0%
Ever notice how every breach headline feels worse than the last? Organizations now lose an average of $3.92 million when payment data is exposed — and 2024 turned PII, PHI, and PCI breaches into a full-blown epidemic.
AT&T’s March incident exposed data from 73 million customers. Dell followed with 49 million records leaked. Bank of America? A ransomware attack revealed Social Security numbers and credit card details for over 57,000 customers. Healthcare isn’t safe either — one-third of hospitals reported ransomware, phishing, or PHI theft last year.
This isn’t just an acronym quiz. Knowing the difference between PII, PHI, and PCI determines how you protect the data your business depends on. Yet 87% of organizations know it matters, and only 56% classify these data types correctly.
Understanding what PII, PHI, and PCI stand for isn’t optional. Let’s break down each category, decode compliance rules, and show how to keep your systems — and your customers — safe from the next breach.
PII stands for Personally Identifiable Information – basically any data that can point back to a specific person, either by itself or when you mix it with other info. The PII acronym gets thrown around a lot, but most businesses underestimate how broad it actually is.
Sounds simple, right? Nope. Here's where it gets tricky.
PII comes in two flavors, and most people only think about one:
Ever wondered how risky “harmless” identifiers can be? Just gender, ZIP code, and birth date can identify 87% of US citizens.
Businesses rely on PII, but one mistake can expose millions of records, wiping out years of trust in seconds.
Here's what can really hurt you if it gets out:
Then there's non-sensitive PII – names, phone numbers, ZIP codes. Seems harmless, right?
Wrong. Context changes everything.
Your name on a business card? No big deal. Your name on a clinic's HIV patient list? Now we're talking sensitive territory.
GDPR keeps it broad: "any information relating to an identified or identifiable natural person." They want you protecting everything – even political opinions and physical characteristics.
CCPA casts an even wider net covering:
Your business handles PII everywhere:
Here's the truth: most companies keep sensitive personal information in their files. Protecting it isn't just about compliance checkboxes – it's about staying in business.
Because without proper safeguards, PII becomes a weapon for fraud, identity theft, and financial disasters.
PHI stands for Protected Health Information — the most tightly controlled category of personal data in healthcare, regulated under the Health Insurance Portability and Accountability Act (HIPAA). It isn’t just data; it’s the backbone of patient trust and healthcare integrity.
While PII covers personal information broadly, PHI applies only to health information created, received, maintained, or transmitted by HIPAA-covered entities or their business associates.
Context matters. PHI protections even extend 50 years after death, highlighting the long-term responsibility healthcare organizations carry.
HIPAA defines 18 identifiers that transform health information into PHI:
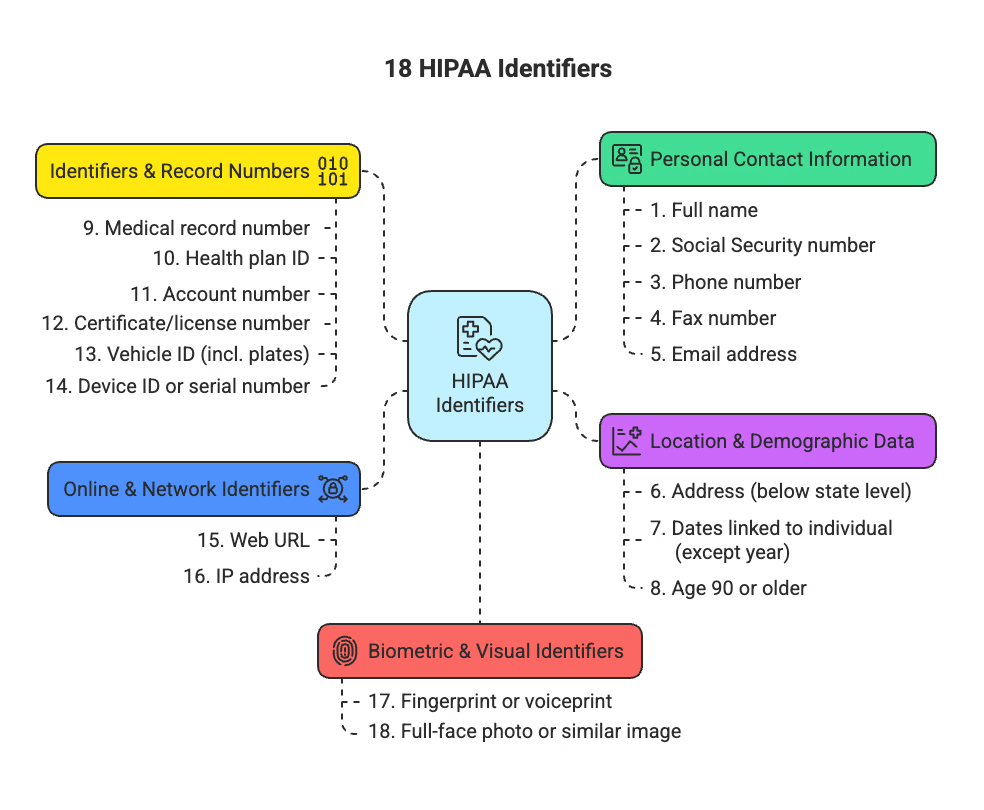
18 HIPAA Identifiers
To de-identify data, all 18 identifiers must be removed.
Electronic PHI (ePHI) is any PHI stored, received, created, or transmitted electronically. HIPAA protects it with:
Paper faxes and phone calls escape ePHI rules if the information never existed digitally.
Healthcare organizations must:
Following the HIPAA Privacy Rule restricts PHI sharing and requires patient consent for anything beyond treatment, payment, or healthcare operations.
Proper PHI handling safeguards sensitive information, preserves patient trust, and ensures healthcare operations remain secure.
Credit card fraud? Yep, it’s the #1 type of identity theft. No wonder PCI (Payment Card Industry) data security keeps business owners up at night. The PCI full form — Payment Card Industry — matters because it defines the exact scope of data the standard protects.
PCI stands for Payment Card Industry — basically, every organization that touches payment card information. The big credit card companies teamed up and formed the PCI Security Standards Council (PCI SSC), creating the PCI Data Security Standard (PCI DSS) to set the baseline for protecting payment data.
Think of PCI DSS as the ultimate rulebook for keeping payment environments secure. But here’s the catch: it’s not enforced by the government. Instead, payment brands and acquirers decide compliance based on contracts with merchants and service providers.
PCI DSS 4.0 dropped in March 2022, and it’s tougher than ever. It focuses on six key areas:
On top of that, organizations now need controls for payment page scripts, automated web application solutions, enhanced monitoring, and targeted risk analysis.
PCI data splits into two buckets:
Cardholder Data (CHD)
Sensitive Authentication Data (SAD)
Here’s the golden rule: you can store cardholder data if it’s protected properly. Sensitive authentication data? Never store it after authorization — unless you’re the card issuer.
PII and PCI often overlap, especially during payments. The difference comes down to context:
PCI data gets stricter treatment because it’s tied to money. When personal info mixes with payment details, treat it as one protected dataset.
Your customer’s name on a driver’s license? That’s PII. The same name on a credit card? Now it’s PCI data. Boom — context matters.
Most people get this wrong: they think PII, PHI, and PCI are just about the data itself. It's not. It's about context — and context changes everything.
The exact same information can flip between PII and PHI depending on where it lives:
Context matters: 75% of organizations that classify data correctly spot misuse within minutes. The rest? They wait days (43%) or even months (29%) to catch problems.
All PHI counts as PII, but not all PII becomes PHI. PHI requires:
PCI data is basically PII with a payment twist. Key differences:
Organizations struggle because:
The solution? Automated discovery tools that label data consistently, no matter where it goes. Getting classification wrong isn’t just a compliance issue — it’s a business killer.
Here’s a quick summary to visualize the differences:
| Aspect | PII | PHI | PCI |
|---|---|---|---|
| Scope | Any personal identifier | Personal health information in healthcare context | Payment card data |
| Regulations | GDPR, CCPA | HIPAA | PCI DSS |
| Examples | Name, email, phone, SSN | Medical records, health plan numbers, lab results | Credit card number, CVV, expiration date |
| Sensitivity | Low to high depending on context | Always high |
Classifying data correctly helps organizations detect misuse faster, reduce penalties, and protect both business and customer trust.
The legal world of data protection? It's messy. Really messy.
Different data types follow different rules. And those rules weren't exactly designed to play nice with each other.
HIPAA doesn't mess around when it comes to PHI. Here's what you're dealing with:
Privacy Rule: Spells out exactly when you can use PHI. Want to use it for anything beyond treatment, payment, or healthcare operations? You better get authorization first
Security Rule: Demands you lock down electronic PHI with administrative, physical, and technical safeguards
Enforcement: Penalties start at USD 100 and go up to USD 50,000 per violation. Repeat offenders? You're looking at USD 1.5 million annually
PHI remains protected for 50 years after death.
Both want to protect PII. But they couldn't be more different in approach:
GDPR (The European Approach):
CCPA (The California Way):
PCI DSS governs organizations handling payment card information. Here's what you need to know:
No government agency enforces this. It's all contractual agreements between payment companies and merchants
Here's where things get really fun. Multiple frameworks often apply to the same data:
Bottom line? You need a strategy that handles overlapping requirements without losing your mind.
Because compliance isn't just about checking boxes. It's about staying in business.
Look, data breaches cost an average of USD 4.40 million per incident. That's not pocket change. So how do you stop your organization from becoming the next headline? Here's what actually works to protect your PII, PHI, and PCI data.
Tokenization is like giving hackers fake IDs instead of the real thing. It replaces sensitive data with worthless tokens that have zero exploitable value.
Why tokenization rocks:
Format-preserving tokenization keeps data usable for systems but useless for attackers. Masking and encryption protect data at rest, in transit, and in use, making breaches far less damaging.
Most organizations mess up access control. Identity and access management should:
Use conditional IAM policies that grant or deny access based on data sensitivity. Permissions adjust automatically when sensitivity changes. Monitoring and auditing access regularly ensures no one accumulates excessive privileges.
Legacy tools miss 60–80% of sensitive data — like a security guard asleep on the job. You need:
Audit trails track who did what, when, and where — like security camera footage for your data.
They provide:
Employees can be your weakest link or strongest defense. PCI compliance training ensures everyone knows how to handle payment data. Cover:
Multi-layered protection isn’t optional anymore. Pick the right tools, train your teams thoroughly, and stay vigilant. The cost of doing nothing? Far higher than acting proactively — financially, legally, and reputationally.
Data protection isn’t getting easier. It’s messier, more complex, and far costlier when you get it wrong. Context changes everything: a heart rate on your fitness tracker is harmless PII. The same number in a hospital file? PHI — completely different rules, completely different stakes.
Organizations that get this right don’t treat data classification as a checkbox. They see it as the foundation of trust, safety, and business integrity. PHI falls under HIPAA. Payment info is PCI DSS territory. Any personal data? GDPR and CCPA apply. Knowing these distinctions is the first step toward strong data governance.
Smart companies layer protections: encryption, tokenization, access controls, employee training, and automated discovery tools. Manual processes miss most sensitive data, leaving gaps for attackers. Hospitals, for example, face ransomware, phishing, and data theft — one-third have already been compromised.
Perfect security doesn’t exist. But understanding PII, PHI, and PCI gives you the clarity to protect what matters. Your customers trust you with their health, finances, and personal lives — a trust you prove every day.
Protect sensitive data, cut compliance headaches, and stay breach-ready with UprootSecurity — built for teams that can’t afford mistakes.
→ Book a demo today

Senior Security Consultant
| Always high (financial risk) |
| Storage Rules | Must protect per privacy laws | HIPAA safeguards: administrative, physical, technical | PCI DSS compliance; sensitive auth data must not be stored post-authorization |
| Risk of Breach | Identity theft, fraud | Patient safety, legal penalties | Financial theft, fraud |