0%
Security frameworks aren’t fancy tools you can buy—they’re your playbook. Think of them as clear rules, best practices, and step-by-step processes that tell you how to protect data, manage risks, and stay compliant.
Most companies get it wrong: they treat frameworks like a one-and-done checklist. Set it up once, mark compliance “done,” then forget about it. That’s the fastest way to get breached, fined, or lose customer trust.
Done right, frameworks become your backbone. They create consistency across teams, give IT and executives a shared language, and improve your overall security posture. They also help you stay ahead of threats, avoid regulatory penalties, and prove to leadership that your security efforts actually work.
Understanding what a security framework is lays the foundation for choosing the right one. Let’s break down what a framework really does and why it matters for your organization.
A security framework is a structured playbook of guidelines and best practices that helps organizations protect data, manage risks, and stay compliant—examples include the common criteria security framework, which provides internationally recognized standards for evaluating information security. It turns scattered security efforts into a coordinated program, making it easier for teams to act decisively and keep systems—and business—secure.
Why it matters:
Consistency: Security measures are applied uniformly across the organization, reducing gaps.
Clear communication: Teams, executives, and auditors share a common language around risk.
Proactive defense: Frameworks enable organizations to prevent threats rather than just reacting to them.
Compliance: Helps meet regulations like HIPAA, PCI DSS, and GDPR.
Scalability: Adapts to organizations of all sizes, from small businesses to global enterprises.
In short, security frameworks aren’t optional—they’re essential for resilient and effective cybersecurity.
Security frameworks aren’t optional—they’re your roadmap for protecting data, managing risk, and staying compliant. Knowing the right frameworks keeps your business secure and trusted.
These 11 must-know common cybersecurity frameworks provide structured guidance to keep organizations secure and compliant.
Here are the essential frameworks every organization should know:
Essential Common Security Frameworks
Let’s dive into each of these frameworks to understand what they cover, how they work, and why your organization should care.
Think SOC 2 is just another checkbox? Think again. Created by the AICPA, SOC 2 separates serious service providers from the rest. It focuses on protecting customer data and proving your security is real—not just talk.
SOC 2 revolves around five Trust Services Criteria (TSC):
You pick the optional criteria based on your business needs. Security is non-negotiable, ensuring systems and data are protected with firewalls, MFA, and intrusion detection.
Roadmap: select TSC, build controls, remediate gaps, get audited, receive attestation report.
Tech & SaaS, cloud providers, financial services, and healthcare tech can’t skip SOC 2. In North America, it’s often the price of entry for contracts and a signal to customers that your security is serious.
ISO 27001 isn’t just another standard—it’s the global benchmark for managing information security. Companies in over 150 countries rely on it to protect their most critical data and prove they follow internationally recognized best practices.
ISO 27001 is built around the CIA triad:
Instead of mandating tools, it guides organizations to assess risks and implement the right controls, scaling from small startups to multinational enterprises.
Certification is valid for three years, with annual surveillance audits and a full recertification audit at the end.
ISO 27001 is ideal for any organization handling sensitive data globally. Certification demonstrates to leadership and customers that security is taken seriously and aligns with international best practices.
The NIST Cybersecurity Framework is a flexible playbook for managing cyber risks, originally created to protect critical infrastructure. Today, it’s widely adopted across industries because it’s voluntary, adaptable, and practical for organizations of any size.
NIST CSF is structured around five core functions:
Version 2.0 adds a sixth function, Govern, emphasizing leadership involvement in cybersecurity.
NIST CSF is voluntary and doesn’t require formal certification. Implementation involves:
NIST CSF works for startups, enterprises, and public agencies alike. It provides a clear, adaptable roadmap for improving cybersecurity, aligning teams, and making informed risk-based decisions.
HIPAA isn’t optional—if you handle electronic protected health information (ePHI), compliance is mandatory. The Security Rule ensures healthcare organizations protect patient data while scaling requirements to fit their size and risk.
HIPAA Security Rule mandates three types of safeguards:
The framework scales with your organization, considering size, infrastructure, costs, and ePHI risk levels.
HIPAA doesn’t have a formal certification. Compliance is enforced by the Office for Civil Rights (OCR) via:
HIPAA is essential for healthcare providers, insurers, and tech handling ePHI. Following the Security Rule protects patient data, reduces breach risk, and ensures legal compliance.
If your business accepts credit cards, PCI DSS isn’t optional—it’s mandatory. Created by major card brands, this framework protects payment data wherever it’s stored, processed, or transmitted.
PCI DSS organizes security into 12 requirements under six control objectives:
These requirements ensure consistent protection of payment systems across organizations of all sizes.
Compliance level depends on transaction volume:
Costs vary based on size, complexity, and assessor fees.
PCI DSS is crucial for any business handling cardholder data, especially e-commerce and retail. Compliance prevents data breaches and costly fines, ensuring trust with customers and payment partners.
The General Data Protection Regulation (GDPR) revolutionized data privacy worldwide. Any organization handling EU residents’ personal data must comply, no matter where it’s based.
GDPR sets out seven non-negotiable principles:
High-risk processing may require a Data Protection Impact Assessment (DPIA).
GDPR compliance is enforced by Data Protection Authorities (DPAs):
There’s no formal certification; compliance is continuous and monitored.
Any company handling EU personal data must follow GDPR. Compliance reduces breach risks, avoids massive fines, and builds trust with customers globally.
HITRUST CSF is designed to simplify compliance while delivering measurable security results. It integrates multiple standards into a single framework, helping organizations manage risk efficiently and avoid breaches.
HITRUST combines over 60 regulations and standards, including:
Controls are spread across 19 domains with three implementation levels, allowing organizations to tailor security based on actual risk.
The certification journey typically takes 1–2 years:
R2 assessments require 62% across domains; I1 assessments require 83%. Certifications last two years, with an interim assessment at 12 months.
HITRUST is ideal for healthcare organizations juggling multiple standards. One framework covers HIPAA, NIST, ISO, and more, streamlining compliance and strengthening overall security posture.
COBIT focuses on bridging the gap between IT operations and business objectives. It provides a structured approach to governance, ensuring IT aligns with organizational goals and regulatory requirements.
COBIT is built on five components:
The latest version, COBIT 2019, organizes processes into five domains: Plan & Organize, Acquire & Implement, Deliver & Support, Monitor & Evaluate, and Manage & Assess.
COBIT itself doesn’t require certification, but implementing its processes helps meet audit requirements and supports frameworks like SOX, ISO 27001, and ITIL. Organizations typically assess current maturity, implement controls, and monitor performance.
COBIT is ideal for enterprises seeking IT governance clarity. It helps bridge IT and executive communication, supports compliance, and ensures IT investments drive business value.
NIST SP 800-53 is a comprehensive framework for securing federal information systems. It provides a detailed set of controls to protect operations, assets, and personnel from cyber threats.
The framework organizes over 1,000 controls into 20 families, including:
Organizations often map these controls to the common control NIST catalog to ensure consistent and standardized risk management. Control selection depends on system criticality: low-impact systems may require around 150 controls, while high-impact systems could need nearly 400. This approach aligns with the nist common criteria, ensuring that all controls meet federal standards and follow best practices.
SP 800-53 is used to achieve FISMA compliance. Implementation involves:
There’s no formal “certification,” but proper implementation is mandatory for federal systems.
Federal agencies and contractors use NIST 800-53 to secure systems and comply with FISMA. It ensures a standardized, risk-based approach to cybersecurity, protecting critical data and operations.
CMMC 2.0 is the Department of Defense’s cybersecurity standard for contractors. It ensures sensitive government data is protected across the defense supply chain.
CMMC 2.0 has three levels:
Level 1 (Foundational): Protect Federal Contract Information (FCI) with 17 basic practices; annual self-assessment
Level 2 (Advanced): Aligns with 110 NIST SP 800-171 controls; protects Controlled Unclassified Information (CUI); self or third-party assessment allowed
Level 3 (Expert): Adds 24 NIST SP 800-172 practices; government-led assessment; defends against Advanced Persistent Threats (APTs)
The framework ensures contractors meet the right security posture for their contract level.
Certification depends on the level:
Contractors must complete gap assessments, remediate issues, and get verified before handling sensitive data.
Any contractor working with the DoD must comply. CMMC 2.0 secures federal data, reduces supply chain risk, and ensures eligibility for defense contracts.
The Federal Information Security Modernization Act (FISMA) sets mandatory cybersecurity requirements for U.S. federal agencies and contractors. It ensures government systems and data are protected against evolving threats.
FISMA compliance revolves around five core requirements:
Even “low-impact” systems require over 100 controls, making thorough implementation essential.
FISMA compliance involves:
There’s no formal certificate; compliance is enforced via audits and federal oversight.
Federal agencies and contractors must comply. FISMA treats cybersecurity as a core business requirement, protecting sensitive government data and ensuring operational resilience.
These 11 frameworks guide organizations to stay secure, manage risk, and meet compliance. They’re not just checkboxes—they’re the backbone of strong cybersecurity.
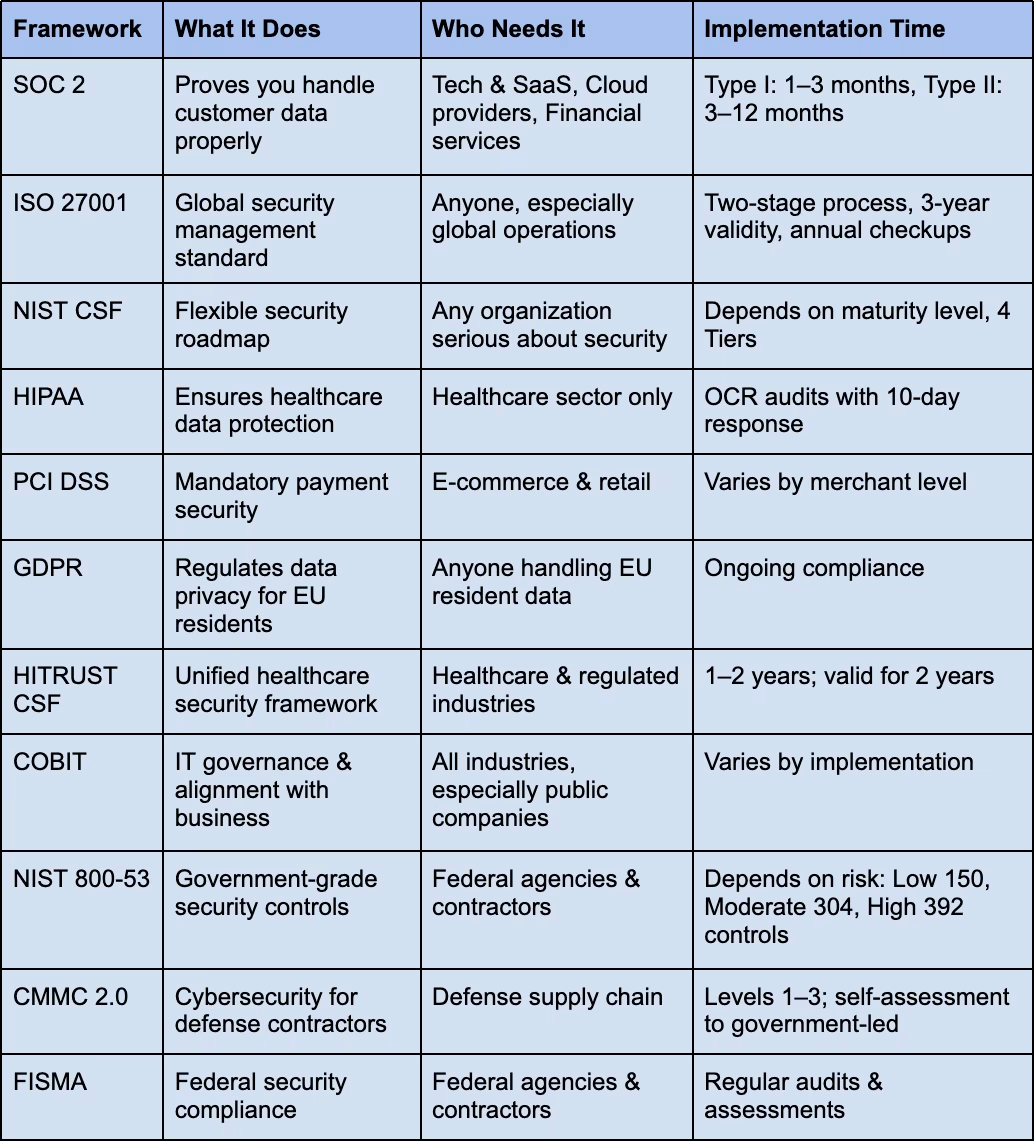
Essential Common Security Frameworks
Use this table to see which frameworks fit your industry, who needs them, and how long they take. Pick, implement, and stay secure.
Selecting the right security framework is simpler than it seems—focus on three key questions:
1. Your industry – Healthcare? HIPAA is mandatory; HITRUST adds credibility. E-commerce? PCI DSS is essential. Government contractors? CMMC 2.0 or FISMA. SaaS? SOC 2 is often table stakes.
2. Customer expectations – Enterprise clients often expect ISO 27001. Startups may ask for SOC 2. Vendor questionnaires reveal what matters most.
3. Your capacity – Some frameworks are major undertakings. HITRUST can take 1–2 years; ISO 27001 requires serious commitment. Start manageable, then scale.
The common mistake? Treating frameworks as one-time checklists. They need continuous updates, monitoring, and improvement. Layer frameworks strategically if necessary.
Pick one that fits your immediate needs, implement it thoroughly, and expand gradually. Doing it right costs far less than a breach, regulatory fines, or lost customer trust—your framework is your roadmap to real security.
Build trust and prevent breaches with UprootSecurity — making GRC the key to good security. → Book a demo today

Senior Security Consultant