency. Understanding these options ensures you pay for value, not just hours or tools, and get the security coverage your organization truly needs.
Picking the right pen testing partner isn't just about price. It’s about finding someone who won’t waste your money on fancy reports that say nothing useful. Most vendors will tell you what you want to hear. Here’s what you actually need to know.
Certifications matter, but not all are equal:
Check that certifications are current and ask for proof. OSCP holders who passed within three years can apply for CREST Registered Tester equivalency. Don’t just take their word for it.
Certifications are good, but experience matters more:
Generic experience doesn’t cut it. You want someone who’s seen your type of setup before.
The report is what you’re paying for. Make sure it’s worth reading:
Many vendors include one free remediation verification within 30 days of testing. That’s table stakes, not a bonus.
Red flags include:
The average cost of a penetration test reflects real expertise. Quotes that seem too good to be true are often just vulnerability scanning, not actual penetration testing. You get what you pay for—pay for quality, or pay for problems later.
Penetration testing isn’t an expense—it’s insurance. Spend $10,000 to $30,000 on quality testing now, or risk $9.36 million in breach recovery later. That’s a 300:1 ROI most CFOs would kill for—and the smartest security investment you’ll ever make.
But here’s what most blogs don’t tell you: every environment is different. A startup’s single web app doesn’t need the same scope—or spend—as an enterprise managing thousands of endpoints, APIs, and users. Your pentesting budget should reflect your actual risk surface, not some “average” that looks good in a report.
If a quote sounds too good to be true (below $4,000), it probably is—automated scanning dressed up as testing. Real penetration testing demands skilled humans who think like attackers, not tools that just list vulnerabilities. The best programs balance cost with credibility: experienced testers, actionable reports, and remediation insights that actually help your team close gaps fast.
Because in the end, you’re not buying a report—you’re buying peace of mind. Pentesting is how you stay ahead of the next breach, not part of it.
#nothingtohide when it comes to cybersecurity budgeting.

Senior Security Consultant