0%
Ever wonder why some companies breeze through SOC 2 audits while others scramble at the last minute? The difference isn’t luck or auditor leniency—it’s how seriously they manage SOC 2 risk from the start.
Most organizations treat SOC 2 like a yearly fire drill: evidence is gathered in a rush, teams work in silos, and everyone hopes the auditor won’t dig too deep. That approach doesn’t reduce risk—it just hides it until audit day.
Real SOC 2 risk management changes that. It transforms scattered security data into structured, measurable controls. Auditors see clear evidence instead of last-minute explanations, and stakeholders gain confidence that risks are actively addressed, not ignored.
The benefits go beyond passing an audit: fewer surprises, faster reviews, and far less stress during compliance season. When SOC 2 risk is managed continuously, compliance becomes a proactive advantage rather than a recurring scramble.
SOC 2 risk management is the structured approach to identifying, evaluating, and controlling risks that could impact an organization’s ability to meet the Trust Services Criteria. Rather than reacting to isolated security issues, it focuses on understanding how threats affect systems, data, and customer trust, and then addressing those risks through clearly defined controls.
This process is anchored in the AICPA’s Trust Services Criteria. Security is mandatory for all SOC 2 reports, while Availability, Processing Integrity, Confidentiality, and Privacy are included based on business relevance. SOC 2 risk management ensures these criteria are selected deliberately and that risks tied to each area are assessed consistently, not based on assumptions or audit pressure.
Effective SOC 2 risk management blends context with evidence. Interviews, process reviews, and system knowledge provide qualitative insight, while vulnerability data, incident history, and monitoring metrics add quantitative clarity. By reassessing risks regularly, organizations maintain control effectiveness throughout the audit period and reduce surprises during SOC 2 evaluations.
The Trust Services Criteria (TSC) are your roadmap for SOC 2 success. Created by the AICPA, these five criteria provide a clear structure for measuring what matters in your security controls. They guide auditors and stakeholders to see exactly how your systems protect data and deliver reliable services.
Wondering where risk assessment fits? Look at the CC3 criteria family. It has four key parts that define how organizations identify, analyze, and respond to risks:
Document your risk assessment process clearly. Capture how you categorize risks, the scales for likelihood and impact, and link each risk to controls. Many companies lean on frameworks like ISO/IEC 27001:2022 or NIST-800 to keep this organized and auditable.
Security is your starting point. Every SOC 2 report includes it, regardless of company size or industry. It’s broken into nine control families:
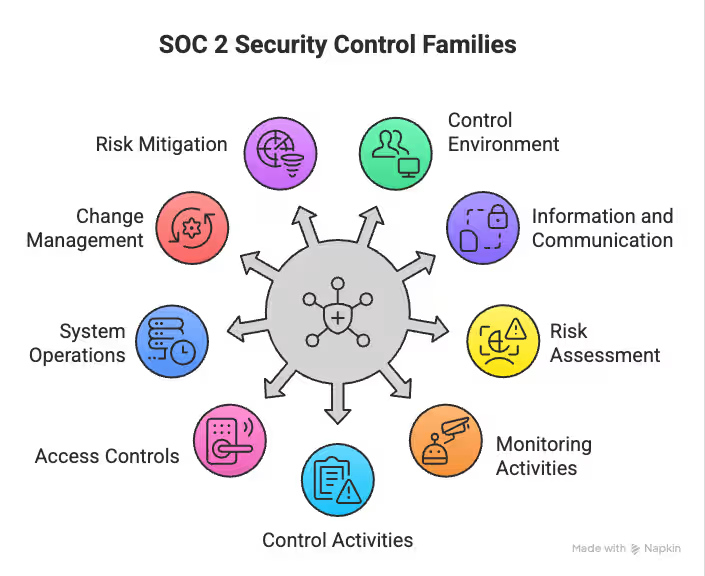
SOC 2 Security Control Families
Pro tip: Build multiple controls for each family. One control failing shouldn’t derail your audit.
Beyond Security, add criteria that actually fit your business and your clients’ expectations:
Availability: Essential if outages would block customers from critical services—think disaster recovery, SLAs, and capacity planning.
Confidentiality: Protect sensitive business data like financials, IP, contracts, and strategic documents.
Privacy: Required if you collect, store, or process personal information—names, addresses, financial details, health records. Aligns with privacy regulations like HIPAA.
Processing Integrity: Needed if your services process data where accuracy matters—payment platforms, analytics services, or document production.
Don’t just check all five because you can. Choose the criteria that align with your operations and your clients’ expectations. This ensures risk management is meaningful, auditable, and actually protects your business.
SOC 2 risk assessments aren’t typical security reviews. They require structured documentation, clear ownership, and ongoing validation. Skip any of these, and the gaps surface quickly during an audit. Done right, a SOC 2 risk assessment connects business commitments to measurable controls that stand up to scrutiny.
At a high level, conducting a SOC 2 risk assessment comes down to three steps:
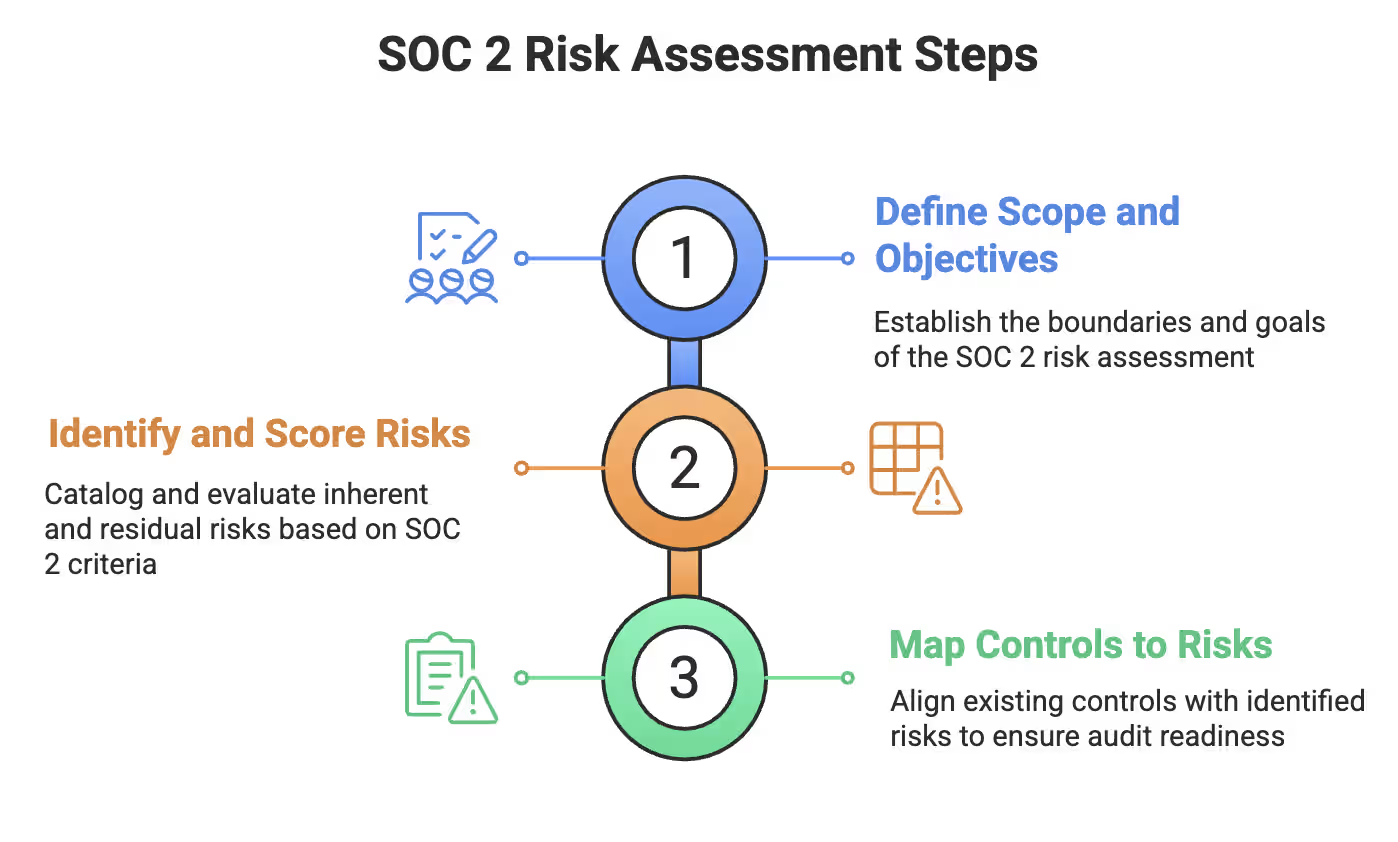
SOC 2 Risk Assessment Steps
Let’s break down each step.
Start with your Principal Service Commitments and Requirements (PSCRs)—what you’ve promised customers. Focus on real, documented obligations, including:
Next, define what falls within scope so your assessment reflects actual operations:
Get scope wrong, and everything else falls apart. Clear PSCRs and defined boundaries keep the assessment focused and defensible.
SOC 2 risk assessments distinguish between two risk types:
Move beyond vague ratings by using measurable techniques:
Quantified risk removes guesswork and makes prioritization clear for auditors and teams alike.
Once risks are scored, map each one to specific controls that mitigate it:
Done well, control mapping turns SOC 2 from last-minute panic into continuous, audit-ready risk management.
Your SOC 2 risk register is your security GPS, showing where risks exist, their severity, and who’s accountable. Most companies misuse them, but a proper register stays current, links risks to real controls, and provides auditors clear, evidence-backed visibility.
A risk register that actually works includes only what matters and nothing auditors can poke holes in:
Organizations with structured risk registers move through audits 40% faster and avoid last-minute control gaps. More importantly, teams understand why controls exist—not just that they do.
Risk ownership isn’t about task execution. It’s about accountability. Every risk needs someone who:
Reviews should follow risk level, not convenience:
Frequent reviews reduce audit stress and surface issues early.
Templates eliminate chaos and speed up audits by standardizing how risks are evaluated and documented:
Templates turn scattered findings into audit-ready documentation. Keep the register simple, keep it updated, and keep every risk tied to controls that actually work.
Here’s a stat most teams underestimate: nearly 98% of organizations experience vendor-related breaches. That’s not an edge case—it’s a pattern. SOC 2 treats vendors as part of your risk surface, requiring continuous assessment, monitoring, and audit-ready evidence.
Not all vendors carry the same risk. Treating them equally creates blind spots.
Most SOC 2 programs tier vendors based on access and business impact:
High-risk vendors: Direct access to production systems or customer data, infrastructure providers, security vendors
Medium-risk vendors: Internal SaaS tools and development platforms with limited access
Low-risk vendors: No sensitive data handling or system access, with documented justification
Start with a complete vendor inventory. Pull from contracts, finance systems, access logs, and data-flow diagrams. This step alone often reveals vendors teams forgot were in scope—but auditors won’t.
Vendor assessments should be structured, repeatable, and audit-ready.
A solid SOC 2 vendor risk assessment template includes:
Verification matters more than assurances. Always review current vendor SOC 2 reports—especially Type 2, which proves controls operate effectively over time, not just on paper.
SOC 2 explicitly ties vendor oversight to risk management.
Auditors focus on:
CC3.2: Identifying risks across the organization, including vendor-driven threats
CC3.4: Assessing changes that could impact internal controls, such as new vendors or expanded access
CC9.2: Defining vendor requirements, monitoring performance, and remediating issues
These controls show vendor risk is actively managed—not passively documented.
If vendors handle personal data, privacy obligations are mandatory.
Under P6.5, vendors must notify you of actual or suspected incidents involving personal information. Contracts should enforce:
Because when a vendor fails, accountability—and audit impact—still sits with you.
Most companies drown in spreadsheets for SOC 2: manual risk tracking, endless vendor questionnaires, and last-minute evidence hunts. Automation flips this, cutting audit prep 40% and saving 75% of compliance time.
Think of a centralized vendor repository as your compliance command center. Everything in one place: vendor details, service descriptions, and risk classifications—all audit-ready. Modern platforms handle the heavy lifting:
No surprises, no missed renewals, no panic.
Automation eliminates tedious compliance work. The platform handles:
The result: risk scores, control mapping, and evidence collection happen automatically while your team focuses on priorities that actually matter.
Modern platforms aren’t just digital checklists—they integrate with your tech stack to:
SOC 2 stops being an annual panic and becomes part of daily operations.
Type 2 audits separate the pros from the amateurs.
Type 1 checks if controls look good on paper. Type 2 watches them work every day for months, catching cracks and gaps. No shortcuts, no luck—only consistent, proven performance counts.
Here’s what changes between the two:
Think of Type 1 as a photo. Type 2? A full-length documentary showing performance over time. Proper planning starts with understanding these differences.
Controls must operate every day, not just when auditors arrive.
Auditors examine your entire observation period, so consistency is everything. Daily monitoring and proper documentation keep surprises at bay.
Most companies trip over these:
Invest in a thorough readiness assessment. Fix problems before auditors arrive, not during. Doing so turns a stressful audit into a predictable, manageable process.
Stop treating SOC 2 like a once-a-year headache. Companies that get it right turn compliance into a competitive edge—faster audits, less busywork, and stakeholders who actually trust their processes.
The secret is making SOC 2 ongoing, not a sprint. Smart organizations build systems that operate year-round. Control mapping becomes automatic, monitoring never stops, and evidence collection happens seamlessly, without constant manual effort.
Start with Security (Common Criteria)—it’s non-negotiable. Include other criteria only if they align with your business. Keep a structured risk register with clear owners, monitor vendors closely, and understand the difference between Type 1 and Type 2. Type 2 proves that controls work consistently in real-world conditions.
Automation transforms the game. Teams using platforms reduce assessment time from weeks to days, cover nearly all vendors, and scale efficiently. Use templates, assign ownership, review regularly, and SOC 2 stops being reactive firefighting—it becomes proactive protection that keeps auditors happy and builds real customer trust.
Turn SOC 2 risk management into an advantage—not a scramble. UprootSecurity helps you manage assessments, vendors, and Type 2 readiness with continuous, audit-ready controls.
→ Book a demo today

Senior Security Consultant