0%
Ever wondered why security experts seem so worried about AWS these days?
Here’s the uncomfortable truth: over 2,300 cyberattacks happen every single day. And attackers? They’re not wasting time on obscure zero-days. They’re targeting the basics—misconfigured cloud resources, open security groups, unpatched EC2 instances. The stuff you meant to fix last sprint.
This isn’t theoretical. It’s happening right now to organizations running on AWS—big and small.
The cloud moved fast. Security didn’t. AWS environments are now sprawling, decentralized, and dynamic. If your vulnerability scanning strategy still involves manual audits and quarterly checks, you’re already behind.
And here’s where it gets dangerous: AWS secures the infrastructure you build on. But your instances, S3 buckets, Lambda functions, and IAM policies? That’s all you.
Too many teams assume Amazon’s got it covered end-to-end. They don’t. And attackers know exactly where those blind spots live.
The good news? AWS vulnerability scanning has evolved. The tools, techniques, and even Amazon Inspector itself have grown up—fast. Modern AWS scanners deliver continuous detection, automated risk scoring, and seamless integration with your cloud workflows.
Let’s break down what modern scanning actually looks like in 2025, and why it might be the most critical security layer in your entire cloud stack.
AWS vulnerability scanning continuously identifies security weaknesses across your cloud environment. A reliable vulnerability scanner AWS teams trust highlights misconfigurations, exposed secrets, and outdated software—before attackers can exploit them. It checks EC2 instances, Lambda functions, containers, storage, and infrastructure-as-code templates.
Modern scanners also provide context-aware risk scoring to highlight the most critical issues, helping teams focus on what could cause the most damage if exploited. This combination of detection, prioritization, and actionable insights ensures teams can address vulnerabilities efficiently and maintain a strong AWS security posture.
Why it matters in 2025:
Continuous Detection: Finds vulnerabilities in real-time rather than waiting for quarterly audits, reducing the window of exposure.
Shift-Left Security: Scans code, dependencies, and IaC before deployment, preventing risky workloads from reaching production.
Prioritized Risks: Focuses on the most impactful issues based on exposure, privileges, and exploitability.
Faster Remediation: Integrates with CI/CD pipelines and AWS tools for automated fixes and immediate validation.
Compliance Support: Helps meet PCI-DSS, HIPAA, and CIS standards while maintaining audit readiness.
In today’s dynamic cloud environments, cloud vulnerability scanning is a foundational layer of defense.Performing a regular vulnerability scan AWS ensures teams catch misconfigurations, exposed secrets, and outdated software before attackers exploit them.
Most AWS environments don’t get breached because teams skip scanning. They get breached because teams scope it wrong. A shallow scope creates blind spots, and blind spots are where attackers live. Real AWS vulnerability scanning isn’t about checking “important” assets — it’s about mapping the full attack surface, everything attackers can see, reach, and exploit.
A strong scope covers every AWS account and region, not just production. It includes EC2 instances, Lambda functions, containers, and forgotten AMIs. It scans S3 buckets, EBS snapshots, RDS databases, and storage that can silently expose data. It goes deeper into IAM users, roles, policies, stale access keys, and cross-account trust relationships.
It also inspects security groups, NACLs, open ports, and public endpoints. Dev, test, and temporary environments are never skipped, and neither are Infrastructure-as-Code templates or embedded secrets. Good scope doesn’t chase visibility. It chases the attacker's reality.
What separates effective AWS vulnerability scanning from amateur hour?
It’s not the tools—it’s how you use them.
A strong process reduces false positives, speeds up remediation, and scales with complex cloud environments. The most secure teams follow a clear, repeatable workflow built around five stages:
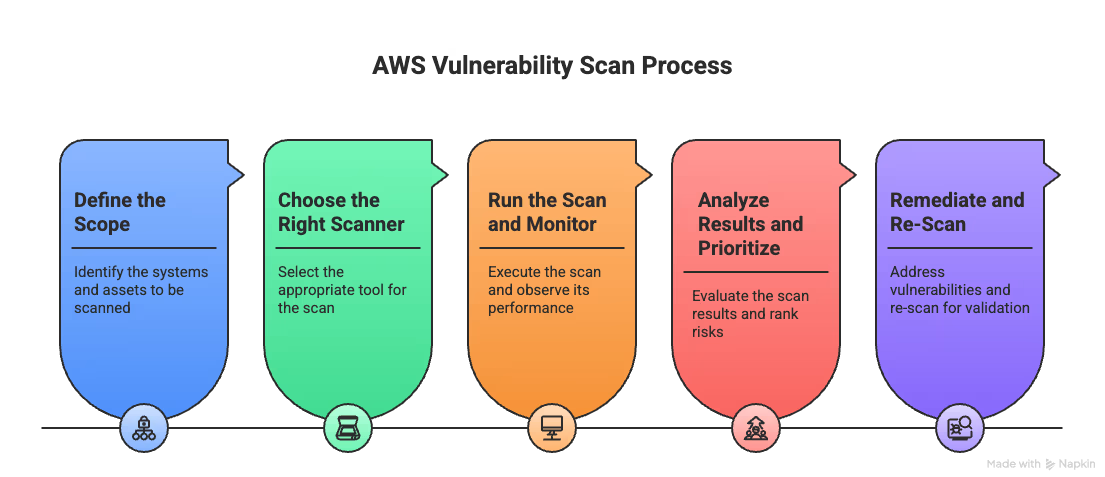
AWS Vulnerability Scan Process
Let’s dive into each step and break down what effective scanning really looks like in 2025.
You can’t protect what you don’t know exists.
Your team should:
Clear scoping keeps scans focused, reduces noise, and makes results actionable.
Look for:
Amazon Inspector is strong for discovery, but combining it with Prowler, CloudSploit, or Astra ensures full visibility.
Scanning isn’t one-off—it’s continuous. Use:
Inspector scans new instances hourly and performs network reachability checks every 12 hours. Monitor performance and fine-tune frequency or resource tagging to maintain efficiency without missing critical assets.
Raw scan data is noise until context is applied. Your team should:
Inspector’s risk scores highlight what truly matters, focusing attention on vulnerabilities that pose real threats.
Detection is just the start. Fixing and verifying is where security is earned. Use:
Finally, re-scan to confirm closure. Tools like Patch Manager and Security Hub can automate this loop.
Fix it. Re-scan it. Validate it. Repeat.
That’s the AWS scanning workflow that actually works in 2025.
Choosing the right scanning tool isn’t just about features—it’s about what actually works for your environment. Teams using purpose-built scanners detect vulnerabilities 37% faster than those relying on manual checks.
Here are five tools that consistently deliver:
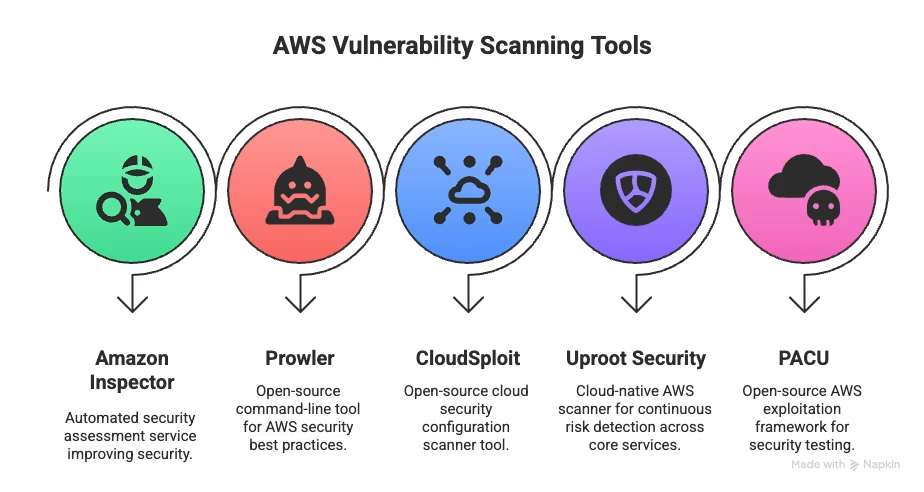
AWS Vulnerability Scanning Tools
Each tool brings something unique to the table—whether it's deep AWS integration, compliance checks, or offensive testing capabilities. Let’s take a closer look at what each one offers and where it shines:
AWS’s native vulnerability management service has matured significantly. It now automatically discovers and continuously scans EC2 instances, container images, Lambda functions, and code repos.
What sets it apart:
Amazon Inspector is tightly integrated with AWS, making it a strong baseline scanner for most environments.
This open-source CLI tool is built for AWS security and compliance assessments.
Highlights:
Prowler is a go-to for auditing IAM policies and validating compliance.
Now part of Aqua Security, CloudSploit scans your AWS environment for misconfigurations and policy violations.
Key features:
It's ideal for teams needing continuous visibility across hybrid cloud setups.
Uproot Security focuses on full-stack cloud security scanning—from infrastructure to workloads to identities. Its strengths lie in actionable findings and seamless integration.
Key features:
Uproot Security is especially valuable for teams that need security insights tied to actual business impact—not just raw CVE counts.
PACU is an open-source offensive testing tool focused on IAM misconfigurations.
It allows red teams and defenders to:
Great for understanding how attackers might move laterally in your AWS setup.
No single tool covers it all. Most teams combine Amazon Inspector with third party vulnerability tools like Prowler or CloudSploit to close gaps and strengthen overall cloud posture.
Selecting the right AWS scanner is crucial—one that integrates seamlessly with your resources, reduces false positives, and works alongside cloud vulnerability scanners for broader visibility. Not all AWS vulnerability scanners are created equal. Choosing the right one depends on how your environment scales, how your teams operate, and how much visibility you need across workloads.
Consider how the tool fits into your broader AWS vulnerability management strategy, including continuous monitoring, CI/CD integration, and compliance reporting. Here’s what to look for when choosing one:
Your scanner should connect seamlessly with AWS services like EC2, Lambda, ECS, and ECR. Native integration means no complex setup, real-time asset discovery, and full visibility across dynamic resources. It also helps ensure your scans stay aligned with AWS’s shared responsibility model.
Modern environments change by the minute. The tool you choose should support continuous scanning that automatically adapts to new instances or configurations. Context-aware intelligence—understanding which assets are internet-facing or high-privilege—helps you focus on the vulnerabilities that actually matter.
Security shouldn’t start in production. A strong scanner integrates with your CI/CD pipeline to scan code, dependencies, and infrastructure-as-code templates before deployment. Catching vulnerabilities early prevents rework and reduces cost.
Detection is only half the job. Look for scanners that provide clear remediation guidance, integrate with issue trackers like Jira or ServiceNow, and trigger automated fixes using AWS tools or custom workflows.
Choose a tool that aligns with standards such as PCI-DSS, ISO 27001, HIPAA, and CIS benchmarks. Automated compliance reports make audits smoother and give leadership clear visibility into your security posture.
In short, pick a scanner that scales with your AWS footprint, fits naturally into your workflows, and turns vulnerabilities into rapid, reliable action.
Running occasional scans isn’t enough. Organizations that treat scanning as a discipline—not a checkbox—experience 76% fewer incidents.
Manual scanning is unreliable. You’ll miss things—guaranteed.
Here’s what actually works:
Automated scanning detects vulnerabilities 37% faster, responding in near real-time to configuration changes.
Fixing vulnerabilities in development is six times cheaper than fixing them in production.
Amazon Inspector integrates with CI/CD workflows via the SBOM Generator and Scan API, enabling you to:
This creates security gates that block insecure code from deploying.
Generic scans won’t meet regulatory standards.
With Chef InSpec, you can run targeted scans using 100+ profiles mapped to PCI-DSS, HIPAA, and CIS benchmarks.
Teams using these profiles meet audit requirements 43% faster.
Without documentation, there's no accountability.
Track:
76% of AWS breaches involve IAM misconfigurations. Don’t be next.
Most teams over-permit out of convenience—then get burned.
Don’t be one of them. Make these best practices your baseline.
Security experts see the same five issues in nearly every AWS environment. These aren’t rare—they’re foundational failures attackers exploit.
AMIs older than 180 days often miss critical patches. Tools like AWS ECR scanning help detect container image vulnerabilities early, ensuring that insecure images never reach production.
Containers with outdated base images are even riskier, offering clear attack paths. While ECR Enhanced Scanning can detect OS and code-level CVEs before deployment, many teams only notice issues after production.
Security groups often go stale, leaving temporary rules wide open. Best practices:
Skipping these steps is a common failure point.
76% of AWS breaches involve IAM misconfigurations. Wildcard permissions like Action: * grant more access than needed. Many teams rarely audit or reduce permissions, and over time, extra access accumulates—creating a higher-risk environment. Regular reviews and stricter permission controls can prevent potential exploits.
Over 58% of S3 buckets lack public access blocks, nearly 40% of buckets and volumes aren’t encrypted, and 88% allow HTTP access. Public EBS snapshots can expose deleted data or credentials. Encryption should always be default, not optional.
Lambda runtimes often include outdated dependencies. Unlike EC2, OS patching isn’t enough—you must manage libraries directly. Fixes:
These five gaps likely exist in your environment now. Don’t wait for a breach to expose them.
Here’s the truth most teams overlook: AWS secures the cloud, not the workloads you run inside it. Their job is to protect the foundation—data centers, servers, networking, and core services. Everything built on top of that layer is your responsibility.
That means managing your own data, IAM roles, application code, configurations, encryption keys, and network settings. If an S3 bucket is left public or an IAM policy is too broad, that’s on you—not AWS.
This is where many security programs stumble. Teams assume “AWS handles security,” only to discover that compliance and protection stop at the hypervisor. Once you understand this division—security of the cloud (AWS) versus security in the cloud (you)—your scanning and remediation efforts become sharper. You stop expecting AWS to close gaps that only your team can fix and start building a security posture that actually matches how the cloud works.
AWS gives you a highly secure cloud—but your workloads aren’t automatically safe.
The shared responsibility model is simple: AWS secures the infrastructure—data centers, servers, networking, and foundational services. Everything running on top of that—the IAM roles, S3 buckets, Lambda functions, containers, and configurations—is your responsibility. Tools like AWS ECR scanning help, but they don’t replace vigilant management.
Vulnerability scanning is your reality check. It exposes blind spots attackers love to exploit, from outdated AMIs and containers to overly permissive IAM policies and public S3 buckets. Regular scanning highlights the most critical risks, helps prioritize fixes, and ensures your security controls actually work.
The goal isn’t just compliance. It’s about knowing your cloud environment inside out before attackers do. Continuous scanning provides visibility, clarity, and confidence—you see what’s vulnerable, what’s patched, and what demands attention next.
Security becomes proactive instead of reactive. It becomes a habit, not a crisis. That’s how modern teams stay resilient in AWS, and why scanning is the backbone of a cloud security strategy that actually works.
If you’re serious about strengthening your AWS security posture and catching vulnerabilities before attackers do, connect with our expert team for a tailored vulnerability assessment—built for modern cloud environments.

Senior Security Consultant