0%
Think HIPAA is the same boring compliance checklist from 1996? Think again.
The Health Insurance Portability and Accountability Act (HIPAA) just got its biggest wake-up call in decades—and this time, it’s not about paperwork. What started as a law to help employees keep their health insurance between jobs has evolved into one of the most critical cybersecurity frameworks in the United States. HIPAA now stands as the frontline defense protecting hospitals, clinics, and digital health startups from an unrelenting wave of cyberattacks.
In December 2024, the Department of Health and Human Services (HHS) introduced the most sweeping HIPAA Security Rule update in more than 20 years. The reason is impossible to ignore: healthcare is under siege. Between 2018 and 2023, large-scale breaches jumped 102%, and over 167 million individuals were impacted in 2023 alone—the worst year ever for patient data exposure.
The message is clear: HIPAA isn’t a suggestion anymore. It’s a mandate. Compliance is now cybersecurity in action.
To understand HIPAA in 2025, you have to see it for what it’s become—a full-fledged cybersecurity law disguised as a healthcare regulation.
The act still protects Protected Health Information (PHI), but its mission now extends far beyond patient privacy. It’s about resilience, accountability, and defense in an era where healthcare data is both currency and target. Hospitals, clinics, and health tech vendors aren’t just expected to secure data—they’re expected to demonstrate how.
The full meaning of HIPAA today lies in its expanded scope. It bridges compliance and cybersecurity, demanding continuous risk assessments, employee training, encryption, and documented safeguards for every system that touches patient information. It enforces not just protection but proof.
This evolution redefines what compliance means in modern healthcare. It’s no longer about paperwork or annual audits—it’s about embedding security into daily operations. HIPAA isn’t a policy relic anymore—it’s the operating system that powers trust, protection, and digital resilience across the healthcare ecosystem.
HIPAA might have started as an insurance portability law—but in 2025, it’s the rulebook for how healthcare protects its most valuable asset: patient data. Understanding HIPAA means understanding how privacy, security, and accountability intersect in modern healthcare.
HIPAA stands for the Health Insurance Portability and Accountability Act of 1996, signed into law on August 21, 1996.
It began as a simple fix for people changing jobs and losing health insurance. But like most federal laws, it expanded—fast. Today, HIPAA includes five titles, but Title II—the Administrative Simplification provisions—does the heavy lifting. It directed the Department of Health and Human Services (HHS) to create national standards for electronic health information, privacy, and security.
The meaning of HIPAA now goes far beyond portability. It does four big things:
For healthcare providers, HIPAA defines strict rules on when and how data can be shared, gives patients access to their own medical records, and enforces technical safeguards for electronic Protected Health Information (ePHI).
So if you’re wondering how to truly “define HIPAA law”—it’s a legislative mashup. It weaves together the Public Health Service Act, the Employee Retirement Income Security Act (ERISA), and the HITECH Act, which turbocharged HIPAA’s data security and breach notification rules.
HIPAA doesn’t apply to everyone—it applies to “covered entities” and their “business associates.”
Covered entities include:
Business associates are third parties—billing vendors, IT providers, legal firms, transcription services—who access or manage PHI. They must sign Business Associate Agreements (BAAs) confirming compliance.
But liability doesn’t stop there. Business associates are now directly accountable for safeguarding PHI—and they must ensure their subcontractors follow suit. It’s a compliance chain reaction, and every link matters.
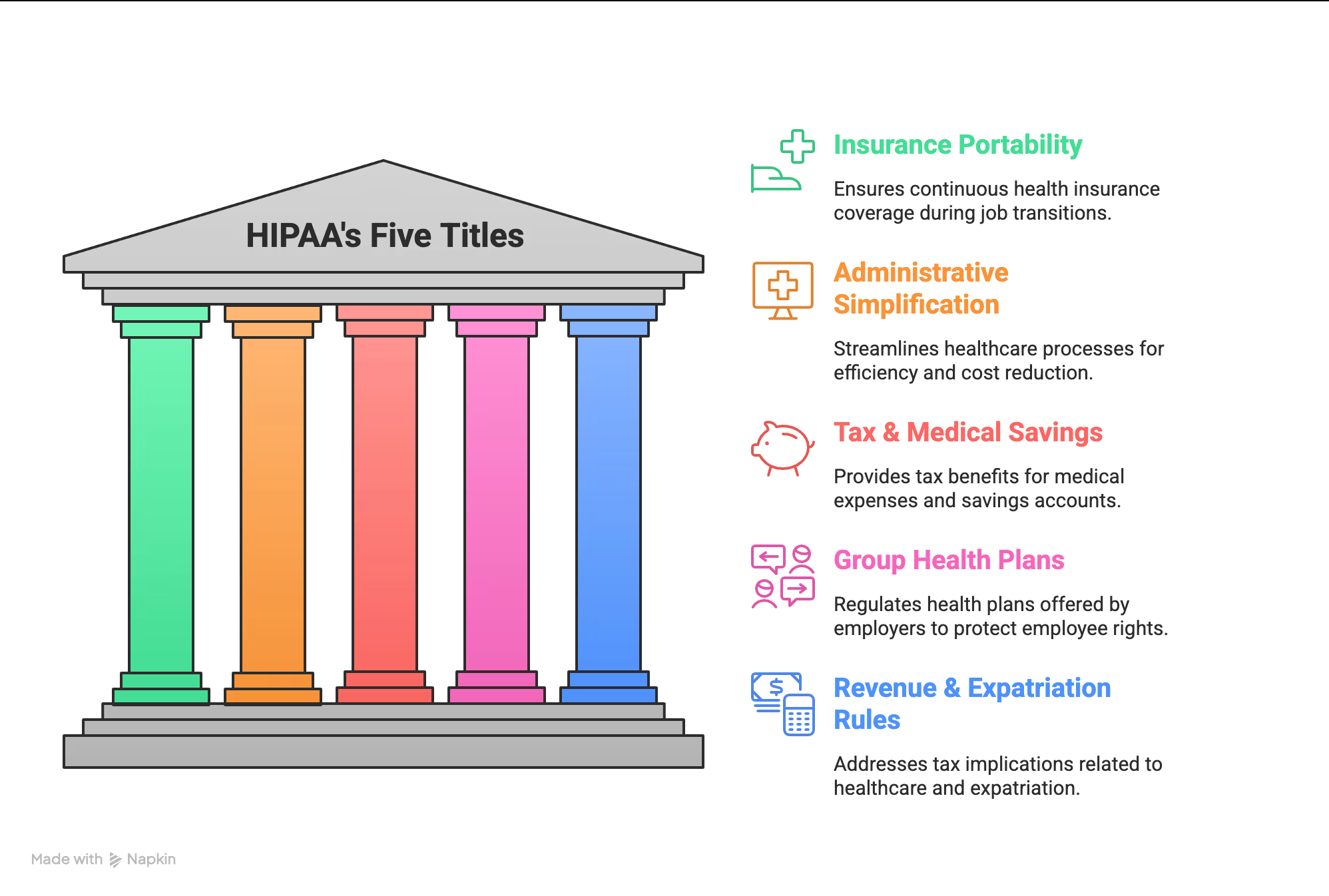
Here’s what most healthcare providers miss: HIPAA isn’t one rule—it’s five. Passed in 1996, the Health Insurance Portability and Accountability Act (HIPAA), also called the Kennedy-Kassebaum Act, reshaped how healthcare information is managed, protected, and exchanged across the U.S.
Before HIPAA, switching jobs often meant losing coverage or facing exclusions for preexisting conditions. Title I fixed that. It:
Essentially, Title I updated federal laws like ERISA and the Public Health Service Act to protect workers’ insurance continuity.
Title II is the operational core of HIPAA—the part healthcare providers work with daily. It established:
It also introduced the Transactions and Code Sets Rule, Unique Identifiers Rule, and Enforcement Rule, creating the foundation for modern healthcare data protection and standardized digital communication.
These final HIPAA titles cover the financial and administrative aspects of healthcare:
Title III: Establishes tax deductions for medical insurance premiums and sets rules for Medical Savings Accounts (MSAs).
Title IV: Expands protections for individuals with preexisting conditions and updates continuation coverage (COBRA) requirements.
Title V: Regulates company-owned life insurance policies and defines tax rules for individuals who renounce U.S. citizenship.
Together, these five titles form HIPAA’s full legal framework—covering everything from patient privacy to data security to tax treatment.
HIPAA's Five Titles
Protected Health Information (PHI) sits at the center of HIPAA’s privacy and security rules. It’s not just medical charts or hospital files—it’s any health-related data that can identify a person. From lab results to phone numbers linked to patient care, PHI covers it all. If information connects a person’s identity with their health, it falls under HIPAA’s protection.
The definition of protected health information under HIPAA includes any individually identifiable health data created, received, maintained, or transmitted by a covered entity or business associate. For something to qualify as PHI, it must:
The key idea? PHI directly links personal identity to health details. Anonymous or de-identified data doesn’t count.
PHI extends far beyond medical charts. It includes:
Even a single baby photo sent to a pediatrician qualifies as PHI. So does a note about someone’s LGBTQ status or emotional support animal—if tied to their medical record.
The Department of Health and Human Services (HHS) lists 18 identifiers that make health data “identifiable.” Examples include:
Not PHI: education records under FERPA, employer-held data, or information about individuals deceased for over 50 years.
Here’s the truth. The HIPAA Privacy and Security Rules aren’t just red tape—they’re your survival guide for protecting patient data without landing in legal hot water.
The Privacy Rule sets national standards for how medical records and health data are handled. Think of it as your guide for what can be shared—and when.
You must share information:
You can share without permission for:
You need written consent for:
And always follow the minimum necessary rule—share only what’s essential. No one needs a 20-page history when a test result will do.
If Privacy is the “what,” Security is the “how.” It covers electronic protected health information (ePHI) and ensures three things: confidentiality, integrity, and availability.
Compliance means conducting risk analyses, patching vulnerabilities, and maintaining safeguards—administrative, physical, and technical. These scale to your organization’s size.
Whether you’re a small clinic or a hospital network, the bar stays high.
The 2013 Omnibus Rule raised the stakes. Business associates—like billing firms or IT vendors—are now directly accountable.
If a breach happens, you must:
Miss a deadline? Expect fines—Presence Health paid $475,000 for delayed notices.
HIPAA empowers patients to:
You have 30 days to respond (soon it may drop to 15).
Once you internalize these rules, HIPAA stops feeling like compliance—it becomes culture.
Here’s the deal. Knowing HIPAA rules and actually living them? Two very different things. Real-world compliance isn’t about ticking boxes on a checklist—it’s about building systems that hold up when a breach hits at 2 AM.
HIPAA compliance means following a set of interlocking regulations to protect patient data. In practice, that looks like:
The best organizations go beyond compliance—they build a culture where data protection becomes instinct. Because the truth is, HIPAA isn’t a one-time task. It’s a moving target that evolves with every new threat.
Let’s clear the air: there’s no official HIPAA certification. Those framed certificates from vendors? Marketing, not proof. What is mandatory is workforce training.
The Privacy and Security Rules require you to train every employee—before they handle patient data, whenever policies change, and at least once a year. Think of training not as compliance theater, but as your frontline defense.
Every organization needs a HIPAA Security Officer. It’s not a nice-to-have—it’s federal law (45 CFR 164.308). This person leads security awareness programs, runs risk assessments, manages incidents, and coordinates cleanup.
A risk assessment isn’t paperwork—it’s your map. It shows where patient data lives, what could go wrong, and how to fix it before it explodes into a breach.
HIPAA’s three pillars of protection work like this:
One gap in these safeguards—and you’re not just noncompliant. You’re exposed.
HIPAA compliance isn’t about perfection. It’s about persistence.
Here’s the truth about HIPAA violations: they hurt—financially, legally, and reputationally. Since 2003, the Office for Civil Rights (OCR) has handled more than 374,000 HIPAA complaints, leading to 152 settlements totaling over $144.8 million. That’s not just paperwork—that’s accountability with a heavy price tag.
HIPAA’s penalty structure doesn’t mess around.
Civil penalties (per violation, annual cap $2,134,831):
Criminal penalties (Department of Justice):
Most HIPAA violations don’t stem from hackers—they come from everyday mistakes. Weak data controls, untrained staff, and carelessness often cause the biggest damage. Common causes include:
UCLA Health System learned this lesson the hard way, paying $865,000 for failing to restrict access to patient records.
When George Clooney was hospitalized after a motorcycle crash, 27 workers were suspended for snooping on his medical records. Britney Spears’ psychiatric stay at UCLA led to 13 staff members being fired for unauthorized access. Octomom Nadya Suleman’s case resulted in 21 employees being caught illegally viewing her data, costing the hospital $250,000. Cardionet paid $2.5 million after a stolen laptop compromised 1,391 patients. And a dentist who revealed PHI while replying to a Yelp review? A $50,000 fine—and public embarrassment.
HIPAA violations don’t just cost money—they destroy trust. In 2025, compliance isn’t optional. It’s survival.
Let’s be honest—HIPAA compliance isn’t glamorous. Nobody claps for risk assessments. Nobody celebrates encryption upgrades. But here’s what actually matters: patient trust.
When someone shares their deepest health fears with you, they’re not thinking about compliance checklists or security frameworks. They’re trusting you with their most vulnerable truths. That trust deserves protection—not because the law says so, but because it’s the right thing to do.
HIPAA compliance will never be perfect. You’ll have gaps. People will slip up. Tech will crash when you least expect it. That’s not failure—that’s healthcare. The real win is showing up every day to do it better.
Start small. One vulnerability assessment, not twelve. Train people like humans, not policy machines. Fix what’s broken. Document what’s real. Stay curious about what’s next.
Yes, penalties can reach $2.1 million a year. But fear isn’t the motivator—trust is. Because HIPAA isn’t about paperwork. It’s about protecting the people who trust you to care for them.
Take control of compliance, reduce risk, and build trust with UprootSecurity — where GRC becomes the bridge between checklists and real breach prevention. → Book a demo today

Senior Security Consultant