0%
Ever wonder what happens when healthcare privacy gets a major shake-up? That’s exactly what went down with the HIPAA Omnibus Rule. Released by the Department of Health and Human Services (HHS) on January 17, 2013, this wasn’t just another compliance tweak—it was the most dramatic overhaul of healthcare privacy since HIPAA first launched.
The rollout was quick. The rule became effective on March 26, 2013, and organizations had until September 23 to comply or face steep penalties. Instead of juggling four different privacy and security rules, the Omnibus Rule pulled them into one unified package. The goal was simple: stronger protections for patients, less confusion for providers.
But this update was never just about paperwork. It was about adapting to the digital health era, where electronic records, cloud storage, and mobile access created new risks that old rules didn’t fully cover.
With the Omnibus Rule, breaches had clearer reporting standards, penalties got tougher, and patients gained more control over how their medical data is accessed and used. In short, it redefined healthcare privacy for a new age.
The HIPAA Omnibus Rule is a major update to U.S. healthcare privacy law. The HIPAA Omnibus Rule of January 2013 did what no other update had done before—it consolidated multiple rules into one, expanded patient protections, and increased accountability for organizations handling health data.for organizations handling health data.
It’s often described as the most sweeping set of changes since HIPAA itself launched. Think of it as HIPAA 2.0—a rule that absorbed four separate updates into one, while pulling in provisions from the HITECH Act and the Genetic Information Nondiscrimination Act (GINA). The goal? Rein in the chaos of digital health data and strengthen patient rights.
It reshaped HIPAA across five key areas:
Most importantly, business associates and their subcontractors could no longer sidestep responsibility. For the first time, they were placed under the same obligations as covered entities, closing one of HIPAA’s biggest loopholes.
Remember when business associates could hide behind “it’s not really our problem”? Those days are over. The HIPAA Omnibus Rule flipped the script for any organization handling protected health information (PHI) for healthcare providers and health plans. Before 2013, business associates were only contractually liable—basically playing with house money. After the rule? They face direct regulatory scrutiny and penalties that actually hurt.
Business associates became directly accountable for HIPAA violations. Civil penalties range from $100 to $50,000 per violation, with fines reaching $1.5 million per identical violation type per year. And this liability doesn’t stop at the primary service provider—subcontractors are fully on the hook too.
Violations that can trigger penalties include:
Every subcontractor that creates, receives, maintains, or transmits PHI is now considered a business associate. The Omnibus Rule leaves no room for passing the buck.
The rule clarified that cloud service providers storing PHI are business associates, even if they never actually access the data. This includes: data storage companies, cloud computing platforms, health information organizations, e-prescribing gateways, and personal health record providers. Two key updates made this clear: adding “maintains” to the definition and confirming that cloud providers require BAAs.
Old BAAs became outdated overnight. Updated agreements must now ensure business associates:
BAAs that predated January 25, 2013, had a grace period until September 23, 2014, but eventually, every contract required these provisions. No more hiding behind old agreements—HIPAA responsibilities are now crystal clear.
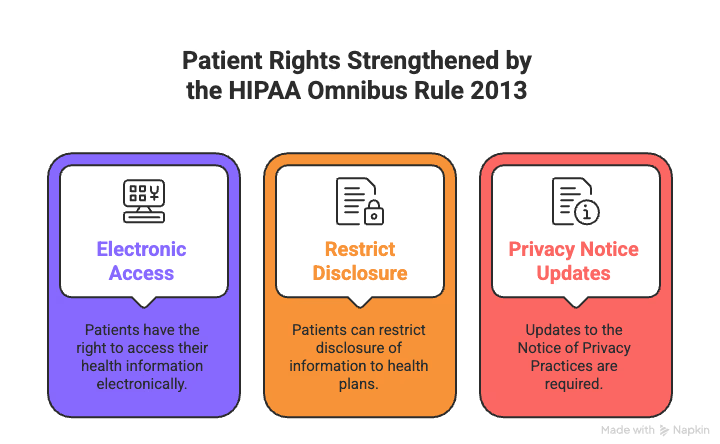
Patient control over health information has been broken for too long. The 2013 HIPAA Omnibus Rule finally fixed that, giving patients real power—not just promises buried in fine print.
Want your health records? You get them. The rule requires covered entities to provide electronic copies of electronically maintained PHI when requested:
For the first time, patients can limit what their insurance company sees. If you pay out-of-pocket for care, you can tell providers not to share that information with your health plan. Providers must flag this info to prevent accidental disclosure.
Patients now have real control over sensitive care. You can:
Privacy notices got a makeover. Updated NPPs now clearly explain:
The Office for Civil Rights and the Office of the National Coordinator for Health IT created model notices providers can use. They must make them available to anyone who asks and post them online. Written acknowledgment is no longer required, cutting down on paperwork.
Bottom line: your health information, your rules.
Patient Rights Strengthened by the HIPAA Omnibus Rule 2013
Think breach notifications were confusing before 2013? You weren’t wrong. The HIPAA Omnibus Rule completely changed when and how organizations report data breaches. No more guessing games, no more subjective calls—everything became clearer and more consistent.
Any impermissible use or disclosure of protected health information (PHI) is now presumed to be a breach requiring notification. Gone are the days of “maybe it’s a breach, maybe it isn’t.” Unless a risk assessment proves a “low probability that the PHI has been compromised,” you must report it.
This puts the burden squarely on healthcare organizations. You need documentation showing either:
Want to skip the assessment? You can go straight to notification. Sometimes the direct route is the safest and simplest approach.
If you do perform a risk assessment, focus on four factors:
Accidentally sending PHI to another hospital is a different risk than sending it to an unsecured third party. Both are breaches, but the risk level and urgency differ.
The old “significant risk of harm” threshold is gone. Now it’s about whether PHI was “compromised,” not whether it might cause harm. HHS eliminated subjective judgment calls, ensuring consistent, transparent reporting across the board.
If PHI was impermissibly exposed, it’s almost certainly reportable under the Omnibus Rule, leaving no gray area for organizations.
Before 2013, healthcare providers often treated your personal health information like a commodity. The HIPAA Omnibus Rule changed that, cracking down on how providers and their partners could use patient data for profit. It wasn’t just a tweak—it set clear boundaries and strengthened patient rights.
The rule drew a line in the sand: no selling patient data without explicit permission. A “sale” is any disclosure resulting in direct or indirect remuneration—cash, credit, or other benefits.
Key requirements:
No wiggle room. If money changes hands, authorization is mandatory.
Marketing now means “a communication about a product or service that encourages recipients to purchase or use it.” Written authorization is required when:
Some communications still don’t need authorization, including: describing the entity’s own services, treatment communications, and prescription refill reminders where payment is reasonably related to costs.
Fundraising rules expanded the types of information organizations can use while giving patients more control. Organizations can use demographic data, department of service, treating physician, outcome information, and insurance status.
Requirements:
Once a patient opts out, that’s it. The only way back is affirmative opt-in. No more sneaky tactics—your data, your rules.
The 2013 HIPAA Omnibus Final Rule didn’t just update privacy—it brought genetic information into the protected zone for the first time. What started with the Genetic Information Nondiscrimination Act (GINA) of 2008 finally got teeth through this rule.
The Omnibus Rule prohibits health plans from using genetic information for underwriting. No more digging through your DNA to set premiums, determine eligibility, or impose pre-existing condition exclusions. This applies to all health plans under the rule—except long-term care plans, which were exempt.
So, what counts as “genetic information”?
What doesn’t count? Age, sex, and standard tests like HIV, blood counts, cholesterol, or drug screenings are excluded. All other genetic information is protected, no matter when it was created.
Covered entities also had to update their Notice of Privacy Practices to reflect these protections. No more hiding the fine print—patients now clearly know how their genetic data will be handled.
In short: if it’s in your genes, it’s protected under HIPAA. Your DNA, your rules.
The Omnibus Rule didn’t just change the rules—it changed what happens when you break them. It introduced a four-tier penalty system with fines ranging from $100 to $50,000 per violation, and annual caps reaching $1.5 million for identical violations.
Penalty Tiers:
Unknowing Violations: $100–$50,000 per violation – when you genuinely didn’t know you messed up
Reasonable Cause: $1,000–$50,000 per violation – when you tried to comply but still failed
Willful Neglect (Corrected): $10,000–$50,000 per violation – when you knew better but fixed it within 30 days
Willful Neglect (Uncorrected): Minimum $50,000 per violation – when you knew better and did nothing
HHS doesn’t automatically slam the maximum penalty. They consider how long the violation lasted, how many people were affected, whether you’ve been a repeat offender, and if anyone was harmed, lost money, or suffered reputational damage.
Good news: if you catch a violation not involving willful neglect and fix it within 30 days, you might avoid a penalty entirely. That’s why keeping detailed records of discoveries and corrective actions is critical.
These fines aren’t theoretical. American Medical Response paid $115,200 for a Right of Access failure. Essex Residential Care shelled out $100,000 for similar issues. Real rules, real consequences, and real money on the line.
Here’s the truth: more than a decade after the Omnibus Rule, many organizations are still failing at HIPAA compliance. Penalties have doubled in the five years since the rule launched. You don’t want to be that organization.
Compliance isn’t a one-and-done task. It requires ongoing effort, including:
Policies also need updates for Omnibus Rule specifics: deceased persons’ information, electronic access requests, limited insurance disclosures, and marketing restrictions.
And don’t think compliance stops there. HHS is preparing new HIPAA regulations for 2025, including technology inventories, semi-annual vulnerability scans, penetration testing, and mandatory multi-factor authentication.
Compliance today isn’t just about avoiding fines—it’s about building strong risk management that protects your patients and your organization. Nail it now, treat it as ongoing protection, and you’ll survive whatever comes next. The choice is yours: get ahead of it, or get hit by it.
Take control of compliance, reduce risk, and build trust with UprootSecurity — where GRC becomes the bridge between checklists and real breach prevention.
→ Book a demo today

Senior Security Consultant