0%
Ever wonder why hackers always seem one step ahead? It’s not magic. It’s the reality of a digital battlefield that’s no longer shifting—it’s being completely rewritten. What once looked like pranks or nuisances has transformed into industrial-scale attacks that can wipe out entire businesses in a single night.
The numbers paint the picture. 72% of organizations report a surge in cyber risks, with ransomware leading the charge. Nearly half now see AI-powered threats as their biggest nightmare—adversarial models that learn faster than defenses can catch them. Phishing has exploded too, with 42% of companies hit by social engineering. Supply chain vulnerabilities? Fifty-four percent of large organizations admit those are their weakest link.
Cybercrime isn’t just about stolen money anymore. It’s about disruption—crippling economies, sabotaging infrastructure, undermining trust. The worst part? The gap keeps widening. Multinationals build fortress-grade defenses, while small businesses are left exposed. Even regional confidence splits wide—just 15% in Europe and North America doubt resilience, compared to 36% in Africa and 42% in Latin America.
That’s the disconnect. And it’s exactly what hackers count on.
Cybersecurity has stopped being a technical problem—it’s now a survival problem. CEOs already name it the top business threat of the decade. And when you see what attackers are using, it’s obvious why. Voice phishing campaigns layered with business email compromise. Deepfakes that impersonate executives. Synthetic identities built with generative AI that slip past security controls like they were designed for it.
The brutal truth? Ninety percent of companies aren’t prepared for this reality. They lack the maturity, the visibility, and the cyber security practices needed to fight back. And that’s not just a gap—it’s an open invitation.
Cyber criminals thrive on weak fundamentals. Outdated patching cycles. Employees who click first and think later. Vendors that haven’t been vetted. These aren’t just small oversights; they’re doorways into your network. Once inside, attackers don’t just steal—they disrupt, manipulate, and destroy.
Cyber security practices in 2025 mean more than antivirus updates or annual audits. They mean embedding security into every layer of business. Training teams to spot deception. Securing supply chains. Testing resilience against AI-enabled threats.
Because here’s the bottom line: without strong practices, you’re not just vulnerable—you’re a target. And survival depends on closing that gap.
"Human error is the single biggest cyber risk—technology is only half the battle." — Satya Nadella, CEO, Microsoft
Your people are either your strongest defense or your weakest link. No middle ground. Around 95% of cyber breaches stem from human error—not malware or elite hackers, but simple mistakes: clicking a bad link, reusing passwords, or trusting a suspicious email. The twist? This weakness is actually an opportunity. Properly trained employees can stop most attacks before they even start.
Social engineering is psychological warfare. Hackers don’t need to break your walls—they convince you to open the gate. Their playbook is predictable once you know it:
Proof? Companies running awareness training cut phishing success rates by 80%.
Remote work changed the game. Coffee shop WiFi is convenient—but it’s also a hacker’s playground. Rule one: never trust public WiFi without a VPN or a secure hotspot. Rule two: don’t leave devices unattended, even for a quick refill. And here’s the tricky part: attackers often impersonate “helpful” IT staff. If someone calls or messages asking for your login, stop. Hang up. Then call your real IT department to confirm. A thirty-second check can save you from a months-long breach.
Security training is like exercise—you can’t do it once and stay strong. Muscle memory matters. Organizations running phishing simulations dropped failure rates to 9.3%, proving repetition builds resilience. Tabletop exercises are your chance to talk through “what if” scenarios in a safe environment. Simulated attacks, on the other hand, show you whether people actually react under pressure. Both are essential. Think of it as training for both the mind and the reflex—because in a real attack, hesitation costs.
Passwords remain the #1 attack vector. The rules are simple:
Strong cyber security practices aren’t just about firewalls or tools. They’re habits. And teams who train, test, and stay sharp aren’t just safer—they’re resilient.
Cyber Security Best Practices for Employees
Your network is your foundation. You can buy the fanciest security tools in the world, but if that foundation is cracked, attackers will find a way in. Every risk you mitigate and every attack you prevent doesn’t just protect your business—it strengthens the overall cybersecurity landscape. The goal isn’t a network that only looks secure on paper, but one that holds up against real-world threats.
Think of your firewall as castle walls—it’s not just a box you plug in and ignore. Harden it before deployment, lock it to “deny all by default,” and review the rules often. Logging isn’t optional—if you can’t see what’s targeting your network, you can’t respond.
Network Segmentation is where the castle gets smarter. Splitting your network into neighborhoods makes attacks easier to spot and contain. High-value assets live in isolated zones, and if one segment is breached, hackers can’t wander unchecked across your digital city.
A VPN creates a private tunnel that keeps traffic invisible to prying eyes. But here’s the mistake many businesses make—having a VPN isn’t enough. You need multi-factor authentication, endpoint compliance checks, and encryption for every connection. Public Wi-Fi without a VPN? That’s like reading your bank PIN out loud in a crowded café.
Every unused port is an unlocked door, and attackers love doors nobody’s watching. Audit your configs regularly, disable inactive ports automatically, and kill inbound access rules unless they serve a documented business purpose. Every cleanup step makes the attack surface smaller.
Zero trust flips the old model on its head. Forget “trust but verify.” The rule now is “verify, then verify again.” In practice:
Zero trust assumes every user and device could be hostile until proven otherwise. It’s not paranoia—it’s survival.
Firewalls, VPNs, segmentation, and zero trust aren’t buzzwords—they’re the pillars of defense. Build strong, test often, and your network becomes a fortress instead of a liability.
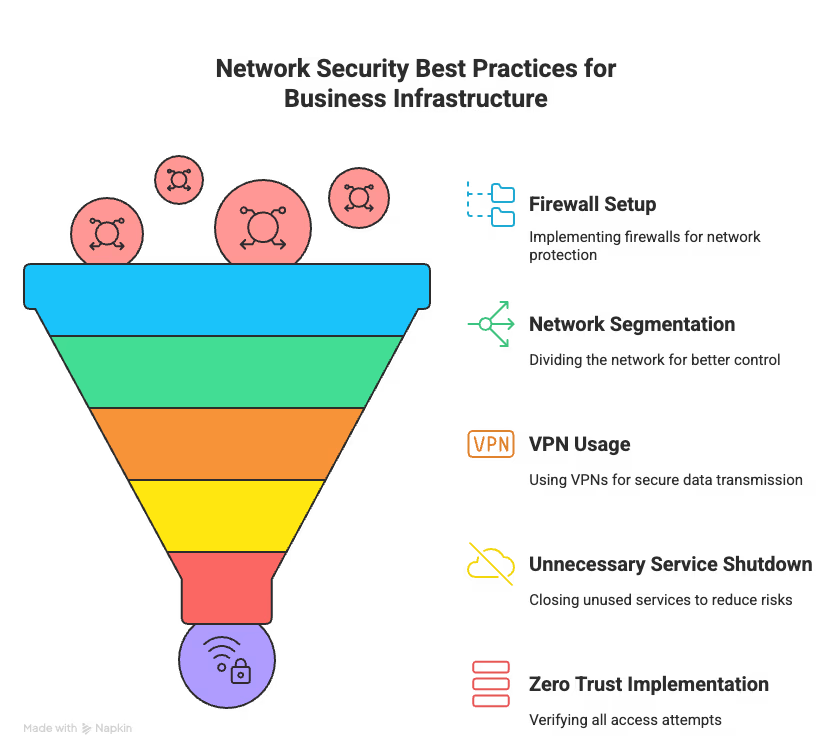
Network Security Best Practices for Business Infrastructure
Compliance has become the biggest driver of security spending in 2025. And honestly? It’s overdue.
75% of the world’s population now has personal data covered by modern privacy laws—up from just 20% in 2020. The message is clear: failing to comply isn’t a slap on the wrist anymore. It’s an existential risk.
Each regulation comes with its own flavor of pain:
GDPR demands accountability. You need proof of strong data protection strategies. Audit logs aren’t technically required, but regulators treat them like essential evidence. Translation: log everything.
HIPAA changed in December 2024. Encrypt ePHI in transit and at rest. Restore critical systems within 72 hours. And yes—annual compliance audits are now mandatory.
CCPA/CPRA gives California residents power over their data. You’ve got 45 days to respond to requests. Need more time? You get another 45—but only if you notify consumers upfront.
Audit logs are both a security control and compliance proof. At minimum, capture:
Store logs for at least 30 days in accessible storage. But regulated industries demand more. HIPAA requires six years. PCI DSS 4.0 wants twelve months, with three months available immediately.
The DOJ doesn’t just look at breaches—they look at whether you did your homework. Risk assessments matter.
A solid process follows five steps: build a cross-functional team, identify risks, analyze likelihood and impact, prioritize, and design mitigation strategies.
And it’s never one-and-done. Expand into new markets, acquire companies, or face new laws? Reassess. Compliance risks evolve as fast as your business does.
Bottom line: In 2025, information security best practices and compliance are the same playbook. Miss either one, and you’re out of the game.
Small businesses get hit hardest in cybersecurity. Same threats as Fortune 500 giants, but with a fraction of the budget. Hackers know it too—43% of breaches target small businesses, betting you can’t afford defenses.
Here’s the good news: you don’t need enterprise cash to build solid security.
Your first line of defense doesn’t need to be expensive:
Norton Small Business covers up to 10 users with real-time protection, VPN, password management, and identity theft monitoring.
Bitdefender blocks malware with minimal system impact—ideal if you need security that doesn’t slow you down.
Surfshark Antivirus is the budget pick—just $72 for two years, perfect for solo shops or very small teams.
Even basic antivirus stops most common threats. When you layer them with other smart moves, you’re already ahead of most small businesses.
Small businesses run on SaaS. But misconfigurations are a hacker’s favorite opening. Here’s how to avoid being an easy target:
Audit app security settings—most defaults are weak or risky.
Turn on MFA everywhere it’s supported. Only 18% of SaaS providers offer it, but when they do, enable it immediately.
Review data sharing permissions regularly—trim access down to only those who need it.
Encrypt data both at rest and in transit. Only 10% of SaaS providers do this by default, which means it’s on you to make sure it’s enabled.
You don’t need to spend big to get powerful defenses:
Find your weak spots, then deploy these tools strategically.
You don’t need deep pockets—just sharp priorities and the right defenses.
“The question isn’t ‘if’ you’ll get breached, but ‘when’—and how you respond.” — Dr. Vinton Cerf, Internet Pioneer and Chief Internet Evangelist, Google
Business continuity is the real test of whether your cybersecurity holds up under fire. And the stakes? Brutal. When ransomware strikes, organizations bleed $53,000 per hour just to stay operational. Preparing for disruption isn’t optional anymore—it’s survival.
Most companies improvise when disaster hits. That’s why recovery stalls and costs spiral.
Here’s what actually works:
Clear roles: Assign an Incident Manager to coordinate, a Tech Manager to restore systems, and a Communications Manager to handle stakeholders.
Regular simulations: Businesses that practice response drills recover 35% faster.
Written playbooks: Document every step—containment, escalation, recovery—so nobody scrambles under pressure.
The payoff is huge. Organizations with tested response teams save an average of $2.66 million per breach.
Follow this and you’ll sleep better:
This simple framework guards against crashes, theft, disasters, and ransomware. For 2025, add one more layer: immutability. At least one backup should be untouchable, no matter what attackers throw at you.
Policies fail when they’re bloated from day one. Smarter approach:
Effective policies should cover disaster recovery, breach response, and system downtime. Because in reality, all three will happen.
Business continuity isn’t about avoiding disaster—it’s about proving your company can take a hit and still stand strong.
Most companies still get cybersecurity wrong. They think it’s all about expensive tools and complex tech stacks. But here’s the truth: the real difference between businesses that crumble and those that bounce back stronger isn’t software—it’s culture.
Right now, two out of three organizations can’t hire the cybersecurity talent they need. Only 14% feel confident they’ve got the right people on their side. That’s not just a hiring issue—it’s a leadership failure. Because culture can fill gaps that headcount alone can’t.
So how do you fix it? Stop treating security like a black box only IT understands. Make it part of everyone’s job. Tie it to performance reviews so it actually matters. Run tabletop exercises on a regular basis—companies that do recover 35% faster when disaster hits. Build safe spaces where employees can admit mistakes and report suspicious activity without fear. And drop the tech jargon—talk to people like people.
Leaders must model it. Teams should normalize it. Individuals need to feel empowered. Because when hackers get smarter, culture—not tech—is what saves you.
Take control of compliance, reduce risk, and build trust with UprootSecurity — where GRC becomes the bridge between checklists and real breach prevention. → Book a demo today

Senior Security Consultant