0%
Ever wondered why companies keep getting burned by their vendors?
You outsource to save money, cut costs, and get expertise you don’t have in-house. Makes sense, right? But here’s the thing nobody tells you: every vendor you bring on board becomes a potential backdoor into your business.
When vendor risk management goes wrong, you get hit hard: data breaches, system crashes at the worst possible time, regulators breathing down your neck, customers losing trust, supply chains falling apart. Ouch.
The numbers don’t lie. During the pandemic, EY found the percentage of third parties actually assessed by organizations dropped big time. Companies got sloppy. And it shows.
But when you get it right, it’s a different story: fewer headaches, operations that actually work, regulators leaving you alone, customers trusting you with their data, vendors delivering on promises, and money saved from avoiding disasters.
TPRM isn’t a checkbox. It’s your safety net.
Third-Party Risk Management (TPRM) is the process of identifying, assessing, and managing the risks that come from working with external vendors or service providers. It ensures your business stays secure, compliant, and operational, even when you rely on third parties.
Vendors touch everything: IT systems, software, supply chains, customer support. They have access to your data, your customers, and your operations. One mistake on their end, and the blame lands squarely on you.
Not all vendors are equal. Some are low risk — your office supplies provider probably won’t sink your business. Others are high risk — think payment processors or SaaS providers with access to sensitive data. Smart companies classify vendors by risk level, then act accordingly.
Modern TPRM programs don’t rely on spreadsheets. They use 3rd party risk management software to automate assessments, centralize vendor data, and alert you when something’s off.
Done right, TPRM turns potential disasters into managed partnerships, letting you reap the benefits of outsourcing without lying awake at night.
Third-party relationships are like letting strangers into your house. They might fix your plumbing, but they could also steal your stuff, burn the place down, or bring in sketchy friends.
87% of firms have had a third party mess up operations, and 11% experienced complete vendor relationship failures. These aren’t “could happen” numbers — this is happening right now.
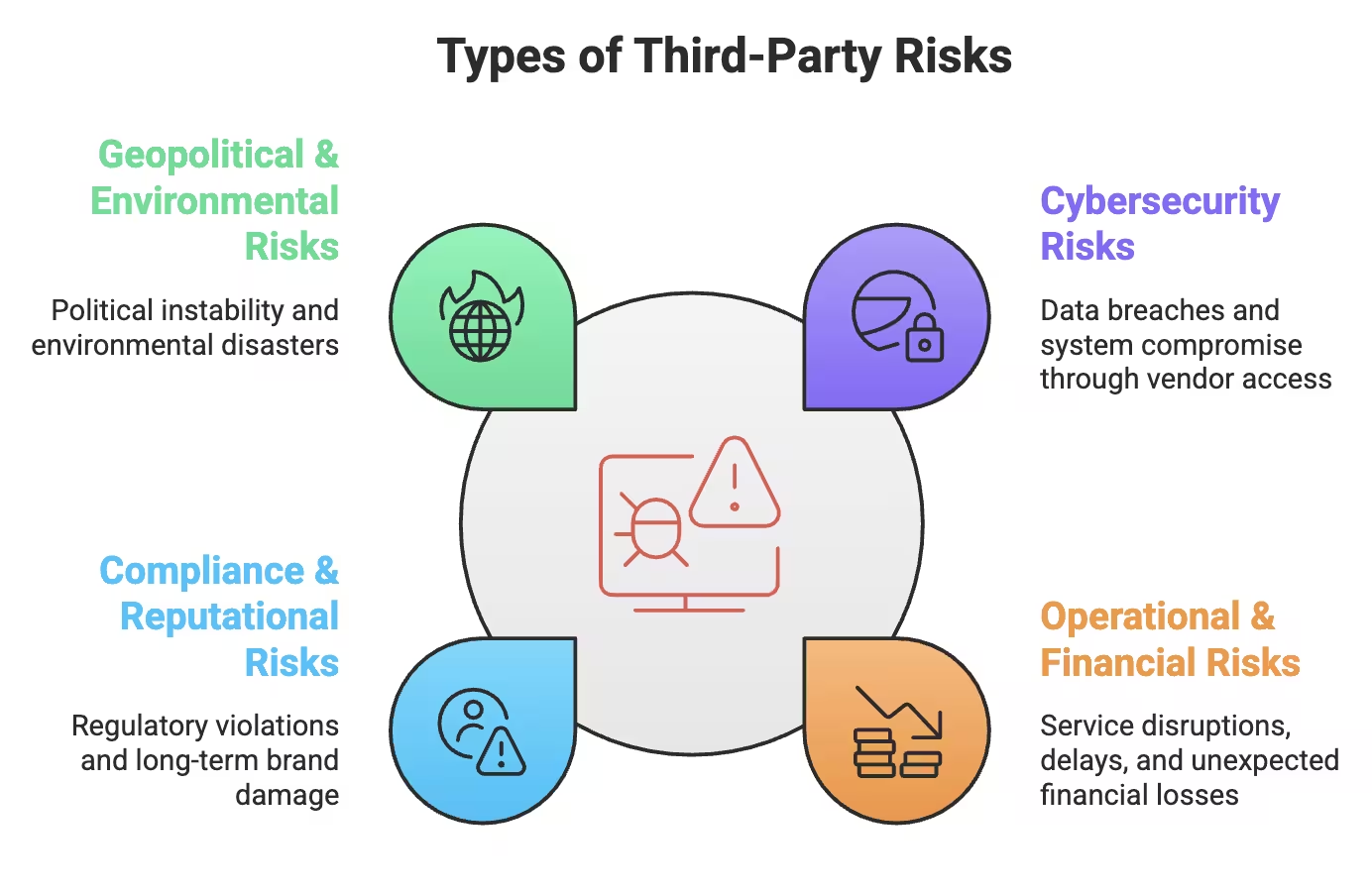
Types of Third-Party Risks
Cybersecurity risk happens whenever a vendor has access to your systems, data, or networks. Even trusted partners can have weak controls, outdated software, or careless employees — all of which make them easier to hack than your main defenses.
Three out of five data breaches start with vendors, not employees. In 2022, 49% of organizations faced vendor-caused breaches, averaging $9.44 million in losses. The 2023 LockBit attack exploited “CitrixBleed” vulnerabilities in widely used network devices, proving one weak vendor can compromise your entire business.
Operational and financial risks appear when a vendor can’t deliver reliably — because of bankruptcy, staffing issues, or supply chain failures.
Failures ripple across your business: delayed deliveries, lost revenue, angry customers, and emergency costs. Smart companies classify vendors by risk and plan contingencies. Low-risk vendors (office supplies) need minimal oversight, while high-risk vendors (payment processors, cloud providers) demand close monitoring.
Compliance risk exists because your company remains liable for regulatory violations, even when you outsource. GDPR, CCPA, or ethical sourcing breaches by a vendor hit both your bottom line and your brand.
Reputational risk follows fast. Customers rarely blame the supplier; they blame you. One vendor’s unethical practices — forced labor, deforestation, or data mishandling — can instantly tarnish your brand.
Global supply chains are vulnerable to political instability, trade conflicts, extreme weather, and economic slowdowns. These events can disrupt vendors and cascade through your operations.
Smart supplier risk assessment plans for these domino effects. Classifying risks, building redundancy, and preparing contingencies ensures one problem doesn’t spiral into a full-blown crisis.
Third-party risks aren’t hypothetical — they’re happening now. Knowing the types of risks is just step one. The real work starts with assessing, monitoring, and managing vendors before one misstep becomes your next big headache.
Managing vendors isn’t a one-and-done deal. It’s more like maintaining a car — ignore it, and you’ll break down when you least expect it. Smart companies handle the entire vendor lifecycle without losing their minds.
These are the key steps in the TPRM lifecycle:
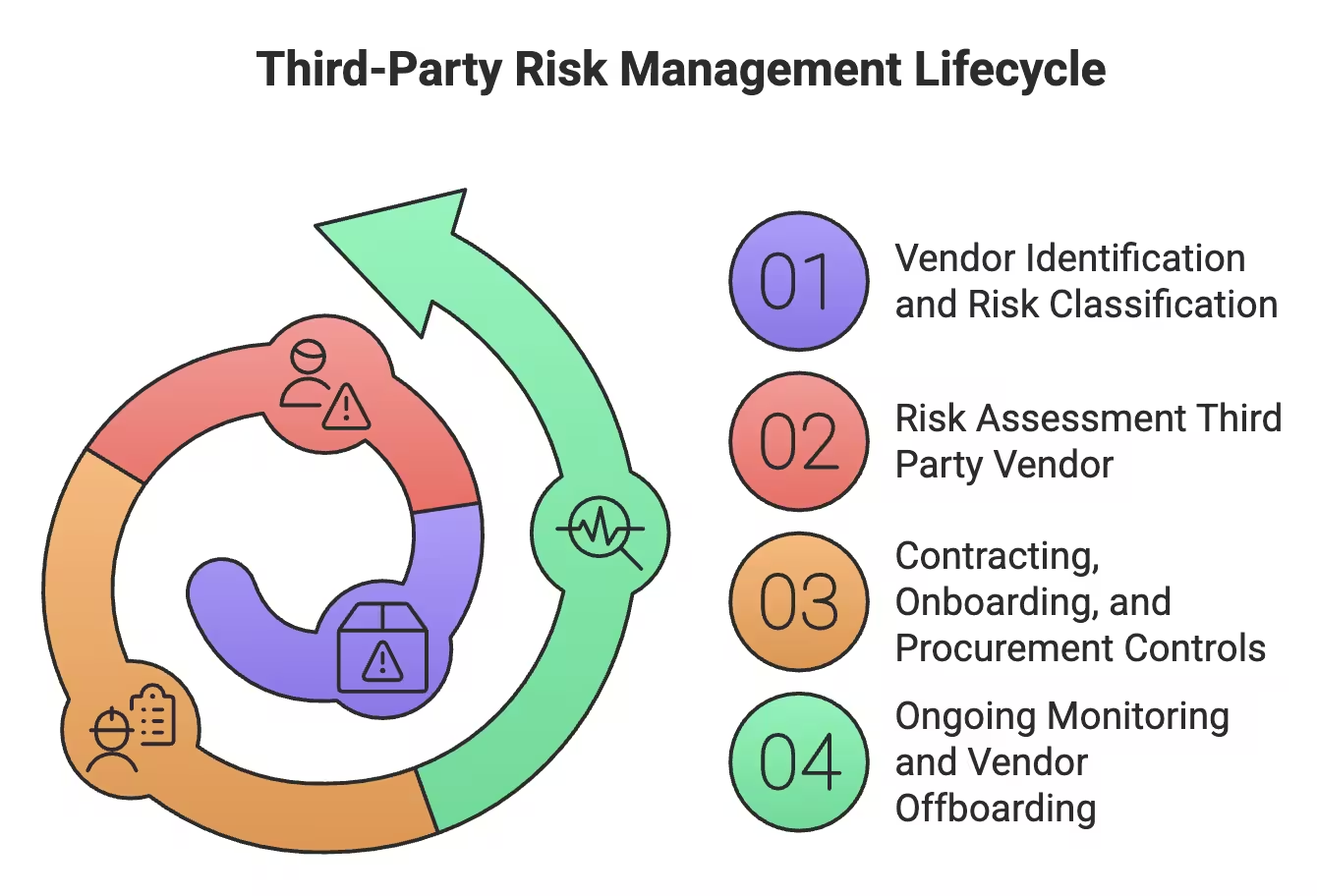
Third-Party Risk Management Lifecycle
Let’s get into each of these steps and see how companies manage vendor risks effectively.
Not all vendors are created equal. Some have the keys to your kingdom; others barely touch critical systems. Smart companies sort vendors into tiers:
This isn’t just bureaucracy. It ensures you’re spending time and resources based on real risk, not treating your coffee supplier like your cloud hosting provider.
Due diligence isn’t optional — it’s insurance. Examine security policies (ISO 27001, NIST), compliance certifications (SOC 2, PCI DSS), and data handling practices. Dig deeper: incident response, breach history, financial stability, and other vendor dependencies.
Think of it like hiring an employee. You wouldn’t skip references, and you shouldn’t skip this. A thorough assessment shows which vendors can deliver on contracts, especially for long-term projects.
Contracts aren’t just legal paperwork — they’re your safety net. Include data protection standards, audit rights, incident reporting, and compliance obligations. Make expectations crystal clear.
During onboarding, build a complete vendor profile: security protocols, access requirements, and risk mitigation strategies. Embedding safeguards in contracts ensures third parties follow regulations and standards from day one.
Set-and-forget doesn’t work. Conduct regular audits, track KPIs and SLAs, and use automated 3rd party risk management software for real-time alerts. Frequency depends on risk tier: critical vendors yearly, moderate every 18–24 months, low-risk every 2–3 years.
When the relationship ends, clean house. Revoke access, delete accounts, securely dispose of data, and back up what’s needed. 84% of risk executives say unchecked third-party risks can disrupt operations. Vigilance here separates companies that thrive from those surviving on luck.
Managing vendors isn’t a one-time task — it’s a cycle of identifying, assessing, contracting, monitoring, and offboarding. Get these steps right, and you turn potential headaches into smooth, secure partnerships. Ignore them, and you’re inviting trouble.
Still tracking vendors in spreadsheets? That approach doesn’t scale. Vendor ecosystems grow fast, risks grow faster, and manual tracking collapses the moment something goes wrong. This is where 3rd party risk management software becomes essential, not optional.
Here are widely used tools that help organizations manage vendor risk more effectively:
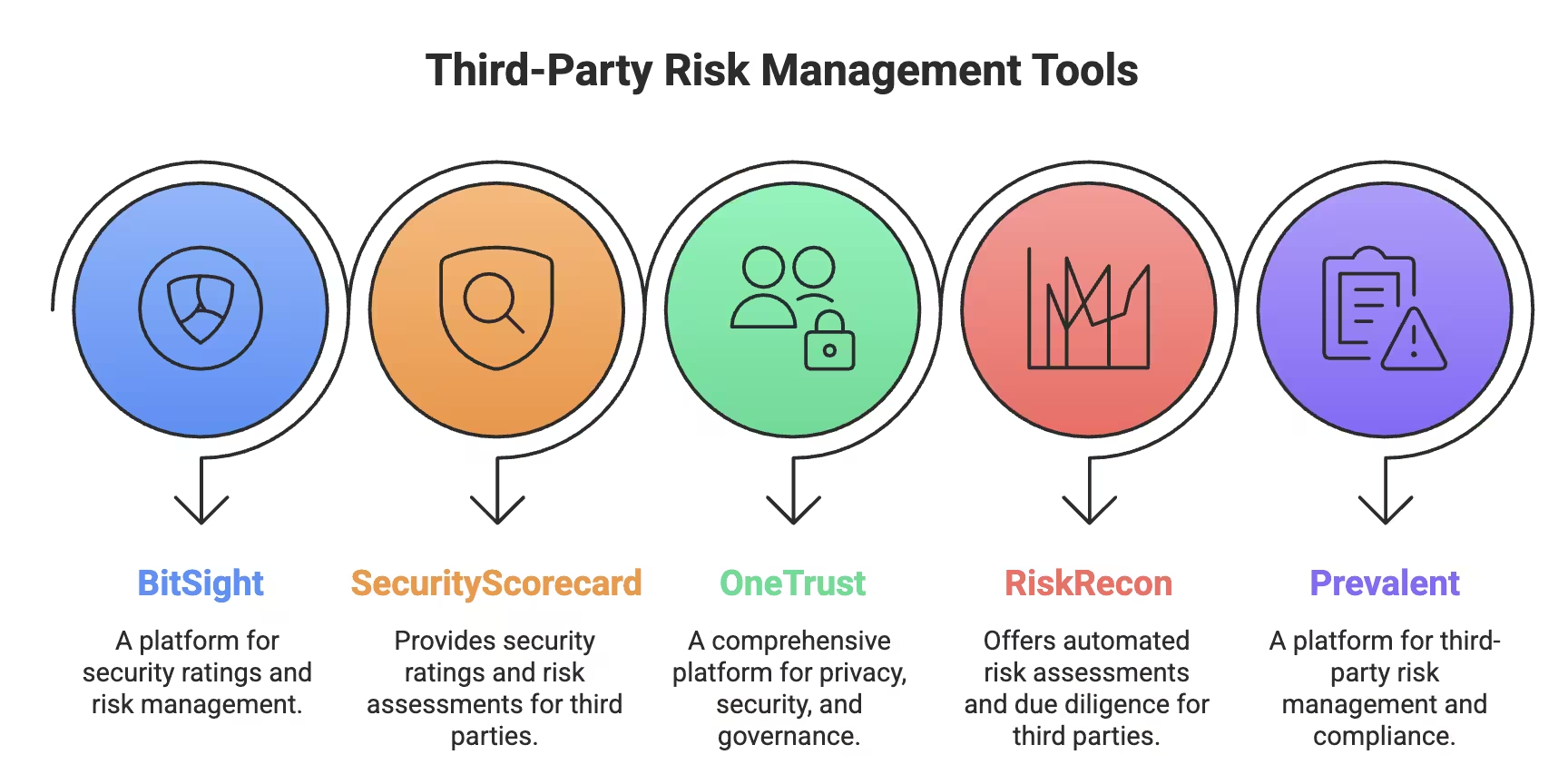
Third-Party Risk Management Tools
Let’s take a closer look at each one.
Uproot Security is a modern third-party risk management platform that brings vendor risk, compliance, and security into one workflow.
It helps teams focus on the vendors that actually matter.
BitSight vendor risk management software provides continuous visibility into vendor security using external signals and AI-driven analysis.
It replaces static questionnaires with ongoing, real-world risk insights.
SecurityScorecard turns vendor risk into simple, digestible security grades.
This makes vendor risk easy to understand across technical and business teams.
OneTrust manages the entire vendor lifecycle from onboarding to offboarding.
It brings vendor risk, compliance, and governance into a single system.
Prevalent combines automation, monitoring, and optional managed services.
It supports both growing and mature supplier risk management programs.
Together, these tools automate assessments, monitoring, alerts, and reporting. The result is less manual work, faster risk detection, and fewer blind spots. With the right platform, vendor risk becomes manageable instead of overwhelming.
Building a strong TPRM program isn’t about piling on more tools. It’s about using what you have smartly. Threats evolve, and so should your approach.
Not all vendors carry the same risk. Your coffee supplier isn’t the same as your cloud provider. Smart companies sort vendors into tiers:
Risk-based tiering ensures high-risk vendors get the scrutiny they deserve, while low-risk relationships don’t drain resources. It cuts assessment costs and focuses attention where it matters most.
Vendors shouldn’t become backdoors into your business. Key strategies:
Even if a vendor account is breached, these steps contain the damage and protect your systems.
Vendors and threats change constantly. Stay ahead by:
Monitoring continuously keeps risks visible and manageable, catching problems before they escalate.
Security shouldn’t just say “no.” It should guide safely:
Done right, TPRM strengthens operations instead of creating vulnerabilities. Vendors should empower your business, not put it at risk.
The future of vendor risk management is already here, and most companies haven’t caught up. While you’re still tracking vendors in spreadsheets, smart organizations are using AI to monitor thousands of relationships in real-time. The gap between leaders and laggards keeps widening.
Modern companies rely on the best vendor risk management software to automate assessments, monitor vendors, and gain real-time insights. Manual vendor assessments are becoming a thing of the past. Natural language processing pulls risk indicators from contracts, policies, and vendor documentation, while machine learning identifies patterns across thousands of assessments to improve accuracy. AI-powered onboarding cuts vendor onboarding time by 40–50% and covers over 90% of vendors, compared to 25–30% with manual methods.
Automation handles repetitive tasks like onboarding, offboarding, risk ratings, sending questionnaires, and performing assessments. This frees teams to focus on strategic decisions, while risks that could be missed manually are flagged automatically.
Regulations change constantly — ESG mandates in Europe, data sovereignty laws in Asia, and more. TPRM programs must adapt without relying on armies of lawyers. Configurable frameworks adjust automatically, automation triggers evidence collection when laws change, and audit-ready tools generate documentation with full version history.
Compliance is no longer a one-and-done checklist. Treating it as a living process allows companies to stay ahead of fines, operational disruptions, or gaps in risk management.
Vendor risk fails when departments work in isolation. Procurement, logistics, finance, and IT each bring insights that, when combined, allow companies to identify and mitigate risks more effectively. Cross-functional teams enable rapid information exchange and proactive responses.
Collaboration turns fragmented oversight into coordinated, anticipatory risk management, helping companies stay agile in a constantly evolving vendor landscape.
Bottom line: companies that adapt fast, automate intelligently, and collaborate across teams win. Everyone else gets left behind with spreadsheets.
TPRM isn’t going anywhere, and neither are the vendors trying to access your systems. The risks are real — data breaches averaging $9.44 million, operational shutdowns, and regulatory fines. But smart companies have figured it out: you don’t need perfect vendors, just ones you can trust because you’ve verified everything they do.
The best organizations treat vendor risk like business risk, not just an IT or procurement problem. They use technology to handle repetitive tasks — risk assessments, monitoring, alerts — so humans can focus on decisions that actually matter. They accept that perfect security doesn’t exist, but managed risk does.
Focus on vendors that can hurt you: payment processors, cloud providers, and software with admin access. Apply zero-trust principles, continuous monitoring, and automated workflows. Remember, three out of five breaches start with vendors, and unchecked risks disrupt operations.
Effective TPRM doesn’t eliminate risk — it makes it manageable, letting you grow your business with confidence.
Take control of vendor risk, reduce operational and compliance threats, and build trust with UprootSecurity — where GRC turns third-party oversight into real business resilience.
→ Book a demo today

Senior Security Consultant