0%
Think AWS is secure by default? That’s the myth attackers are betting on.
The truth is, cloud environments like AWS are only as secure as the people configuring them. One misstep—a public S3 bucket, an overly generous IAM policy, a forgotten access key—and you’ve just handed an attacker the keys to your kingdom.
That’s why AWS penetration testing matters now more than ever. But here’s the twist: testing cloud infrastructure isn’t like testing traditional systems. You’re not just scanning for open ports—you’re navigating IAM roles, API gateways, serverless logic, and ephemeral resources that spin up and disappear in minutes.
And AWS has rules. You can’t just run scans or brute force everything—you need to know what’s in scope, what’s off-limits, and how to test without triggering alarms or violating terms of service.
This guide is your tactical playbook. No fluff. Just straight-up strategies, tools, and real-world testing workflows for securing your AWS stack.
Because cloud breaches don’t start with malware—they start with misconfigurations. Let’s make sure yours aren’t next.
AWS pentesting is a proactive security practice that simulates real-world cyberattacks on your AWS (Amazon Web Services) infrastructure—whether it’s EC2 instances, S3 buckets, IAM policies, or serverless apps. The goal? To uncover vulnerabilities before attackers do. By mimicking the tactics of threat actors, pentesters can expose hidden misconfigurations, excessive permissions, exposed services, or weak authentication flows that may otherwise go unnoticed.
This approach goes beyond traditional vulnerability scanning. It validates the effectiveness of your security controls in real-world conditions and reveals the actual impact of potential exploits. The result: a clear picture of where you’re secure—and where you’re not.
For companies operating in highly regulated industries, AWS pentesting also plays a crucial role in meeting compliance requirements such as SOC 2, ISO 27001, PCI-DSS, and HIPAA. But even outside compliance, it's a smart, continuous way to harden your cloud posture against evolving threats.
In short, it’s not just about finding bugs—it’s about building cloud environments that can withstand real-world attacks.
AWS penetration testing isn’t just about ticking a compliance box—it’s a strategic weapon against the unknown. In a cloud world where environments shift rapidly and threats evolve even faster, pentesting gives you the clarity and control needed to stay ahead.
Pentesting uncovers what you don’t see—misconfigured IAM roles, open S3 buckets, overly permissive security groups, and exposed APIs. Finding and fixing these issues before attackers do is the fastest way to reduce cloud risk.
You’ve set up firewalls, IAM policies, and monitoring—but do they actually work under pressure? Penetration testing simulates real attack paths to test the effectiveness of those defenses in live conditions.
Frameworks like SOC 2, PCI-DSS, HIPAA, and ISO 27001 require ongoing security validation. AWS pentesting provides proof of due diligence—helping you pass audits and avoid penalties.
Pentesting helps you move from reactive to proactive. Instead of waiting for alerts (or breaches), you identify exploitable issues early, giving your team time to patch, reconfigure, and harden.
Bottom line: Pentesting helps secure what your cloud team builds—before someone else breaks it.
Before you dive into penetration testing on AWS, you need to understand one core principle: the Shared Responsibility Model. It’s not just a policy—it’s the blueprint for who owns what when it comes to cloud security.
AWS is responsible for the security of the cloud. That means protecting the infrastructure that runs its global services—physical data centers, networking, hardware, and the foundational software powering EC2, S3, RDS, and more. They ensure the availability, durability, and resiliency of the cloud platform itself.
You, the customer, are responsible for security in the cloud. That includes your virtual machines, S3 bucket permissions, IAM policies, encryption, patching, firewall rules, and how your applications handle data. If a misconfigured EC2 instance leaks data or a public S3 bucket exposes sensitive files, that’s on you.
This model isn’t just conceptual—it directly impacts pentesting. AWS permits testing certain services without prior approval, as long as you stay within defined boundaries. That means you can test, validate, and lock down your environment—without navigating unnecessary red tape.
Bottom line: AWS secures the foundation. You secure everything you build on top of it.
Cloud pentesting isn’t plug-and-play—it’s controlled chaos with structure. Unlike traditional infrastructure, AWS introduces added layers: IAM boundaries, ephemeral compute, and service-specific limitations. If you don’t plan well, you’ll either miss key exposures or set off alarms.
Here’s how to prepare with precision:
Decide exactly what’s in bounds. Are you testing EC2 instances, S3 buckets, Lambda functions, VPCs, or internal APIs? Be specific. Vague scoping leads to wasted effort—and legal risk.
AWS has rules. Make sure your testing plan respects the Shared Responsibility Model and AWS’s official penetration testing policy. Route 53, denial-of-service simulations, and anything that hits shared infrastructure is off-limits.
Document everything. This includes:
Before touching anything, enumerate. Identify IAM roles, APIs, open endpoints, and misconfigured services—especially public-facing ones. Tools like Prowler and AWS CLI can help here.
When you prep right, your test becomes not just safer—but smarter. You reduce noise, avoid false alarms, and surface the real risks hiding in your cloud.
Think you can just scan everything in your AWS account? Not quite.
AWS may support pentesting—but only on their terms. Cross the wrong line, and you could trip alarms, violate policies, or even get your account flagged. So before you test, know the rules.
AWS’s penetration testing policy lays out what’s fair game—and what’s completely off-limits.
If it’s your own environment, you’re generally in the clear to run:
These are red flags—even in your own stack:
One thing’s clear: You can test in AWS, but only within strict boundaries.
So you’ve locked down your scope, understood the rules, and cleared the paperwork. Now it’s time to put your plan into action. AWS pentesting isn’t just about running scans—it’s about simulating real threats in a cloud-native way. From environment setup to vulnerability discovery, every move should be precise, compliant, and well-documented.
The core steps include:
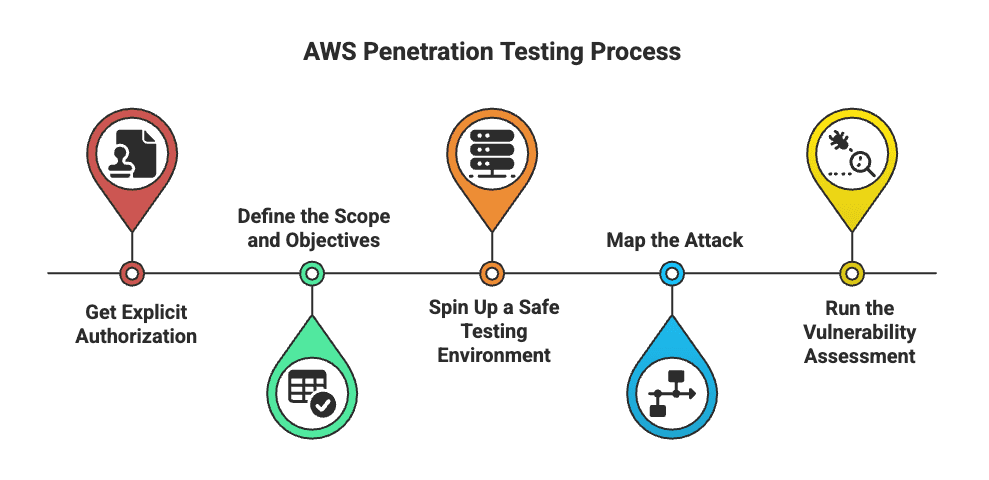
AWS Penetration Testing Process
Let’s dive into each phase to understand how to execute a clean, compliant, and impactful AWS penetration test.
This isn’t optional. You need written approval from the AWS account owner (or organization) before testing anything—even if it’s your own cloud. It protects everyone involved and avoids legal fallout.
Don’t just test blindly. Know exactly what you're targeting—whether it's EC2 instances, S3 buckets, Lambda functions, or internal APIs. Outline what success looks like: is this about compliance, red teaming, or finding exploitable misconfigs?
Never test in production. Create a dedicated AWS environment just for testing. Set up isolated networks, hardened instances, IAM roles, and security groups to simulate your actual cloud stack without risking disruption.
Start with reconnaissance. Use tools like AWS CLI, Prowler, or manual checks to find accessible services, open ports, over-permissive roles, and weak configurations. Pay close attention to IAM roles, public endpoints, and unprotected S3 buckets.
This is where you test what you’ve mapped. Scan for known vulnerabilities, exploit unsafe policies, and simulate real-world attacks. The goal isn’t just to find bugs—it’s to uncover real risk in how your cloud is set up.
Start small, test wide, and always document what you find.
These are the core techniques used to uncover misconfigurations, privilege escalations, and exposed assets in AWS environments. Each step gets you closer to understanding how secure—or insecure—your cloud setup really is.
The key techniques include:
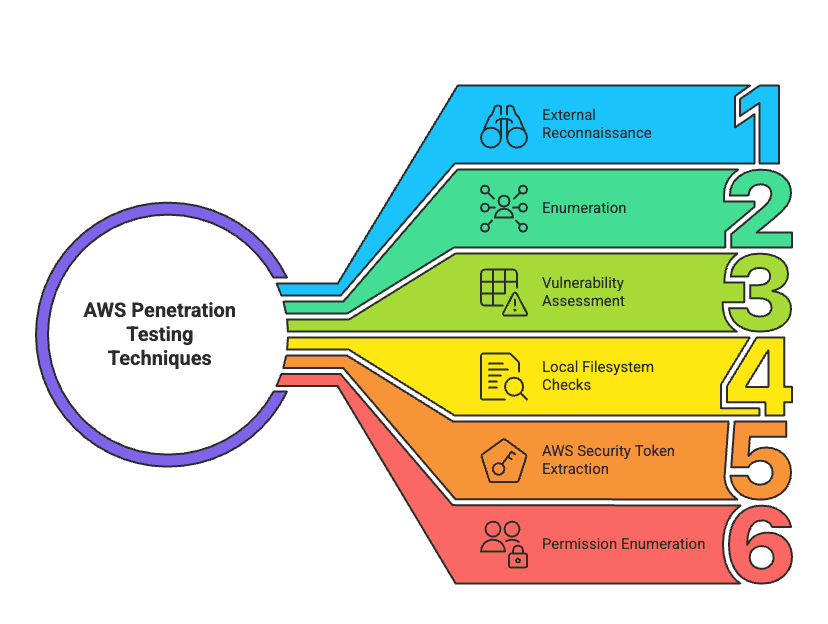
AWS Penetration Testing Techniques
Let’s break down each technique to understand how it fits into a practical AWS pentest—and how it reveals the weak points attackers are counting on.
Start by gathering public information about your AWS environment. This phase doesn’t require credentials but can reveal exposed resources.
Dig deeper into the account’s configuration by listing policies, users, roles, and network controls.
aws iam list-policies
aws iam get-policy --policy-arn arn:aws:iam::aws:policy/AdministratorAccess
aws iam list-attached-user-policies --user-name <username>
aws iam list-roles
aws ec2 describe-security-groups
aws ec2 describe-network-acls
aws ec2 describe-subnets
Scan common services for insecure configurations.
`aws s3api list-buckets --query "Buckets[].Name"`
for bucket in $(aws s3api list-buckets --query "Buckets[].Name" --output text); do
echo "Checking permissions for bucket: $bucket"
aws s3api get-bucket-acl --bucket $bucket
aws s3api get-bucket-policy --bucket $bucket
done
aws lambda list-functions
for func in $(aws lambda list-functions --query "Functions[].FunctionName" --output text); do
echo "Checking code for Lambda function: $func"
aws lambda get-function --function-name $func
done
aws rds describe-db-instances
for db in $(aws rds describe-db-instances --query "DBInstances[].DBInstanceIdentifier" --output text); do
aws rds describe-db-instances --db-instance-identifier $db
done
If you gain access to an EC2 instance or similar service, inspect the local file system.
- Look for config files, hardcoded secrets, or sensitive logs.
- Identify misconfigurations that allow privilege escalation.
- Attempt lateral movement using discovered ports, services, or SSH keys.
Check for AWS credentials and metadata:
# Accessing AWS Metadata Service
TOKEN=$(curl -s -X PUT "http://169.254.169.254/latest/api/token" -H "X-aws-ec2-metadata-token-ttl-seconds: 21600")
curl -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/
Temporary tokens (from EC2 IAM roles) can be used to access AWS resources. If found, extract them from the metadata service:
# Retrieving IAM Role Credentials
TOKEN=$(curl -s -X PUT "http://169.254.169.254/latest/api/token" -H "X-aws-ec2-metadata-token-ttl-seconds: 21600")
IAM_ROLE=$(curl -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/iam/security-credentials/)
curl -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/iam/security-credentials/$IAM_ROLE
Once you’ve obtained AWS credentials, enumerate what actions are allowed.
aws sts get-caller-identity
aws iam list-attached-role-policies --role-name <ROLE_NAME>
aws iam list-policy-versions --policy-arn <POLICY_ARN>
These techniques, when used responsibly, help uncover serious risks long before attackers do. Always test within scope and with proper authorization.
Using the right tools can make or break an AWS pentest. Cloud environments are complex—riddled with policies, ephemeral resources, and identity boundaries. The best tools help you cut through the noise, uncover misconfigurations, test access boundaries, and simulate real-world attacks without causing damage.
The core AWS penetration testing tools are:
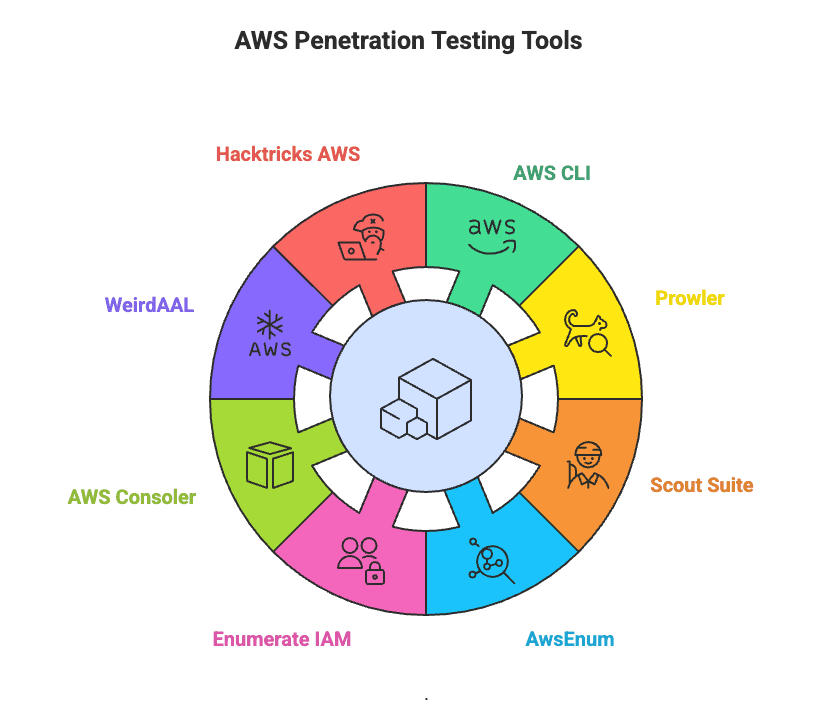
AWS Penetration Testing Tools
Let’s break down what each tool brings to the table and how it fits into a successful AWS penetration test.
The foundation of everything. The AWS Command Line Interface lets you query services, inspect metadata, manage permissions, and run audits directly from the terminal. Most pentesting tools are wrappers around it—so mastering the CLI is essential.
Prowler is an open-source tool that performs security and compliance checks against AWS environments. It aligns with benchmarks like CIS, GDPR, HIPAA, and PCI-DSS—making it useful for both pentesting and audit readiness.
Scout Suite is a powerful multi-cloud auditing tool that generates detailed, visual reports of misconfigurations, IAM exposures, and network weaknesses. Great for reporting findings to non-technical stakeholders.
AwsEnum and Enumerate IAM are specialized reconnaissance tools designed to identify hidden IAM privileges, misconfigured roles, and privilege escalation paths that may otherwise slip through traditional audits.
Transforms CLI access keys into AWS Console sessions. Ideal for teams that want GUI access without sharing passwords or long-term credentials.
WeirdAAL is a post-exploitation framework that demonstrates what an attacker can do with compromised AWS credentials—making it ideal for red teams simulating real-world cloud breaches.
Hacktricks AWS serves as a curated, continuously updated knowledge base packed with AWS-specific attack vectors, exploitation scripts, and escalation paths used in actual compromises across the cloud landscape.
Pro Tip: Start with AWS CLI mastery. Most of these tools build on it—so if you understand how it works, the rest comes naturally.
AWS penetration testing isn’t just a checkbox—it’s a critical, ongoing effort to validate your cloud defenses against real-world threats.
Whether you're running a lean startup or managing a sprawling multi-account enterprise, misconfigurations, exposed IAM policies, and overlooked permissions can open dangerous gaps. Pentesting helps you catch these blind spots before attackers do.
But cloud testing comes with its own rules and nuances. Unlike traditional environments, AWS operates under a shared responsibility model—and breaking AWS’s testing policies could get your account flagged or throttled. That’s why structured, compliant testing matters. From defining scope and building a safe test environment to leveraging the right tools and enumeration techniques, every step must be intentional and accountable.
Tools like Prowler, Scout Suite, and the AWS CLI are powerful—but only when paired with a deep understanding of IAM, metadata services, and privilege escalation paths.
At the end of the day, penetration testing in AWS is about building cloud environments that don’t just look secure—but are secure. It’s about knowing your weak spots, testing them safely, and staying one step ahead of whoever’s coming after your cloud.
Want help testing your AWS stack—without the noise, false positives, or compliance headaches? Get clarity, not checklists. Talk to our team to get started.

Head of Security testing