0%
Ever wonder why companies panic the moment auditors walk in?
Why compliance feels like an endless game of whack-a-mole?
Here’s the truth: most teams run security, risk, and compliance as isolated silos. Chaos follows.
Technical GRC flips that script.
Governance, Risk, and Compliance—done the technical way—aligns IT with business goals while keeping risks and regulations under control. Born from the OCEG in 2002, it’s now the integrated strategy modern organizations can’t live without.
The payoff is hard to ignore:
Instead of juggling disconnected processes, Technical GRC unites them into one streamlined framework that powers faster decisions and stronger security.
Cyber threats keep escalating. Compliance costs are set to spike 30% in the next two years. Spreadsheet-driven programs won’t survive that storm.
Technical GRC—and the analysts and consultants who implement it—deliver the automation, frameworks, and documentation that keep organizations secure, efficient, and always audit-ready.
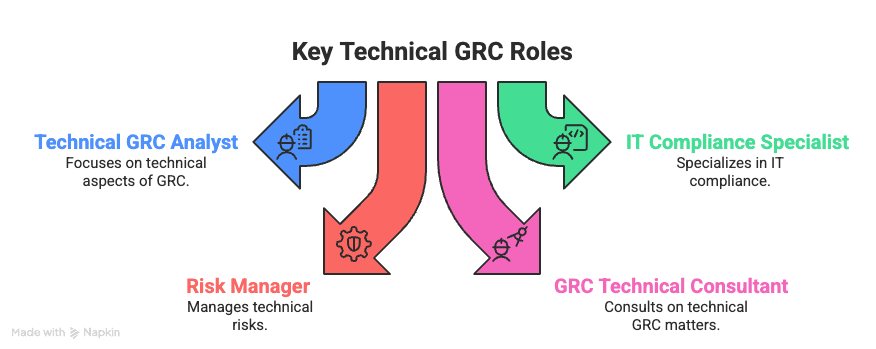
Think all GRC roles are the same? Think again. Technical GRC isn’t just about policies or checklists—it’s the bridge between regulations and real-world technology. These roles make sure organizations navigate complex rules while keeping systems secure, compliant, and resilient.
Key Technical GRC Roles
GRC Analysts operate at the strategic level, connecting business goals with compliance realities. Their core responsibilities include:
Technical GRC Analysts go deeper. They combine compliance knowledge with technical expertise. Employers increasingly demand skills in:
IT Compliance Specialists make sure systems follow security rules. Their daily work involves:
Expertise in NIST 800-171, CMMC, and NIST 800-53 is essential. Many roles also request SAP GRC knowledge for extracting audit data efficiently.
Cybersecurity Risk Managers identify, assess, and mitigate risks tied to ICT infrastructure. Once confined to IT, their impact now spans the entire business. Their main tasks include:
These consultants translate compliance requirements into actionable system-level controls.
They understand:
They don’t need to be engineers, but technical fluency builds trust with IT teams, smooths audits, and speeds remediation.
Technical GRC roles are far from one-size-fits-all. Each position brings unique skills to reduce risk, strengthen compliance, and protect systems. Organizations that leverage this expertise move from reactive security to proactive control, keeping risks low and operations safe.
Basic compliance knowledge won’t cut it anymore. The technical GRC field moves fast, and employers want skills most candidates lack. Master these, and you’ll stand out from the crowd chasing entry-level roles.
You can’t fake framework knowledge. NIST frameworks provide structured methods to identify, assess, and manage cybersecurity risks. The NIST Risk Management Framework has a 7-step process covering information security and privacy—skip learning it at your peril.
ISO 27001 sets the global standard for information security management systems. With 114 controls across 14 categories, it safeguards sensitive information and proves security commitment. Memorization won’t cut it—you must understand how controls work together.
SOC 2 demonstrates robust data security using five Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. The Security criteria alone has 265 controls against unauthorized access and breaches. Comfort with these controls is crucial.
Risk management is the backbone of technical GRC. NIST outlines five steps: identify risks, protect assets, detect attacks, respond, and recover. ISO 27001 risk assessment requires methodology definition, asset listing, threat identification, risk evaluation, and mitigation. Each step builds on the last.
Control mapping—aligning multiple regulations to a common set of controls—eliminates redundancy and gives a unified compliance view. Mastering this separates beginners from professionals.
Strong writing skills determine your career ceiling. Well-documented policies simplify audits, support controls, and meet regulatory requirements. Key documents include framework policies, detailed policies, implementation guidelines, and best practices.
Version control is essential. Without it, documents spiral into chaos, undermining credibility.
Privacy regulations are here to stay. GDPR requires Data Protection Impact Assessments (DPIAs) for high-risk processing. HIPAA’s Security Rule mandates administrative, physical, and technical safeguards for electronic protected health information, including risk analysis and documentation standards. Missing these can mean massive fines or operational disruption.
Tool proficiency is expected. ServiceNow GRC unifies risk, policy, and compliance management, integrating with ITSM/CMDB—powerful, but steep learning curve. RSA Archer aligns to NIST, COSO, ISO frameworks, enterprise-grade but complex. LogicGate Risk Cloud offers modular, no-code workflow automation—user-friendly but requires customization training.
Master these skills, and you’ll bridge the gap between compliance and practical implementation. Skip them, and competing in technical GRC will be an uphill battle.
Four frameworks dominate the technical GRC world. Master them, and you’ll speak the language every technical GRC consultant needs to know.
ISO 27001 is the gold standard for information security. Organizations implementing it properly:
ISO 27701 extends ISO 27001 with privacy-specific requirements for organizations handling personally identifiable information. Think of it as ISO 27001 with privacy superpowers, turning your ISMS into a full-fledged Privacy Information Management System (PIMS). For technical GRC professionals, these standards provide clear guidance on GRC technical specifications—no guesswork required.
The NIST Special Publication 800 series is essential for federal information system security. It includes:
FedRAMP brings these principles into cloud environments with a standardized security assessment approach. Nearly 80% of cloud providers fall into the moderate impact category. Want to work with government agencies or contractors? Proficiency in these frameworks isn’t optional—it’s mandatory.
GDPR enforces heavy penalties—up to €20 million or 4% of global revenue—for failing to protect personal data. CCPA empowers Californians to:
Technical GRC writers produce detailed data sheets documenting compliance efforts. Why? CCPA violations can cost up to $7,500 per intentional violation.
CMMC protects federal contract information with a three-tiered assessment model. Defense contractors use it to:
SOC 2 focuses on five Trust Services Criteria. The Security criteria alone has 265 controls. These frameworks give GRC professionals structured approaches to evaluate third-party security practices—no guesswork, no assumptions.
Master these frameworks, and you’ll move confidently across compliance, privacy, and vendor risk landscapes.
Think you need years of GRC experience to break in? Think again. This field is growing fast, and over 60% of professionals in GRC roles transitioned from other industries. Your existing skills matter more than you think.
Your Background Already Has What They Want
Theory only goes so far. Real exposure counts:
Show, don’t just tell:
Concrete samples beat empty promises every time.
Recruiters spend seven seconds per resume. Make each one count:
Your resume isn’t a life story. It’s your marketing pitch. Combine your background, hands-on exposure, portfolio, and a tight resume, and you’ll make a strong case—even without years in GRC.
Memorizing frameworks won’t cut it anymore. About 75% of technical GRC interviews now focus on scenario-based questions. You need to think quickly and prove you can apply knowledge in real time.
Expect curveballs such as:
Practice explaining risk matrices—impact versus likelihood—and how you prioritize remediation. Structure answers clearly: Identify, Contain, Remediate, Review.
Audit trails aren’t just paperwork; they’re proof. They record who did what and when, exposing incidents—many that begin inside an organization. Be ready to explain how logs, SIEM alerts, and retention policies help trace incidents and provide evidence for remediation and reporting.
Most companies struggle here. Break it down:
Show how these lines work together to prevent control gaps and strengthen accountability.
Focus on controls, not definitions. Map a NIST control to a business risk or align an ISO 27001 control to a specific policy and evidence artifact. Describe a remediation plan with timeline, owners, and validation steps to prove you can move from theory to action.
Interviewers want problem-solvers, not reciters. Practice scenarios, rehearse crisp examples, and show the mindset they hire for.
Technical GRC blends security, strategy, and compliance into one career path. It’s the bridge between “what could go wrong” and “how we prevent it.” Organizations everywhere need professionals who speak both tech and business, spot risks early, and act before problems explode.
Your background doesn’t have to be perfect. IT pros, legal minds, and business leaders are all breaking in. Curiosity and practical thinking matter more than credentials. If you can learn frameworks and connect dots, you’re already ahead of the game.
You’ll master NIST and ISO 27001, build a strong portfolio, and ace scenario-based interviews. Many professionals see salary bumps of 35 percent or more, especially in cloud or healthcare compliance roles where demand keeps climbing.
The real win? Becoming the person who turns complex risks into plain English and transforms compliance requirements into action. Technical GRC isn’t box-checking—it’s protecting customer data, keeping operations steady, and staying ahead of evolving threats.
Cyber risks grow every day. Companies can’t afford afterthought security. They need experts who see the big picture and execute the details. Ready to step in?
Take control of compliance, reduce risk, and build trust with UprootSecurity — where GRC becomes the bridge between checklists and real breach prevention.
→ Book a demo today

Senior Security Consultant