Ever wondered why companies with 75+ security tools still get hacked? Here’s the uncomfortable truth: 2025’s security landscape is built on illusions. Organizations keep piling on shiny tools, expanding their stacks to an average of 75 solutions. Blinking dashboards everywhere—but real security? Not so much.
Verizon’s latest report shows that 67% of U.S. enterprises were breached in the past 24 months, and vulnerability exploitation is up 34% year-over-year. Why? Tools can’t tell you if your security actually works. They only tell you they’re running.
Meanwhile, teams managing 75+ solutions drown in 2,000 alerts per week—double what smaller stacks generate. Those with 100+ tools face over 3,000 weekly alerts. That’s not protection—it’s noise.
Even companies with fewer than 50 security tools aren’t safe: they saw a shocking 93% breach rate. Your security stack can look impressive, but without real-world testing, it’s just a fancy alarm system nobody’s tried.
Professional penetration testing changes the game. These aren’t automated scans. These are humans thinking like attackers, finding the gaps your tools completely miss.
Why Penetration Testing Services Matter in 2025
Professional penetration testing services are the reality check every organization desperately needs. Unlike automated scans, skilled pentesters chain together tiny weaknesses, map attacker paths, and expose business process gaps that dashboards can’t detect.
The stakes are enormous. Data breaches now cost $4.45 million globally and $10.22 million in the U.S. A single $20,000 penetration test can prevent a major breach, delivering an ROI of 200x. That’s proof that investing in human-led testing isn’t optional—it’s essential.
From basic penetration testing for compliance to advanced testing that validates real-world defenses, these services uncover what tools cannot. Web applications, APIs, cloud environments like AWS and Azure, even mobile apps through Android penetration testing—pentesters see it all.
Annual penetration testing has evolved beyond a checkbox. It’s the only way to verify that controls work in practice, not just in theory. When you test like an attacker, you see the truth about your security posture. And in 2025, knowing the truth isn’t just valuable—it’s survival.
Core Penetration Testing Services Explained
The pentesting world got complicated fast. You’ve got basic scans, advanced testing, API checks, mobile app pen testing, wireless assessments… and most companies have no clue which one they actually need
Basic Penetration Testing vs Advanced Penetration Testing
Basic penetration testing is like a health checkup with a checklist. Automated tools scan for known vulnerabilities using predefined signatures. Quick. Clean. Predictable.
But here’s what basic testing misses: context-specific vulnerabilities that require human intuition.
Advanced penetration testing goes deeper:
- Creates custom exploits for your environment
- Focuses on business logic flaws
- Emphasizes post-exploitation to show real-world impact
Advanced testers don’t just find the door—they walk through it, explore privilege escalation paths, set up covert channels, and test whether you’d notice if someone was stealing your data.
Think of it this way: Basic testing tells you the lock is broken. Advanced testing shows exactly how a thief would rob you blind.
Application Penetration Testing Services for Web and Mobile Apps
Web and mobile apps are where the action happens.
Web testing checks:
- Security flaws in source code and databases
- Authentication and session issues
- Data validation and integrity gaps
Mobile app penetration testing covers:
- Malware distribution through apps
- Phishing targeting BYOD devices
- WiFi network vulnerabilities and MDM violations
Your apps are talking to the world. Are they saying the right things?
API Pentesting for Modern Microservices
APIs power modern apps—and often break them.
Why it’s critical:
- Most orgs can’t list all their APIs
- APIs handle sensitive data over the public internet
- Microservices create many potential security boundaries
Key vulnerabilities: weak authentication, code injection, rate-limiting gaps, and data leaks.
Proper testing requires understanding API specs to craft precise test requests. APIs are like whispering through your windows while thinking no one hears.
Wireless and Physical Security Testing
Wireless testing checks:
- Network encryption weaknesses
- Bluetooth and RFID/NFC protocols
Physical security testing covers:
- Tailgating and badge cloning
- Lock-picking and badge reader manipulation
- Employee social engineering resistance
Digital security means nothing if someone can just walk through the front door.
Social Engineering and Human Risk Assessment
Humans are usually the weakest link. Main attacks include:
- Phishing: Emails to steal info
- Vishing: Phone-based phishing
- Impersonation: Pretending to be someone trustworthy
- USB drops: Malicious devices left around
Over 85% of cyberattacks in 2024 leveraged social engineering. Your employees want to help. Attackers know this. And they use it against you.
The question isn’t whether you need penetration testing. It’s which combination of these services actually protects your organization.
Practical Penetration Testing Workflow — From Recon to Reporting
Behind every effective penetration test is a workflow that mirrors exactly how real attackers operate. Scary fact: organizations take an average of 212 days to detect a breach—and another 75 days to contain it. That’s why having a systematic, step-by-step workflow isn’t just nice to have—it’s critical for understanding your true security posture.
These are the core steps a penetration tester typically follows:
- Intelligence Gathering and OSINT Techniques
- Threat Modeling and Asset Prioritization
- Vulnerability Analysis, Exploitation, and Post-Exploitation
- Reporting and Risk-Based Remediation
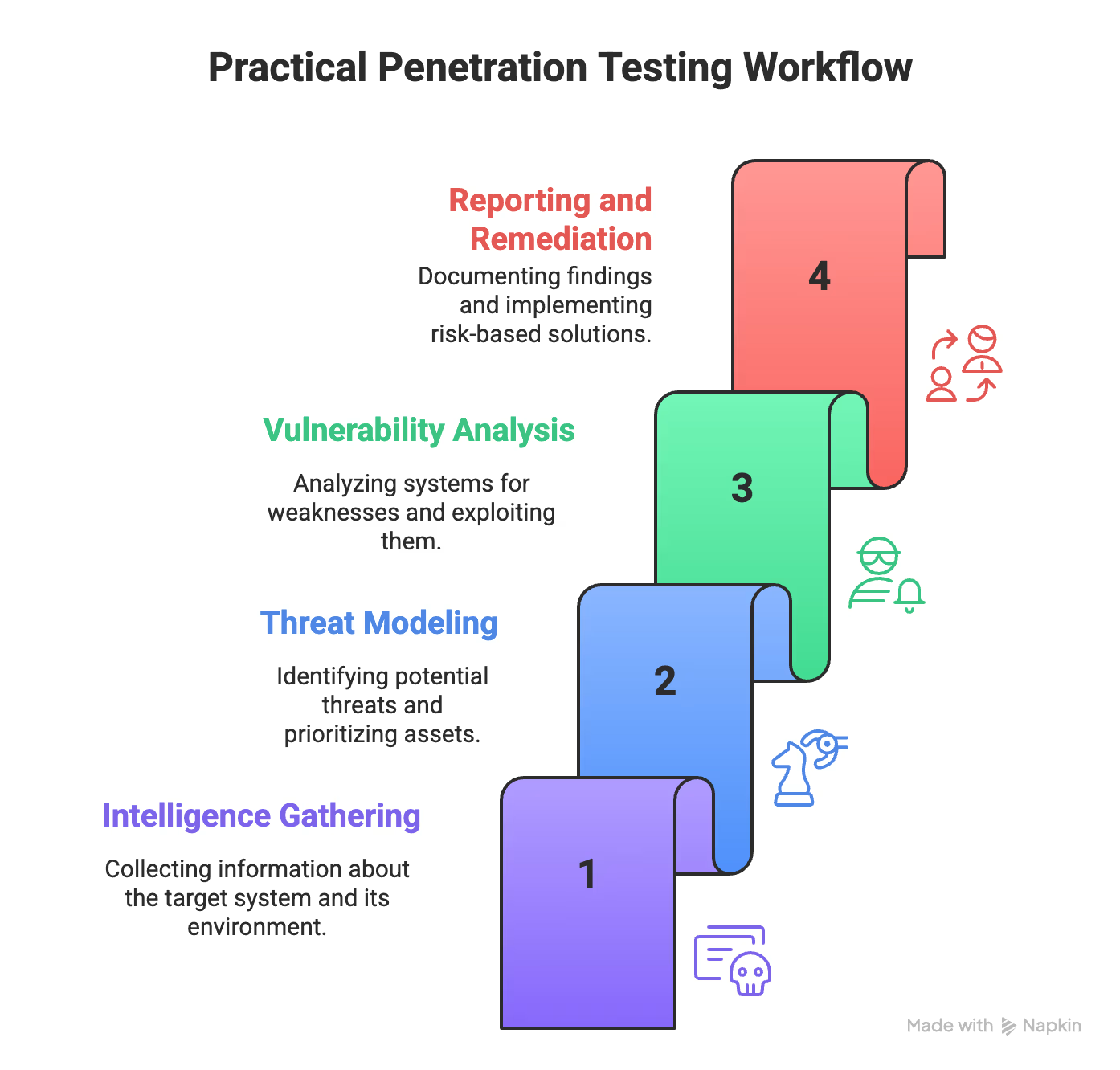
Practical Penetration Testing Workflow
This workflow provides a practical, hands-on approach for testers to uncover weaknesses and deliver actionable insights for organizations. Let’s dive into each step.
1. Intelligence Gathering and OSINT Techniques
Ethical hackers start the same way criminals do—by collecting publicly available information. OSINT (Open-Source Intelligence) is surprisingly effective at finding gaps without touching your systems.
Key tools include:
- Google Dorks: Advanced search operators uncover sensitive files hidden in plain sight
- Metagoofil: Finds emails and contact details exposed online
- Recon-ng: Automates data collection from multiple sources
- SpiderFoot: Maps your digital footprint across 100+ sources
Testers often discover attack vectors that client-provided asset lists completely miss.
2. Threat Modeling and Asset Prioritization
This phase answers one critical question: what’s most valuable to steal? Testers think like attackers, mapping attack surfaces, trust boundaries, and every possible entry point.
Frameworks like STRIDE provide structure without overcomplicating things. They help teams systematically consider Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege.
Prioritization is based on business impact, not just technical interest. The goal is to focus resources where they matter most, not chase low-risk vulnerabilities.
3. Vulnerability Analysis, Exploitation, and Post-Exploitation
After recon and modeling, testers move into active testing. Automated scans uncover known vulnerabilities, while manual analysis digs into logic flaws and hidden weaknesses.
Exploitation tests like SQL injection, cross-site scripting, and backdoors show how attackers could move through your systems. Post-exploitation demonstrates real impact—privilege escalation, lateral movement, and simulated data exfiltration. It’s not just about finding holes. It’s about understanding how a real attacker would operate.
4. Reporting and Risk-Based Remediation
The final report isn’t just a list of vulnerabilities. It includes:
- Critical asset importance: which parts of your business matter most
- Realistic exploitability: how easily vulnerabilities could be abused
- Business impact assessment: what damage an attacker could actually do
- Prioritized remediation guidance: where to spend your security budget first
This turns penetration testing from a technical exercise into a practical, strategic business tool. You get actionable insights, not just a checklist. The workflow ensures you know exactly how vulnerable you really are.
Choosing the Right Penetration Testing Approach
Choosing the wrong penetration testing approach is like bringing a knife to a gunfight. The right approach ensures your testing is efficient, effective, and aligned with your actual risk.
Black Box vs White Box vs Gray Box Testing
The information you provide testers changes everything:
-
Black Box Testing: Testers know nothing about your systems. They mimic external attackers, focusing on perimeter defenses. Quick and realistic, but may miss internal vulnerabilities.
-
White Box Testing: Full access to source code, architecture, and system details. Ideal for comprehensive assessments and insider threat detection. Thorough but resource-intensive.
-
Gray Box Testing: Limited info, usually credentials. Simulates advanced persistent threats while balancing depth and efficiency.
Most organizations find gray box testing delivers the best value. IBM’s 2025 report shows regular testing reduces breach impact by 38%, regardless of approach.
When to Use Android Penetration Testing
Mobile security isn’t optional. Android testing is essential if your apps:
- Handle sensitive banking, healthcare, or commercial data
- Include payment systems (e.g., Klarna 2021 breach)
- Connect to critical backend services
Past breaches like ParkMobile (21M users affected) show the stakes. Testing uncovers malware, insecure storage, and app-to-backend vulnerabilities before attackers exploit them.
Annual Penetration Testing for Compliance
Regulators are taking yearly testing seriously.
- HIPAA (2025 update): Requires annual penetration testing for healthcare entities
- GLBA: Mandates annual testing since 2023
- Bi-annual vulnerability scans and documented audits are often needed
Smart testing can cover multiple compliance frameworks simultaneously, saving time, reducing effort, and mitigating risk.
API Penetration Testing vs Web Application Testing
Web and API testing target different attack surfaces.
- Web apps: Focus on UI elements, authentication, and browser-based attacks
- APIs: Test backend logic, authentication, authorization, and endpoints not connected to UIs
With 90% of web apps exposing more risk via APIs than interfaces, specialized API testing has become essential.
Strategy for SMBs and Enterprise Environments
Testing strategies should match organizational size, risk, and budget.
- SMBs: Gray box testing is cost-effective, providing balanced insights
- Enterprises: Multi-layered approaches cover both internal and external systems
The key is building a strategy tailored to your organization’s actual risk—not copying what worked for someone else.
Automated vs Manual Penetration Testing Services
The debate isn’t about sides—it’s about scale versus complexity. Automation delivers speed and consistency, while manual testing adds intuition and context. Together, they give a full view of your security posture.
Automated Penetration Testing Tools and Use Cases
Automated testing is like a tireless security guard—never sleeps, never skips steps, never misses a beat. These tools excel at:
- Scanning large networks and thousands of endpoints efficiently
- Integrating into CI/CD pipelines for continuous security checks
- Running repeated vulnerability scans consistently without error
They quickly flag OWASP Top 10 risks, misconfigurations, and outdated components. Perfect for DevSecOps teams needing fast, repeatable feedback. But automation alone can’t think like an attacker—it misses context, logic flaws, and the creative paths human hackers exploit.
Combining Manual and Automated Testing for Better Coverage
The best approach blends both.
Step 1: Automated scanning sets the baseline, identifying obvious misconfigurations and exposed services.
Step 2: Human testers take over, validating results, discarding false positives, and probing for complex vulnerabilities that automation can’t detect.
Automation gives breadth. Humans give depth. Together, they deliver the complete picture of your real risk.
Limitations of Automated Pen Testing
Even the best tools have blind spots:
- Miss business logic and context-specific flaws
- Generate false positives that waste time
- Can’t chain vulnerabilities or anticipate attacker creativity
- Fail to identify zero-day exploits and evolving threats
Affordable Penetration Testing Strategies
Security testing doesn’t have to drain your budget:
- Startups: $5K–$10K for basic web or API testing
- Larger setups: $12K–$25K for layered assessments
A $10K test today beats a $4.45M breach tomorrow
Cloud & Infrastructure Penetration Testing Services
Moving to the cloud? Great choice. But here’s what nobody tells you: your cloud security is only as good as how you test it.
AWS Penetration Testing
AWS pentesting controls 32% of the cloud market. That’s a lot of S3 buckets, EC2 instances, and IAM policies to secure. Good news: AWS doesn’t make you jump through approval hoops anymore for most testing. Bad news: most companies still mess up their configurations.
Common issues we see:
- Exposed S3 buckets leaking customer data
- IAM policies granting excessive access
- Metadata service exploits nobody thought to check
Rule of thumb: don’t launch Denial-of-Service attacks. AWS isn’t cool with that.
Azure Penetration Testing
548,000 users got exposed through Azure misconfigurations. Microsoft secures the cloud, but everything inside—apps, workloads, data—is on you. Smart Azure pentesting covers storage, APIs, identity management, and infrastructure. Many companies focus on the wrong areas.
Internal and External Network Testing
- External: Simulates attacks from outside—web servers, firewalls, public apps.
- Internal: Assumes attackers are already inside; tests lateral movement.
- Hybrid/multi-cloud: On-prem and cloud resources combined, doubling attack surfaces.
Bottom line: cloud penetration testing ensures your security controls actually work across complex environments. Your infrastructure is intricate—your testing should match.
Evaluating a Penetration Testing Service Provider
Here's how to spot the real deal.
You’re about to spend $20,000+ on a pentest. Don’t get fooled by flashy marketing or empty promises. Most providers hide behind logos and buzzwords. Here’s what actually matters:
Look at the Certifications, Not the Company Logo
Look at individual certifications, not company credentials:
- OSCP/OSCP+: Proven ability to hack in real scenarios. Skills renewed every three years.
- CREST Registered Tester (CRT): Government-recognized, hands-on validated skills.
- CEH: Covers 500+ attack techniques; easier to get than OSCP but still useful.
Red flag: If they won’t share individual certifications, walk away. Certified testers find real vulnerabilities—not just run automated scans.
Demand to See Their Work Before You Pay
Ask for sample reports upfront. A proper report includes:
- Executive summary your CEO can understand
- Technical details with proof-of-concept examples
- Risk-based prioritization for what to fix first
During planning, they should document assets, credentials, and objectives. Vague scoping = vague results.
Support After the Test Separates Pros from Amateurs
Look for providers who offer:
- Post-test support for your technical team
- Free retesting of critical vulnerabilities
- Developer-friendly guidance
Reality check: ~10% of employees click phishing emails during testing. The best providers don’t just report issues—they help you fix them.
The bottom line: the right pentest provider finds problems and sticks around to help you solve them.
Building a Long-Term Penetration Testing Strategy
Penetration testing isn’t a “set it and forget it” task. It’s an ongoing commitment to understanding your real security posture. Most companies treat it like a yearly health check—then ignore their systems for the next 364 days. That’s a recipe for disaster.
The smartest organizations embed testing into development. Automated scans run continuously, catching obvious flaws, while certified human experts step in periodically to uncover complex vulnerabilities machines can’t spot. They track Mean Time to Detect (MTTD) and Mean Time to Remediate (MTTR), fix high-impact issues first, and test quarterly or annually based on risk. Add Attack Surface Management to see what attackers actually see.
The goal isn’t just to find vulnerabilities—it’s to build a culture where security testing becomes as natural as code reviews. Automated tools give breadth. Humans give depth. Together, they keep you ahead of the threats that are coming—because waiting 287 days to detect and contain your next breach? Nobody has time for that.
Continuous, hybrid testing isn’t optional. It’s how organizations survive, adapt, and thrive in 2025 and beyond.
Frequently Asked Questions

Robin Joseph
Senior Security Consultant
