0%
Ever wonder why some startups close enterprise deals while others get stuck answering endless security questionnaires?
Your product works. Your team delivers. But the moment security questions appear, momentum dies. PDFs pile up. Deals slow down. Confidence fades. Meanwhile, competitors with the right trust signals move faster—and win.
Enterprise buyers aren’t just evaluating features anymore. They’re evaluating risk. When trust isn’t clear, growth stalls. Sales cycles stretch. Late-stage deals fall apart. Startups hit ceilings they didn’t see coming. That gap isn’t about engineering quality or vision. It’s about credibility.
SOC 2 has quietly become one of the strongest trust signals in B2B. Not because it’s flashy—but because it removes doubt at exactly the moment buyers hesitate. When security concerns disappear, decisions move faster, conversations change, and startups stop losing momentum to trust gaps they shouldn’t have to fight.
SOC 2 is a security framework that shows how your startup actually protects customer data—not in theory, but in practice. It’s built around the Trust Services Criteria and focuses on real controls, real processes, and real evidence of how your systems operate day to day. What matters isn’t what you promise, but what you can prove under independent scrutiny.
For startups, this matters because trust doesn’t scale automatically. Early customers may take your word for it. Enterprise buyers won’t. They expect assurance backed by evidence. SOC 2 turns security from an ongoing debate into a clear conclusion. Instead of re-explaining your posture on every sales call, you point to validation that removes friction and accelerates decisions.
As you grow, risk grows faster than teams and tooling. SOC 2 gives you structure before things break. It forces clarity on ownership, access, monitoring, and response—without freezing velocity.
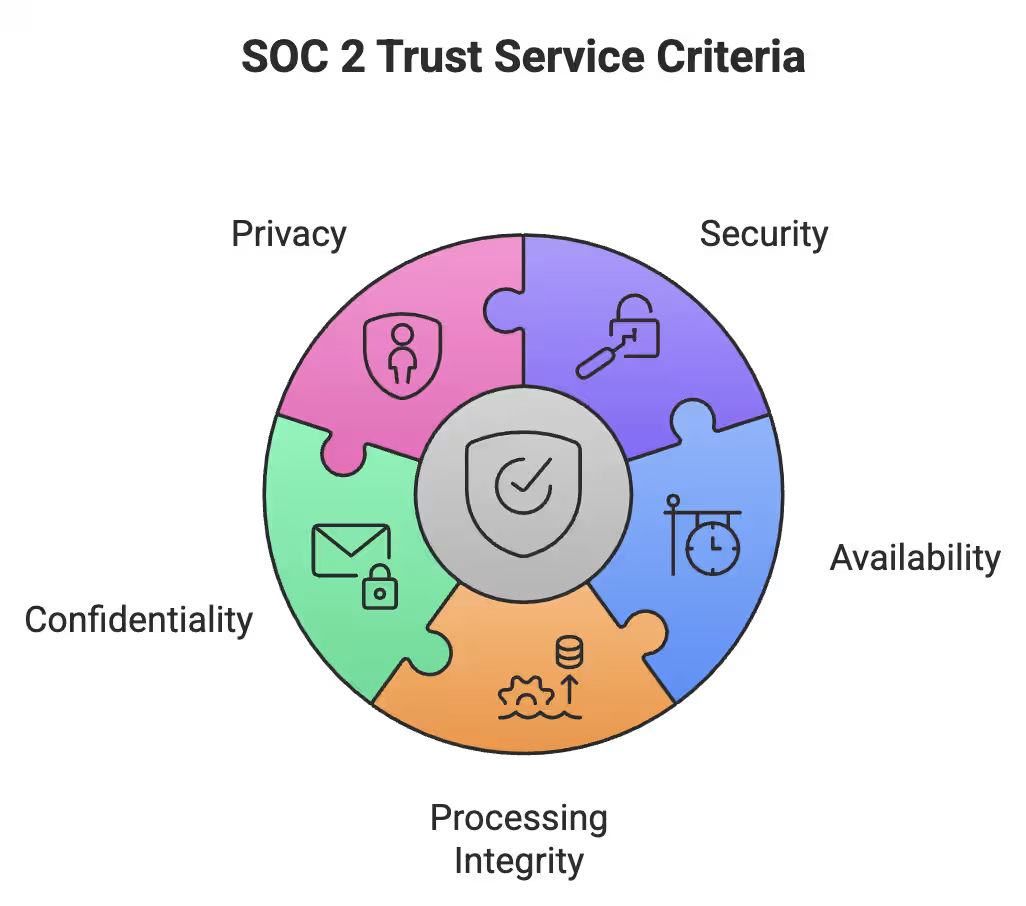
SOC 2 is built around five Trust Service Criteria that auditors use to assess how your startup protects data and operates systems. You don’t need all five. The right criteria depend on your product, data risk, and customer commitments.
Security is the foundation of every SOC 2 report. There are no exceptions.
For startups, Security proves you take data protection seriously. It’s the minimum bar for trust.
Availability comes into play when uptime is part of your promise.
Confidentiality focuses on sensitive business information.
If customers trust you with their data, confidentiality usually matters.
Processing Integrity is about correctness and reliability.
Privacy addresses personal data handling.
Not every startup needs these—but when you do, they’re non-negotiable.
SOC 2 Trust Service Criteria
SOC 2 isn’t just a checkbox—it’s a strategy. The goal isn’t to cover all Trust Service Criteria, but the ones that match your real risks. Consider the data you handle, the promises you make to customers, and contractual requirements. Over-scoping adds cost and audit friction without improving security. Focusing on the right criteria shows maturity, credibility, and that you can manage risk effectively as your startup scales.
Choosing the wrong SOC 2 type wastes time, money, and energy—and you may still fall short of what enterprise clients expect. Pick based on real needs, not prestige.
Type I is a snapshot of your controls at a single point in time. It answers one question: are your controls designed properly right now?
The SOC 2 Type I report covers:
The benefit: Type I can be completed in weeks instead of months. It’s perfect for startups needing to unblock sales conversations or show readiness quickly.
Type II evaluates whether your controls are followed consistently over 3–12 months. Think of it as checking not just the gym membership, but whether you actually work out.
The SOC 2 Type II report covers:
Enterprise clients and regulated industries prefer Type II because it demonstrates reliability and operational maturity—not just promises.
Your business model and sales priorities should guide the choice.
Most startups do Type I first, then upgrade. If enterprise deals are imminent, skipping ahead to Type II can make sense.
Type I helps close deals quickly, showing clients your controls exist and processes are in place. Type II proves those controls actually work over time, giving enterprise clients and regulated industries the confidence they require. Focus on customer expectations, contract obligations, and team capacity. Done right, SOC 2 drives growth without slowing operations.
Choose your SOC 2 type and scope based on real risk, customer needs, and team capacity. Smart scoping saves time, reduces friction, and positions your startup for secure, scalable growth.
Here’s the deal: Most startups overcomplicate SOC 2. They try to implement every control under the sun and then wonder why audits drag and costs skyrocket. Smart startups build security into operations from day one—it’s way easier than retrofitting later.
The biggest mistake? Scoping like a Fortune 500 company. Stop that. Do it right:
Startups that treat SOC 2 as more than a checkbox extract real value. Don’t just check boxes—build controls that protect customers and grow the business.
Not all controls matter equally. Focus on essentials:
Good news: you likely already have many in place. Google Workspace with MFA, weekly access reviews, quarterly incident drills—you’re halfway there.
Some startups need extra rigor:
For SaaS startups, SOC 2 is table stakes. No compliance? No enterprise deal.
Most SOC 2 guides drown you in jargon about “holistic frameworks” and “risk-based methodologies.” The reality? Startups succeed when they focus on what matters, stay organized, and demonstrate operational security to auditors and clients.
Getting audit-ready doesn’t have to be overwhelming. Focus on the essentials that matter most for startups, save time, reduce friction, and show real operational security to auditors and clients.
Key SOC 2 checklist items for startups include:
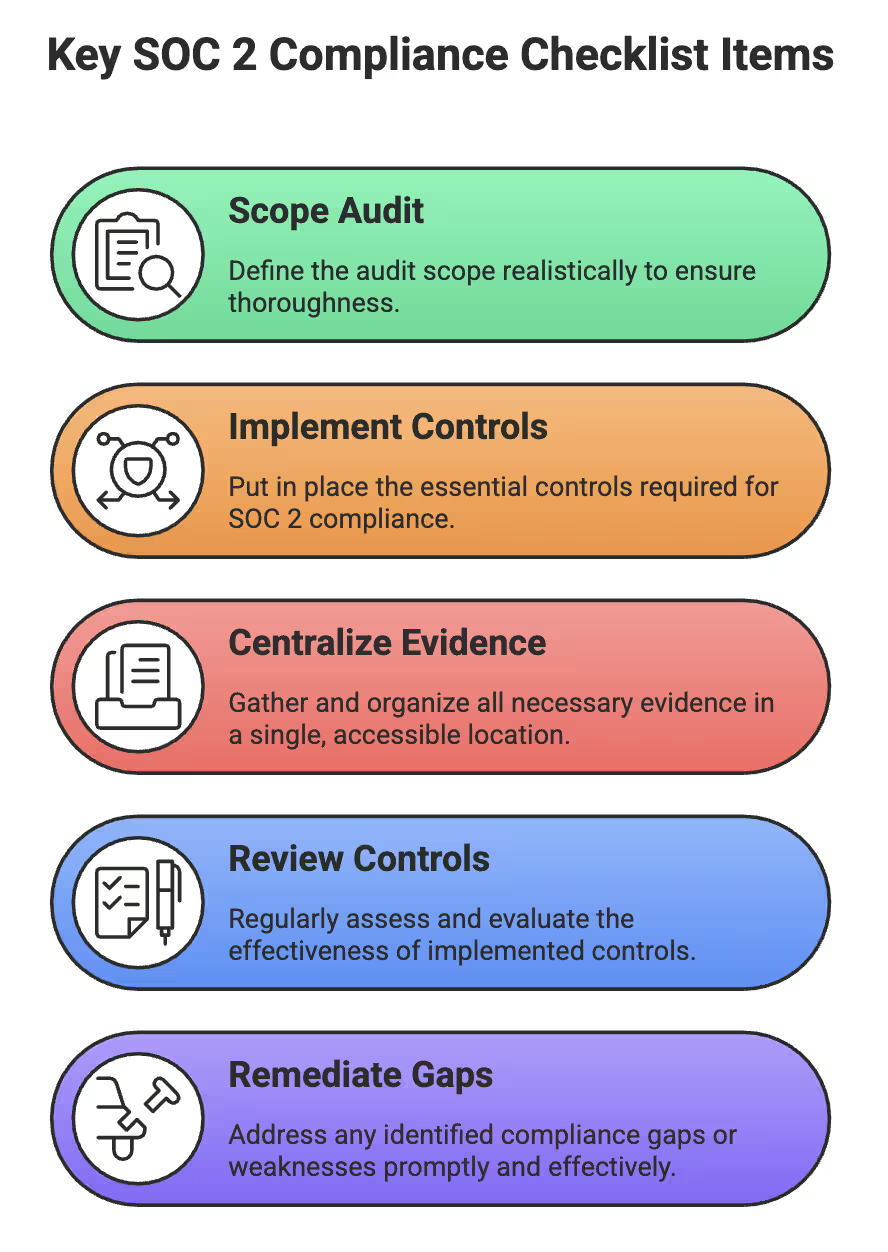
Key SOC 2 Compliance Checklist Items
This streamlined checklist keeps startups audit-ready, focused on what matters, and able to demonstrate real operational security to clients and auditors. For a ready-to-use SOC 2 Compliance Checklist PDF, check out Security Compass SOC 2 Compliance Checklist.
Getting SOC 2 ready isn’t about checking boxes—it’s a clear, repeatable process that reduces gaps and strengthens trust.
Key audit readiness steps:
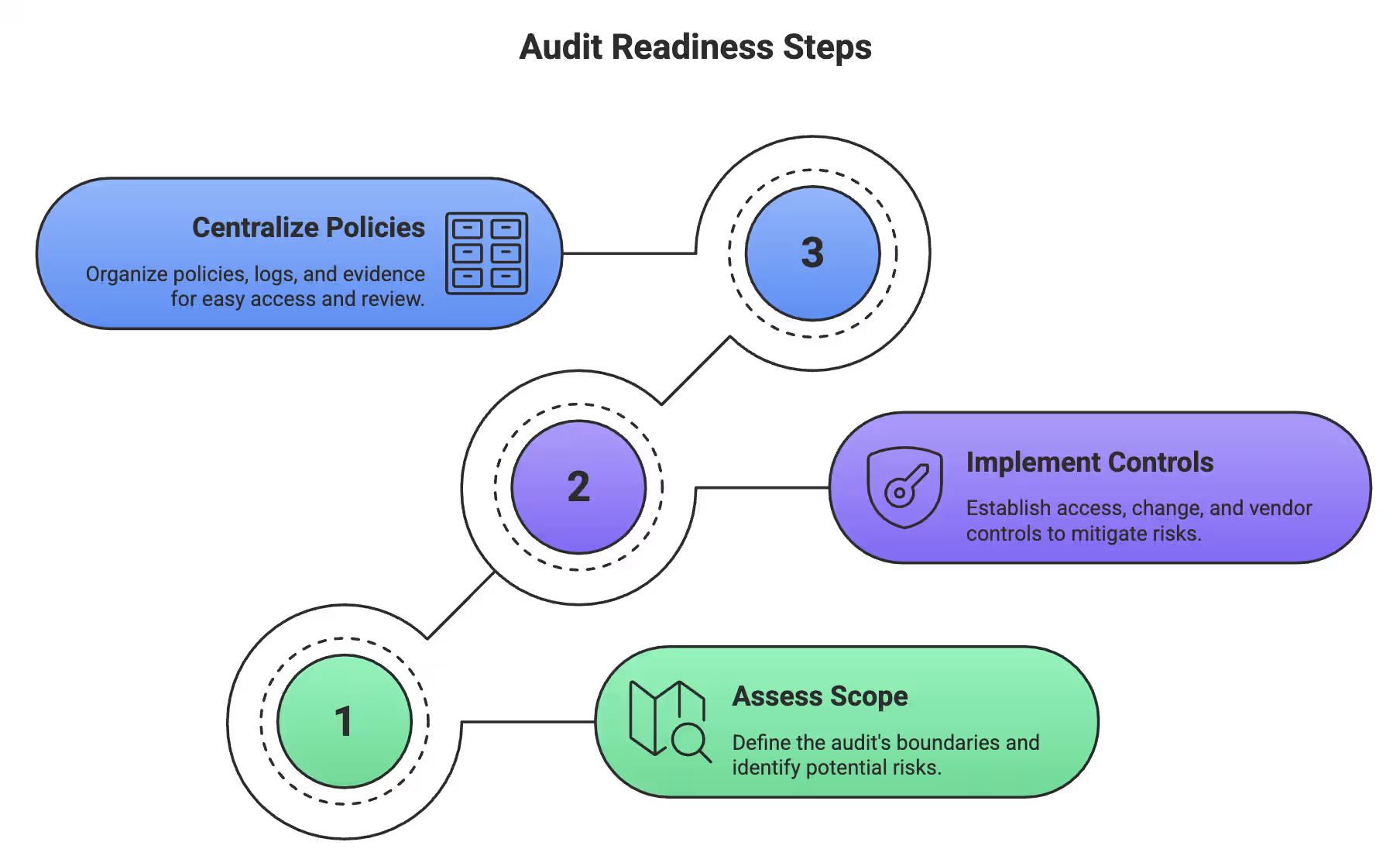
Audit Readiness Steps
Let’s get into each step.
Define system and process boundaries, identify critical vendors, and map risks for sensitive data. Prioritize remediation to focus on what truly matters and avoid wasted effort.
Enforce access controls with MFA, document and approve system changes, and continuously monitor vendor security. Turn policies into operational practices auditors can validate.
Centralize policies, procedures, and logs. Automate evidence collection, assign owners, and timestamp activities. Ensure auditors see proof, not promises, reducing friction and speeding up reviews.
Following these steps keeps startups organized, reduces surprises, and ensures controls are proven and repeatable.
SOC 2 isn’t optional for startups handling sensitive data or chasing enterprise clients. SaaS providers, cloud services, fintech, and healthcare startups usually require it. Start compliance work 4–6 months before contracts demand it, not weeks. Early planning saves time, reduces stress, and ensures readiness when auditors or clients show up.
Choosing the right auditor and compliance platform can make SOC 2 a growth enabler rather than a headache. Most founders underestimate how much smoother audits run when they align the right people, processes, and platforms from the start, making SOC 2 compliance for startups more achievable and less stressful.
Finding the right auditor is like picking a co-founder. The wrong fit costs time, money, and stress.
90% of startups report smoother audits when their auditor understands both their team and tech. Don’t underestimate cultural fit — it’s as important as credentials.
Manual audits kill time and slow growth. The right automation platforms streamline evidence collection, track controls, and keep your team audit-ready.
These platforms reduce manual work, help teams stay organized, and free founders to focus on product while maintaining SOC 2 compliance.
For startups in India eyeing global clients, SOC 2 is non-negotiable.
SOC 2 certification opens doors and builds credibility that spreadsheets and PDFs alone can’t.
Got your SOC 2 certificate? Congrats. But this isn’t a trophy to put on a shelf. SOC 2 is like a gym membership—skip the work, and the benefits fade. You need ongoing effort to keep controls effective, auditors happy, and clients confident.
Think of your controls as always-on systems, not a one-time checklist. Automated monitoring makes compliance easier and strengthens security. Key practices:
Following these practices keeps your controls reliable and reduces audit friction.
Regular check-ups keep your startup audit-ready and secure. Most startups that review controls quarterly sail through audits. Focus on:
Consistent internal audits make risk management part of daily operations.
SOC 2 certificates expire every 12 months, and each renewal gets easier with continuous practice. Remember:
Treat each recertification as a checkpoint, not a last-minute scramble.
You’ve earned your SOC 2 certification. Most founders stop there—and that’s the mistake. SOC 2 isn’t just proof that you protect data. It’s leverage. Used well, it removes friction, builds instant trust, and changes how buyers evaluate your startup from the first conversation.
Sales cycles shrink because security objections disappear early. Enterprise buyers take you seriously instead of slowing deals with endless questionnaires. Investors see operational maturity, not just product velocity. When prospects compare similar solutions, SOC 2 often becomes the deciding factor.
There’s a second benefit many teams overlook. Your SOC 2 report doubles as a security roadmap. It shows which controls matter most, where to invest next, and what not to overbuild. No guessing. No security theater. Just focused improvements that reduce risk and drive progress.
Yes, certification takes effort. But the returns compound. SOC 2 isn’t a checkbox or a cost center. It’s a signal that you’re ready to scale securely—and a competitive advantage that keeps working long after the audit ends.
Build trust, streamline audits, and keep your startup SOC 2 ready with UprootSecurity — turning compliance from a checkbox into a growth enabler.
→ Book a demo today

Senior Security Consultant